Intro by Andrew Morgan, Founder of Right of Boom Cyber Summit.
March 26, 2020, and July 2, 2021, are two dates that will be seen as turning points for the way managed service providers (MSPs) run their businesses.
The SolarWinds SUNBURST (2020) and the Kaseya ransomware attack (2021) put such a spotlight on supply chain attacks that both CISA and cyber insurance carriers became incredibly vocal about the massive risk managed service providers can have on their end customers. These supply chain risks were also highlighted with Exchange ProxyShell and a number of internet-facing firewall vulnerabilities with Fortinet, SonicWall and Pulse Secure.
Many MSPs are incredibly well-run, have a security-first mindset and follow frameworks and best practices, and have implemented policies to mitigate risk within their and their clients’ environments. That said, the aforementioned events created incredible hardship for many MSPs and their clients, while the MSPs themselves were held accountable for using a vulnerable third-party piece of software. As a result, their insurance premiums skyrocketed or coverage was dropped.
On average, MSPs use more than 17 applications to run their business and deliver their services. But they don’t have the internal capabilities to continuously audit the application security of their vendors, nor are vendors in the MSP ecosystem on the margin adopting application security programs like BSIMM, implementing vulnerability disclosure programs (VDPs) or offering bug bounty programs that incident security researchers to find issues within the applications MSPs rely on.
***
The State of Affairs for Security Researchers
In the security research community, we’re actually pretty ineffective at security research in regard to the tech landscape.
Why? Because as researchers, we’re heavily outnumbered by the threats out there, forcing us to pick and choose what we work on.
Aside from the true altruists in our community, many researchers are attracted to who can pay the most, either via a position on a research team or through an externally facing program that offers cash awards to those who can find the bugs (before attackers do).
These are commonly referred to as “bug bounty programs" and, as expected, the most active bug bounty programs are run by the most successful tech businesses. They get the lion’s share of the attention from the research community.
Unfortunately, that leaves a large swath of the tech landscape (small to medium-sized businesses [SMBs], state/local government, open-source software projects, etc.) left to fend for themselves since there traditionally isn't very much money—if any—to be had by finding those vulnerabilities.
Open-Source Software: An Attractive Target for Hackers
Well, wouldn’t you know it: open-source software is everywhere, and our reliance on it is at a scale that we likely didn't account for.
When we find exploitable vulnerabilities present in software as widely used as Secure Shell Protocol (SSH), Secure Sockets Layer (SSL), etc., it can cause panic because it is difficult to wrap our brains around use at that scale.
You can also guarantee that these exploits will be weaponized immediately following disclosure (via tools like Metasploit, Cobalt Strike, etc.), so due to the lack of technical skills required to operate these tools and launch such attacks, the incoming wave of activity can be overwhelming to even those with a substantial security presence.
The cleanup of one such exploit, Log4Shell (an exploit of a commonly used web server logging utility), has been referred to as “the largest mass scale cyber response in history” by Rob Silvers, undersecretary for policy at the U.S. Department of Homeland Security.
Regarding the threat itself, he asserts that
"[...] it is likely that organizations are going to be dealing with continued Log4j exposure for years to come, maybe a decade or longer."
I would posit that this is only the beginning of this type of activity, and due to the reliance on open-source software in critical infrastructure and national security systems, these supply chain attacks will only become more prevalent.
Bug Bounty Programs
In the wake of these supply chain issues, Google has announced a bug bounty program specifically for open-source software. Capitalizing on the fervor associated with these recent security events, Google aims to further incentivize security researchers in spending time investigating design issues that may lead to exploitable vulnerabilities.
Bug bounties are becoming more prevalent these days, and the amount that companies are willing to pay out keeps growing. Google paid out more than $8.7M in 2021, and Apple currently offers up to $1M for finding their most critical flaws.
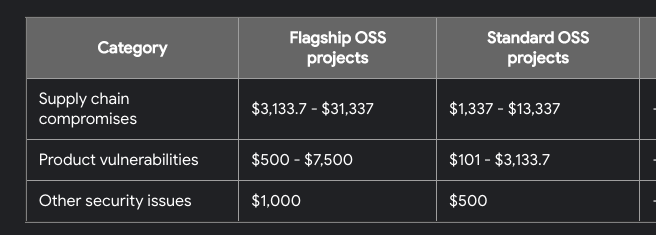
Special shout-out to Google for including hacker easter eggs in their payout matrix. Are you 1337 or are you 31337?
There are even companies out there like Hackerone and BugCrowd that enable companies that may not have the capabilities to manage their own bug bounty programs by connecting them with freelance security researchers and brokering the payout process.
It makes sense, though. The bounties paid for finding these vulnerabilities pales in comparison to the immeasurable financial disaster that an attack could precipitate.
Companies are happy to pay these relatively reasonable bounties in exchange for responsible disclosure of how the exploit works. For the security researcher, this can prove to be a very lucrative career, as we’ve seen nine individuals claim over $1M in bounties from the aforementioned bug bounty aggregator, Hackerone.
So Where Does That Leave the 99%?
There’s a problem here, though. With 99% of US businesses (~32 million) classified as “small”, most of them don't have the means to effectively manage security, let alone the resources required to manage a bug bounty program and the money to pay these bounties out. Yet they are still faced with the same cyber threats as the other 1% and, unlike those in the enterprise, are not favored to withstand the potential fallout.
To further complicate the issue, the folks that most small businesses turn to for their IT and security services, MSPs, are currently prime targets for threat actors. This is due, primarily, to two factors:
- MSPs are a single entry point for many more SMBs. As we’ve seen in the past, with such notable events as the Kaseya breach, the tools that MSPs use to provide visibility and reach across a large client base can be used against them. Even if the MSP has a comprehensive security stack and is seemingly doing all the right things, a breach can still happen, as we’ve seen in the past.
- Most MSPs are small businesses, too. Just like the SMB as a whole, there is only a small percentage of MSPs that have invested a significant amount of resources into security—and with more than half (57%) of MSPs in the US having been around for less than five years, they are prime targets for threat actors. They are more likely to be ill-equipped to handle any sort of attack from a people, process and technology standpoint, so the chances of them paying at least a portion of the ransom is high.
And that’s where the Dutch Institute for Vulnerability Disclosure (DIVD) comes in.
Earlier this year, we partnered with our friends from Appgate, Axcient, Blumira, MSPCFO, OITVoip, Servosity, Taylor Business Group and Unveil Security Group to support DIVD financially as well as create/fund a bug bounty program focused on MSPs.
The aim is to fund the payouts of these bug bounties, ensuring that they are on par with the larger programs in an effort to attract the same level of activity that is usually afforded to the larger companies only.
Hopefully, more security vendors will recognize the benefits of supporting initiatives like this. If we all pitch in, we may stand a chance of leveling the playing field in regards to everyone’s ability to respond to threats.
Learn More
If there’s one truth that has withstood the test of time in cybersecurity, it’s this: we’re better together.
That’s why we’re proud to offer the Huntress Neighborhood Watch Program: a collection of resources and programs to help elevate the broader security community—with a special focus on the 99% of businesses that are often underserved.
















