A hacker sits behind a screen and reads the text of a website. It’s the Microsoft 365 login page. The hacker has the username and password of a target, and this would be an easy job if not for one thing: multi-factor authentication! Even though the credentials are correct, the site tells them they must tap the notification on their phone to complete the login process. But they don’t have the phone in question.
They think for a moment. How could they coerce the user to tap this notification? Suddenly, a flash of inspiration strikes. The hacker presses the “Resend Notification” link on the login page. Then, they press it again. And again. Ten more times. Twenty more times. The user on the other end is being bombarded by these notifications. After a flurry of clicks, the login form pauses for a moment. Then, the page changes. The hacker has succeeded and is now staring at the user’s email inbox!
But instead of a trove of personal information to pilfer, the hacker only sees one thing: flag{0cc175b9c0f1b6a831c399e269772661}
This doesn’t surprise the hacker. They weren’t targeting a real person. This was a Capture the Flag (CTF) challenge called “MFAtigue.” And they just solved it.
The CTF is a time-honored tradition in the hacking community.

This year, in celebration of Cybersecurity Awareness Month, the Huntress team hosted a month-long CTF tournament. By the end of the CTF, almost 9,000 hackers from all over the world tried their hand at 66 unique challenges to test their hacker mettle. Only about 45 players completed every challenge.
This post is a retrospective on our CTF. We had a lot of fun, learned a lot of lessons, and RickRolled a lot of people.
The Hacker in the Arena
Let’s not get ahead of ourselves. First, what is a CTF?
Capture the Flag, or CTF for short, is the hacker’s sport. In these events, hackers come together either as individuals or on teams to pit their wit and guile against a set of challenges. Each challenge is designed to test their understanding of a technical concept. Each challenge has a flag planted somewhere, and it’s the hacker’s challenge to figure out how to get to it.
CTFs are rooted in hacker tradition, if there is such a thing as hacker tradition. They started where most hacker things started: at DEF CON in the 1990s. CTFs can be for fun or competitive. And when they get competitive, they get competitive!
In competitive CTF, flags make points. The flag represents the successful navigation of a challenge, so to the players go the spoils. Each hacker or team of hackers gain points for correct flag submissions. Some flags may be worth more than others, which is a way to represent the skill required to solve it.
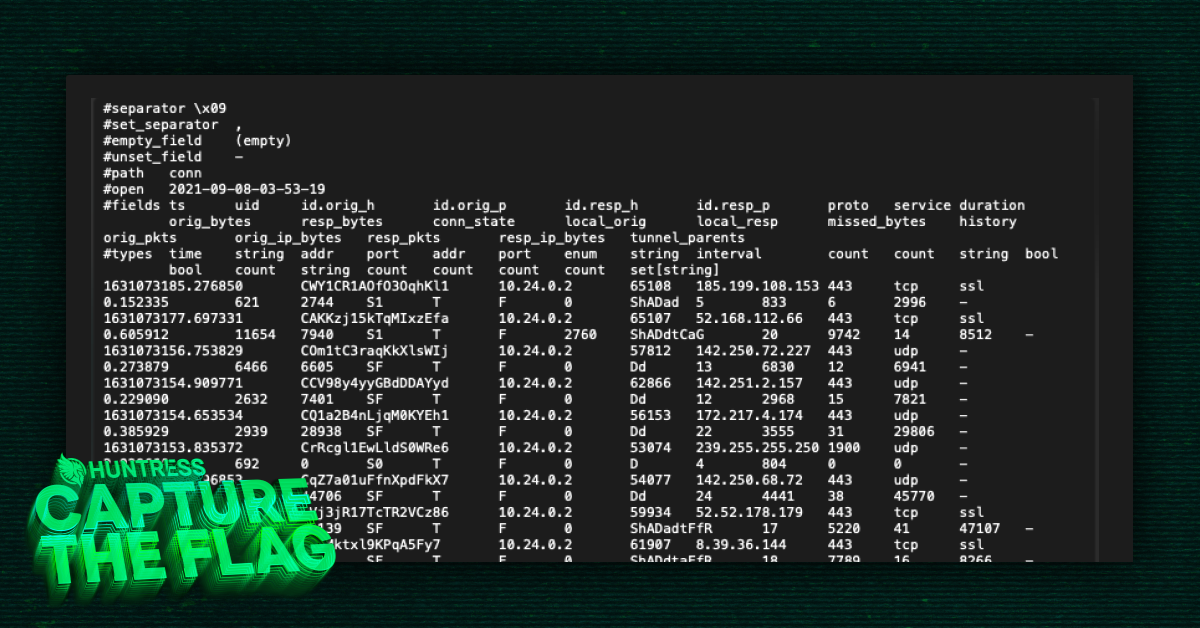
The challenges vary in topic, complexity, and tone. Challenges can span from hacking vulnerable web apps to custom memory exploits, or even tracking a fictional persona by examining their online footprint. You never know what you’ll run up against, and you can’t possibly be prepared to solve every challenge immediately. Struggling, therefore, is expected. We work in a field where no single person has all the answers, and CTFs remind you of this fact.
But one constant remains: creativity. It fuels the design of these challenges, and equally, it powers their resolution. Hackers are inherently creative, so solving their challenges requires creativity.
CTF with Huntress Swag
When Huntress does a CTF, we do it with swag. I’m not talking about the prizes in this case, though everyone in the top 10 ended up with some form of Huntress swag for a prize. In this case, I’m talking about the panache of a CTF that puts you in the well-worn, monochromatic high-top sneakers of the Threat Analyst. Let me explain.
Many CTFs have a distinct tone to them. Challenge design, in most CTFs, can be described as “wacky.” A normal CTF may present you with a well-crafted but silly website, which reads “Welcome to Sally’s Sea Shell Company! Find the best shells here!” As a hacker, you intuit the premise of the challenge. This site is vulnerable to OS command injection and you need to find how to get a shell—how to inject code into the site to gain access to it. The challenge is built to be fun, quirky, and engaging. And it is!
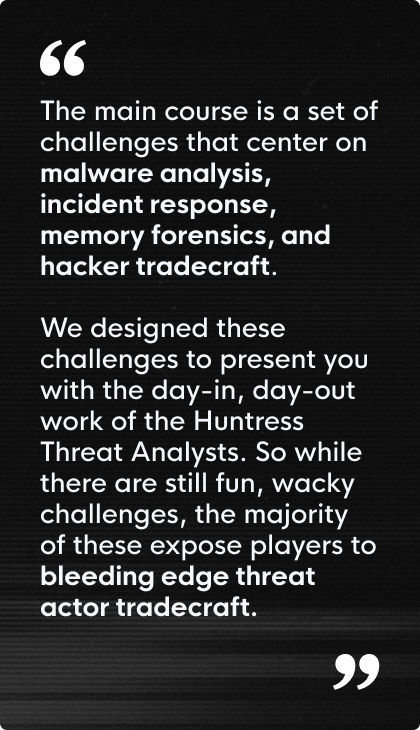
At Huntress, we honor the past but switch it up to the present. The wacky CTF tone is still present, but it’s a dash of spice added to the main course. The main course, in this case, is a set of challenges that center on malware analysis, incident response, memory forensics, and hacker tradecraft. We designed these challenges to present you with the day-in, day-out work of the Huntress Threat Analysts. So while there are still fun, wacky challenges, the majority of these expose players to bleeding edge threat actor tradecraft.
One day, you’re playing rock, paper, scissors against a computer program that can read your mind. The next day, you’re dissecting a malware sample and reverse engineering how it connects to its command and control server. In several cases, the Huntress team even ripped live malware right from the endpoint, cleaned it up a bit, and built it into a challenge. It doesn’t get more authentic than that.
Challenges for Dayz
Good CTF challenge design is like good puzzle design. Each challenge should present the player with everything they need to complete it and leave it up to them to put those pieces together. Maybe the player is a subject matter expert on the premise of one challenge and solves it immediately. But maybe that same player does another challenge where they’ve never even heard of the pieces, let alone know how to put them together. CTFs, then, are as much an exercise in research as they are in the practice of learned skills.
To satisfy players of all skill levels, we diversified the topics and difficulty of the challenges. A player might be able to play a vulnerable website like a fiddle, but doesn’t even know where to start on malware analysis. So, we needed to make a wide array of challenges that could be enjoyed by seasoned experts and newcomers alike.

We also tried to add variety to the subject matter for the challenges. We had classic CTF-style challenges like Land Before Time, which required steganography to solve. Rock, Paper, Psychic pitted the player against a telepathic computer player, where the only way to win was to rewrite the bytes of the program itself. We also included malware analysis challenges like Hot Off The Press, Thumb Drive, Batchfuscation, and PHP Stager, to test the player’s analysis and triage skills.
Some challenges were fascinating in their design and engineering, like the M Three Sixty Five challenges. We gave players the opportunity to use cloud hacking tools to enumerate and exploit an Azure tenant. This was, hands down, my favorite set of challenges for this CTF, and the credit goes to its creators, John Hammond, David Carter, and Dave Kleinatland, for their ingenuity.
Highlights
Several times during the run of the CTF, I saw the following unfold in the dedicated CTF Discord server:
“Just solved [insert challenge title]! I had never even heard of [insert central challenge premise] but now I’m curious and I want to learn more!”
As a CTF challenge designer, there is no better feeling in the world than watching that happen.
Another highlight for me is watching players come up with innovative solutions for challenges. The challenge developer knows the intended solution for their own challenges pretty well, but it’s consistently surprising to watch the CTF players approach, iterate, and solve the challenges with sparks of innovation.
Concluding Thoughts
The glory goes to the hackers in the arena. CTFs bring the hacking community together and remind us that we are all apprentices in a craft that no one has, or ever will, master. We struggle, fail, re-think, and succeed. Our skills overlap, and we bring each other up by sharing what we know. The Huntress CTF was a testament to that.
To the players, thank you! You make the community better. To the winners, congratulations! We’ll see you for the next CTF.

















