What Threats Are Lurking in Your Environment?
Today’s hackers are getting smarter.
To evade detection, attackers are abusing legitimate applications and processes to slip through the back door undetected. Once inside, they establish a quiet foothold and plan their next move—often the deployment of malware to cripple systems, or ransomware to encrypt and steal sensitive data.
Huntress detects these persistence mechanisms to identify—and eliminate—persistent actors who are dwelling in your environments through unauthorized access. We protect your customers from today’s clever attackers with custom incident reports, human-powered threat hunting and one-click approval of remediation steps.

To the Point: Persistent Footholds

Initial Discovery
When the Huntress agent is deployed, it begins collecting relevant data and activity associated with persistence mechanisms.

Automated Analysis
Once captured, data is automatically analyzed to highlight known threats as well as identify new and potentially malicious activity.

Human Review
Our SOC team reviews potential footholds. If one is verified, a custom incident report is created with a detailed overview of our investigation.

One-Click Remediation
Along with the report, Huntress includes one-click execution of automated remediation actions and step-by-step instructions for any additional work that’s required.

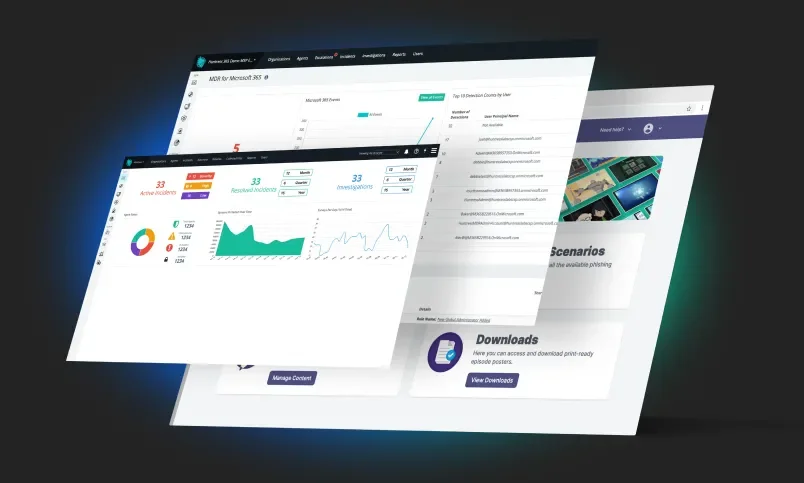
The Huntress Platform
Valuable Intel
Your Huntress dashboard makes it easy to identify and eliminate malicious footholds and persistence-enabled attacks. The dashboard shows active and resolved incidents, reviewed autoruns and comparisons highlighting how your customers stack up against Huntress averages. This enables your team to defend against attackers who are lurking in the environments you manage.


Find and Eliminate Persistent Threats








