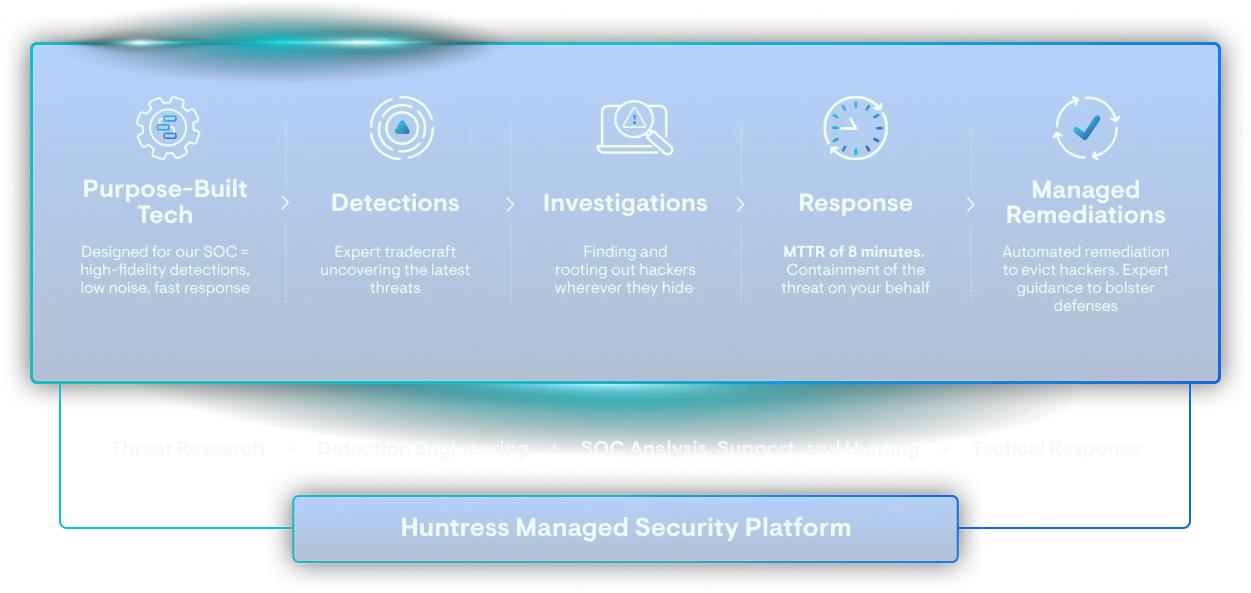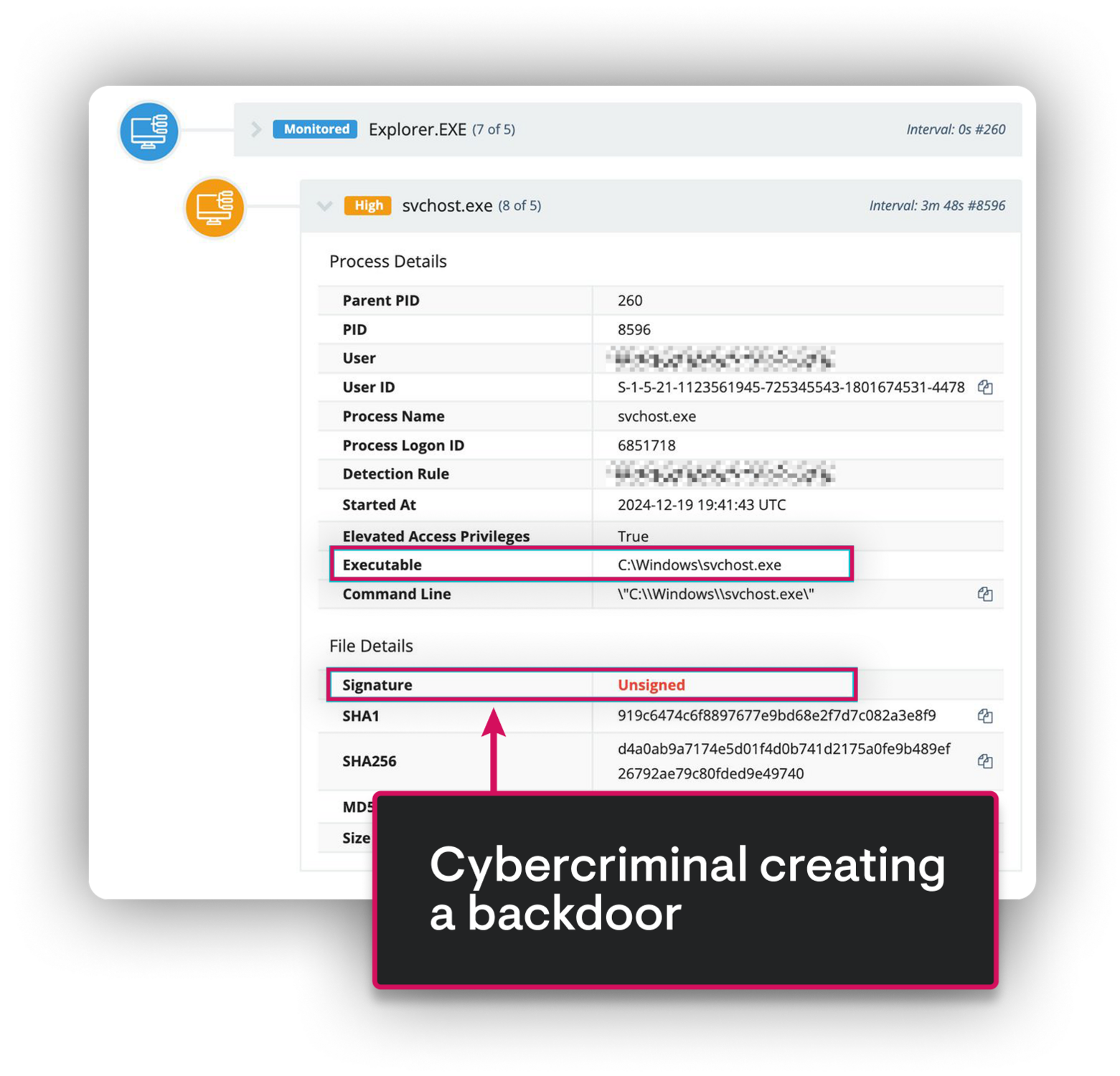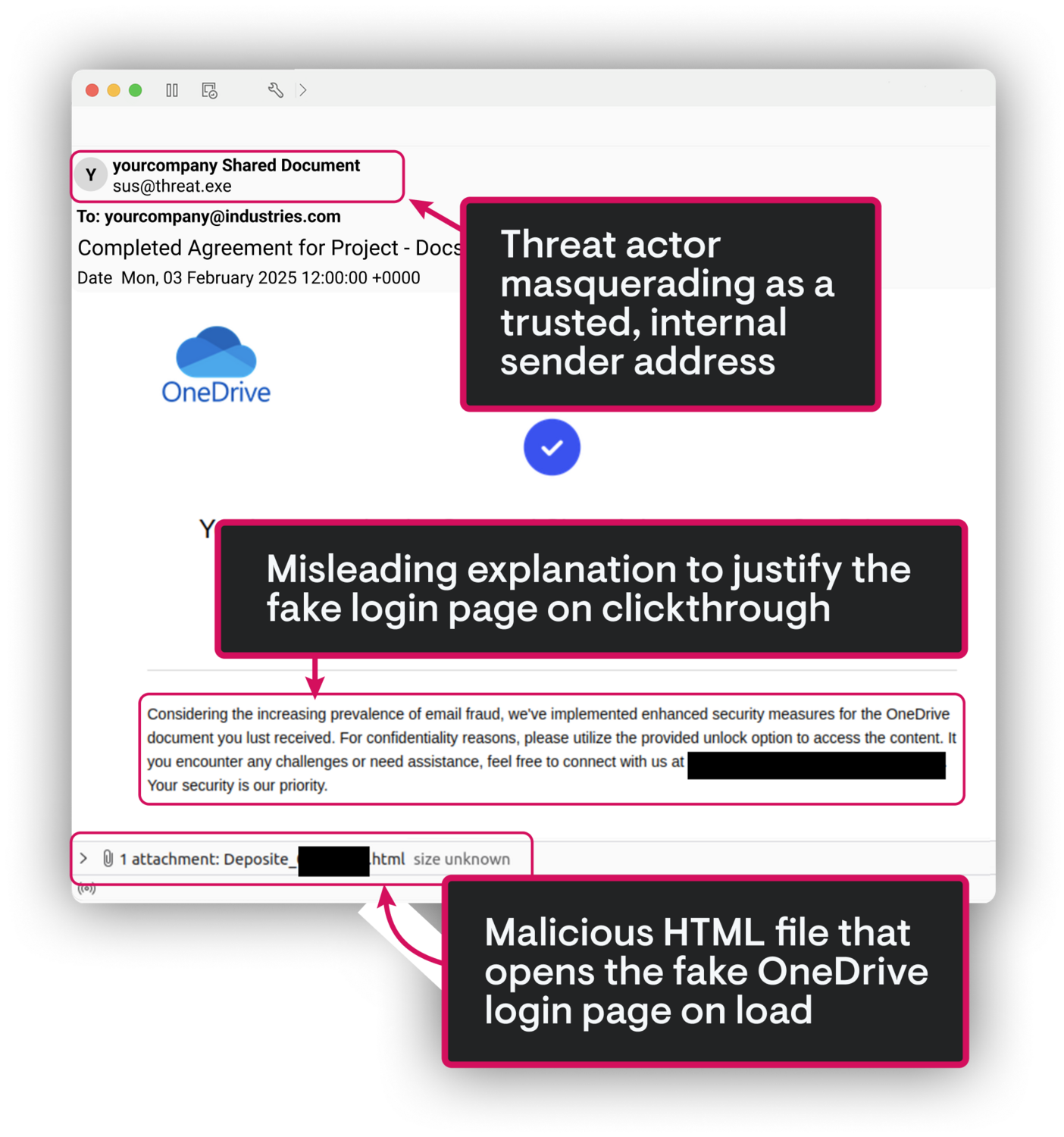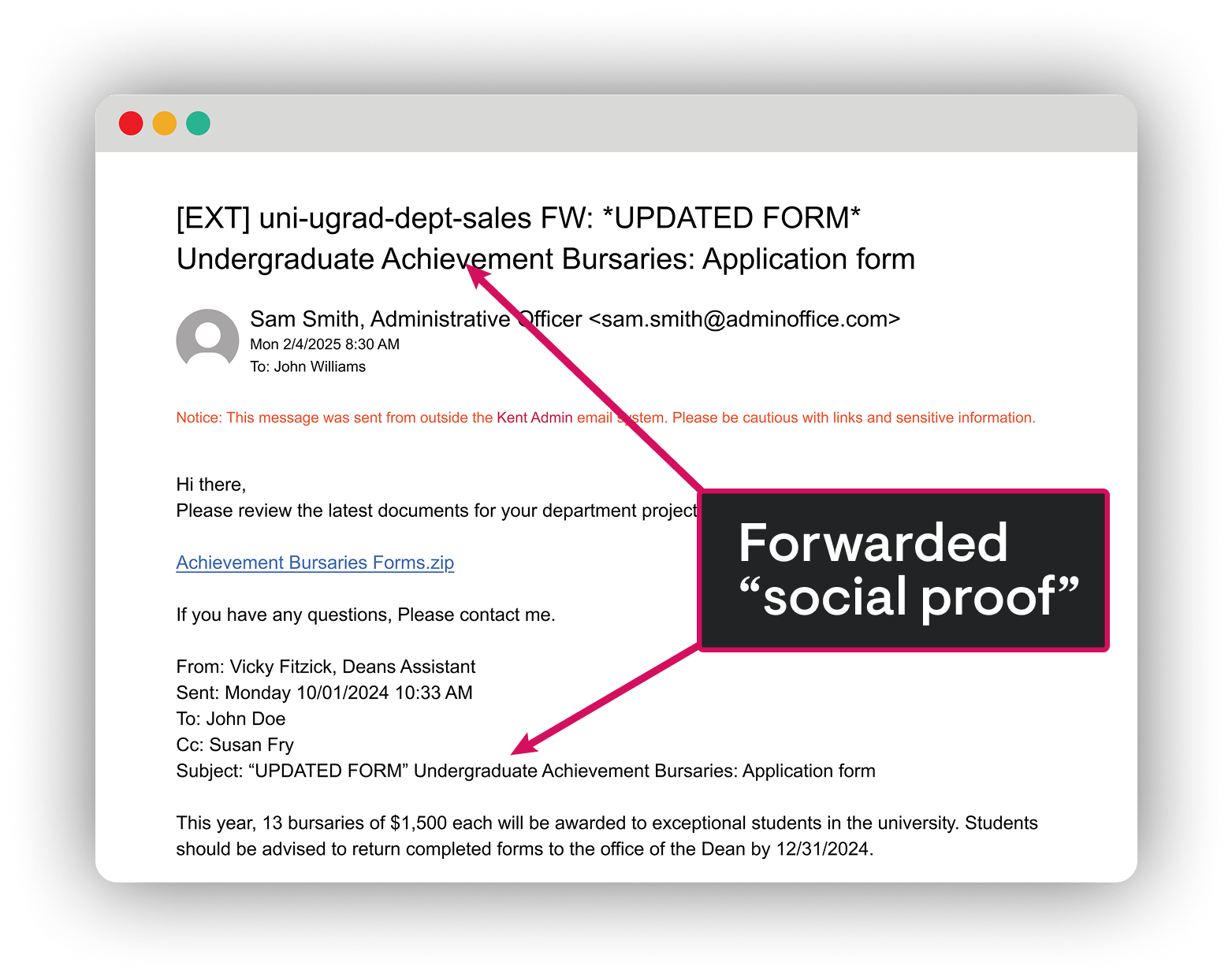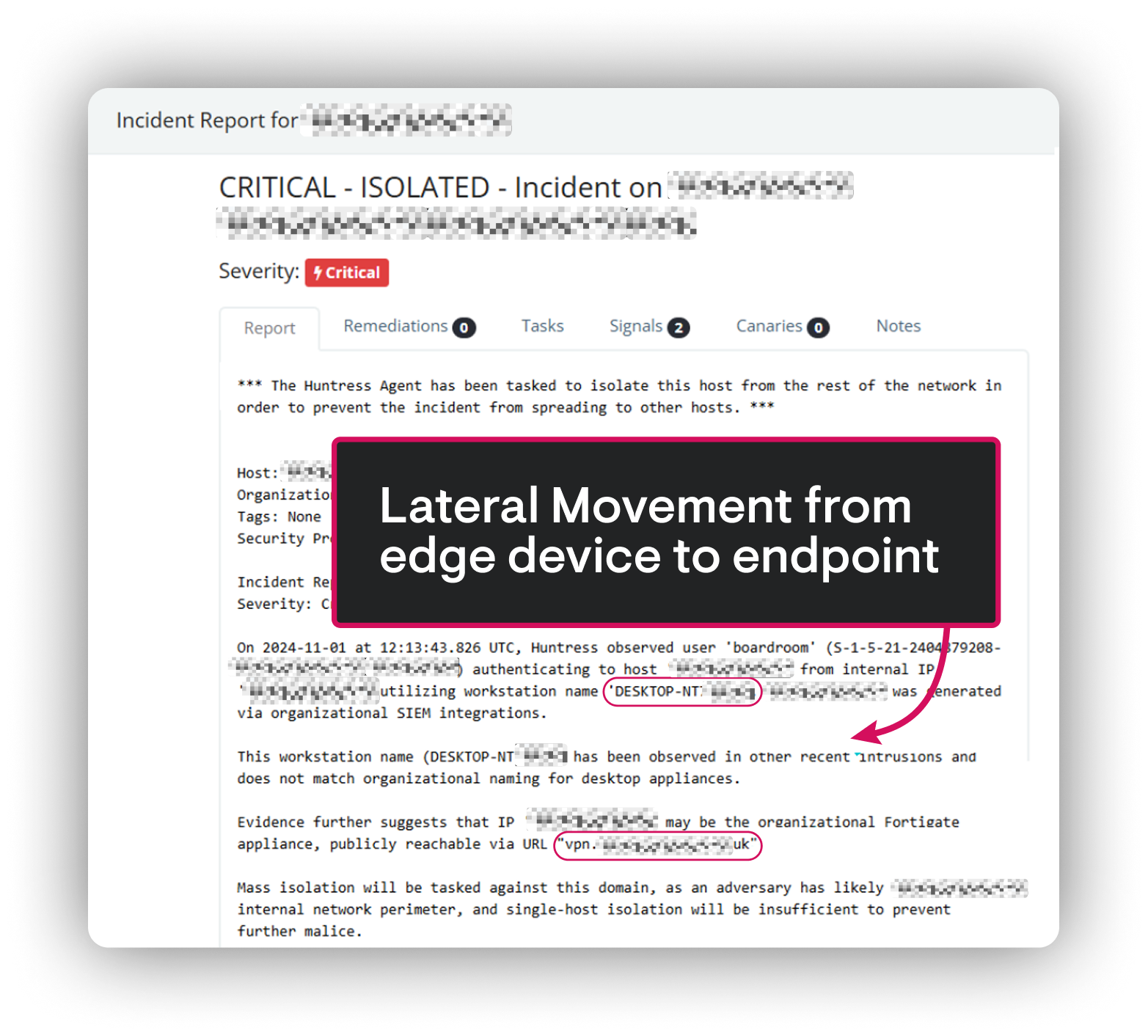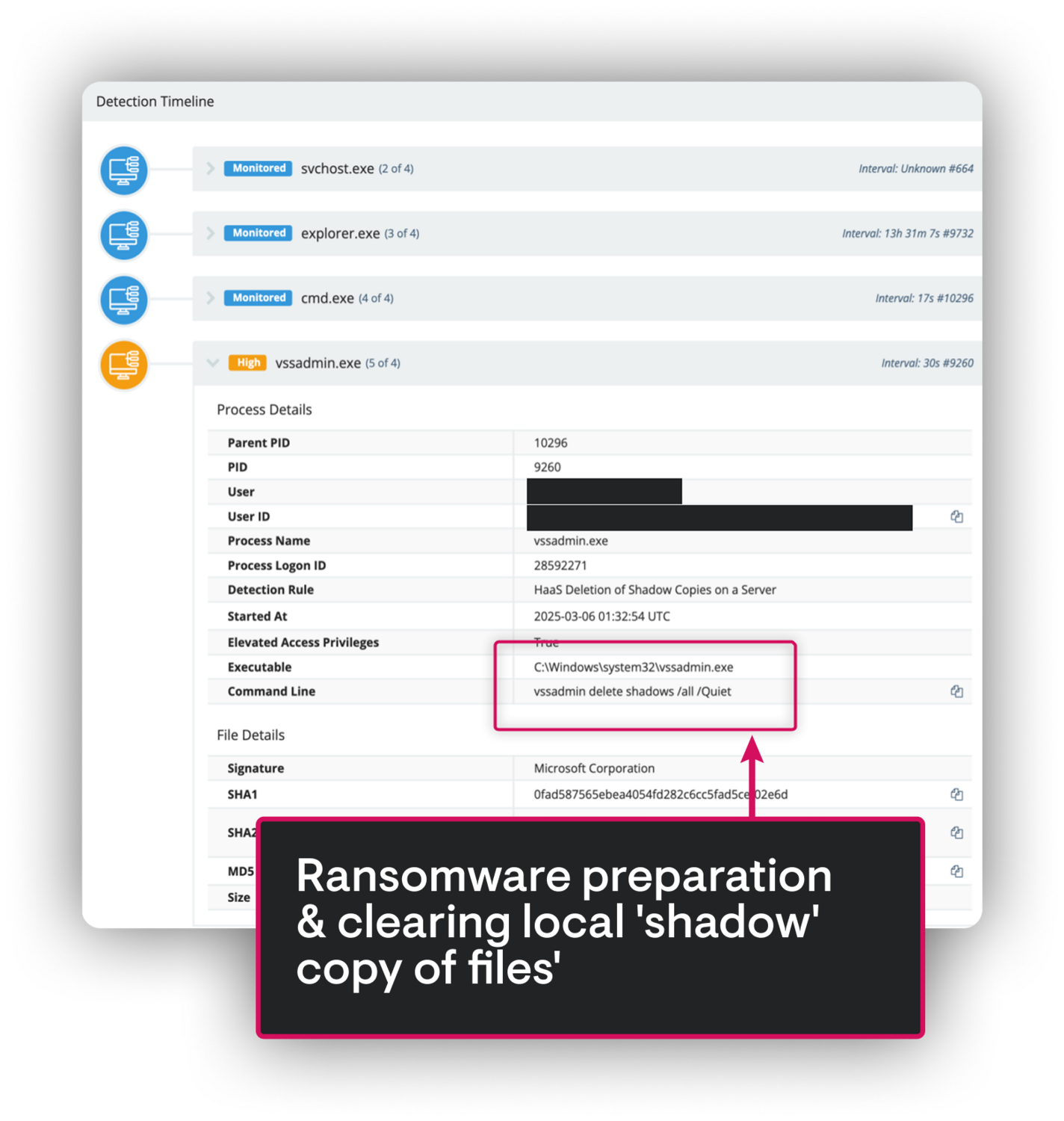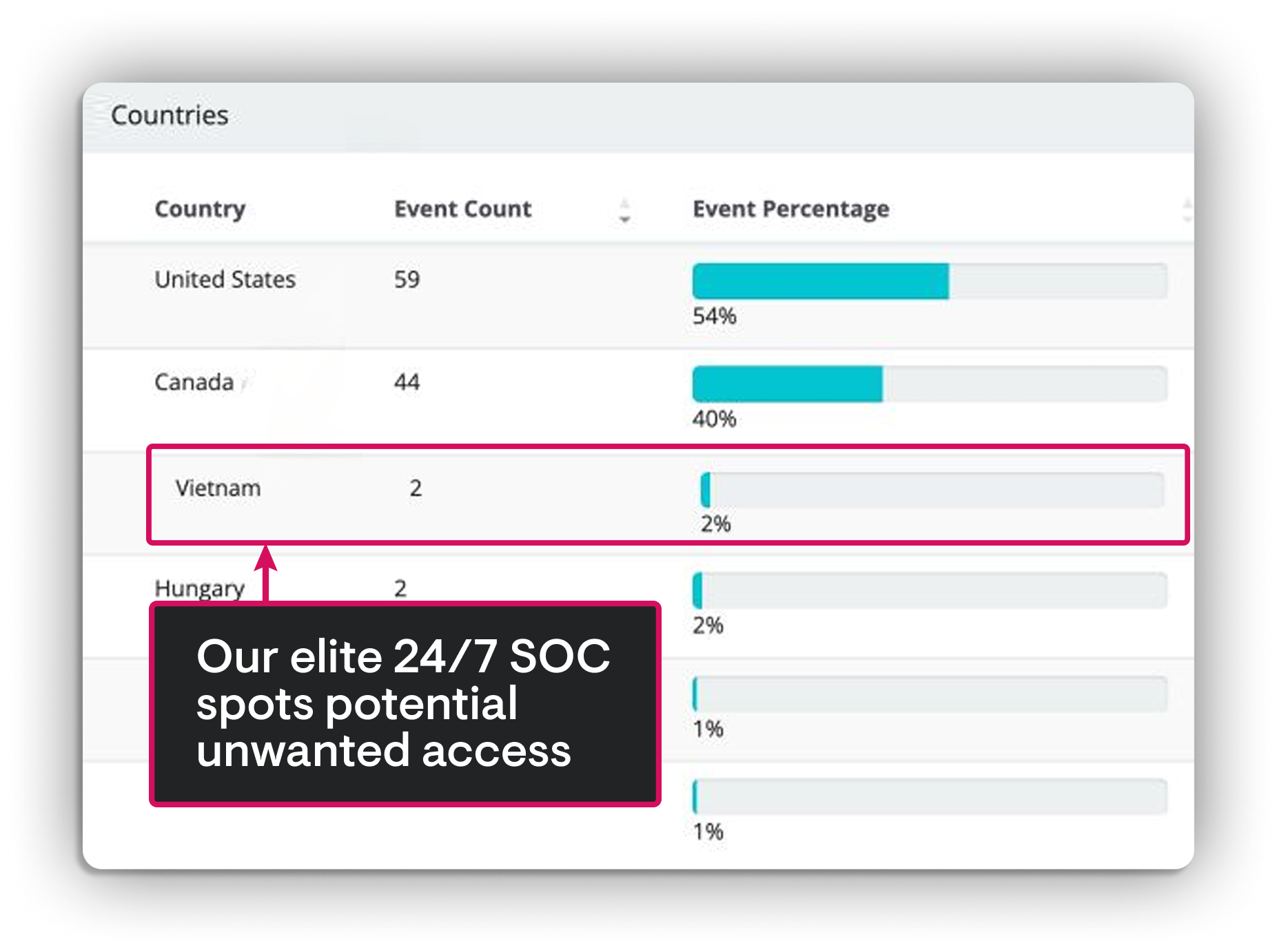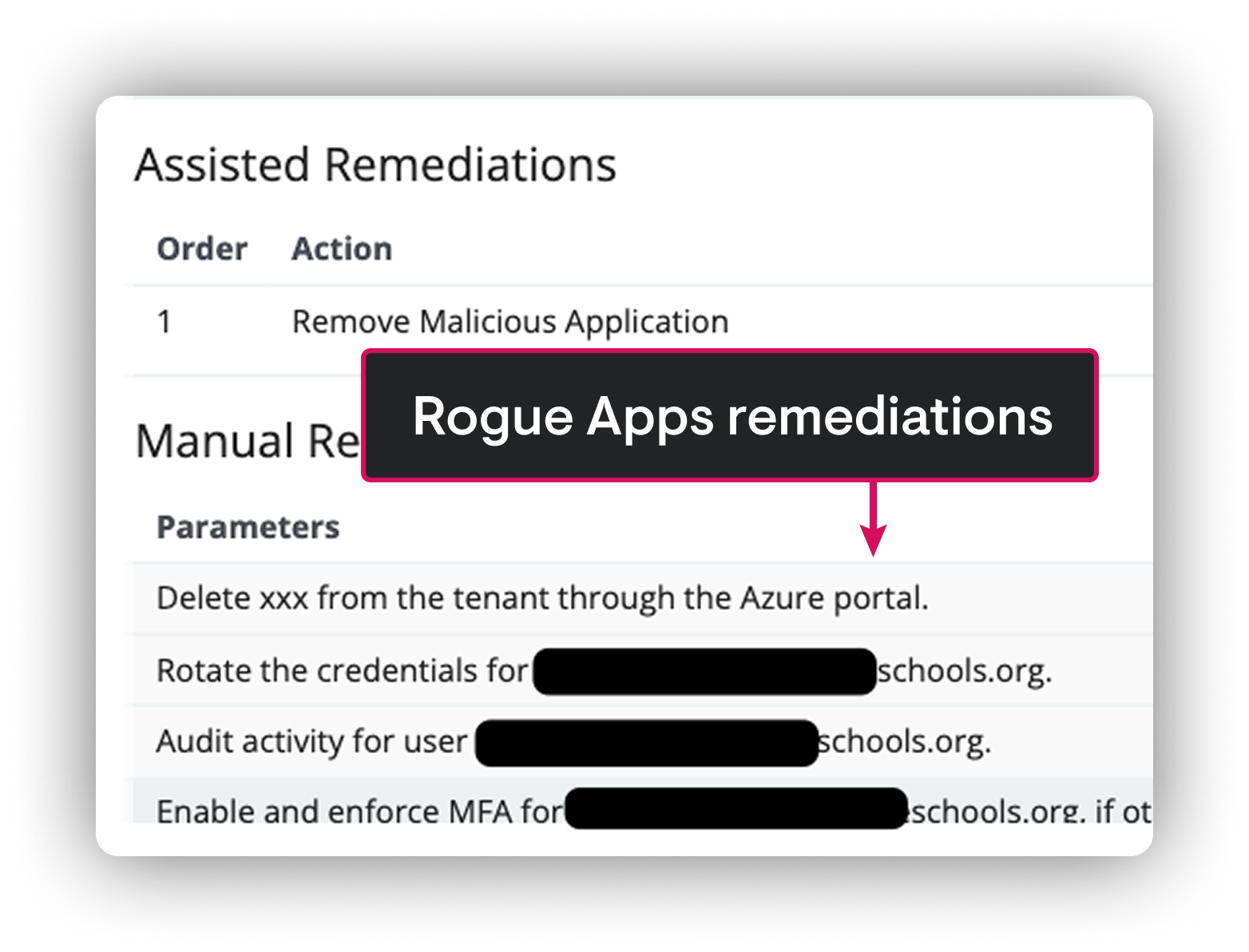
SlashAndGrab
CVE-2024-1709, CVE-2024-1708
- Quickly reverse-engineered the ScreenConnect vulnerability delivering a universal hotfix
- Issued first public detection guidance (with ongoing updates)
- Collaborated directly with ConnectWise to facilitate their response