It’s been eight months since we launched our Managed Microsoft Defender service in general availability. Tens of thousands of endpoints are now protected by the top-rated Microsoft Defender and the watchful eyes of the global Huntress ThreatOps team—and let me tell you, we’ve seen some shady sh*t. 👀
We explored some of the things we’ve seen and lessons we’ve learned thanks to Huntress Managed Microsoft Defender in a webinar not too long ago. We took a brief trip down memory lane to talk about the story of Managed Antivirus and the types of threats it has helped us uncover in the wild… and there was no shortage of tales to tell.
ICYMI, you can go watch the recording here to catch all the excitement—or keep reading for the recap.
Why AV Needs Active Management
Although antivirus might not be the shiniest tool in your toolbox, it’s a critical layer for thwarting attacks aimed at small- and medium-sized businesses. And because it’s so important, leveraging an AV with a managed component can give you an extra layer of protection against ever-evolving attacks.
The biggest mistake we see with AV (apart from not having it at all) is assuming that it’s a self-sustaining engine. Your AV tool may work, but it doesn’t learn. It needs maintenance. It needs optimization. And it needs active management.
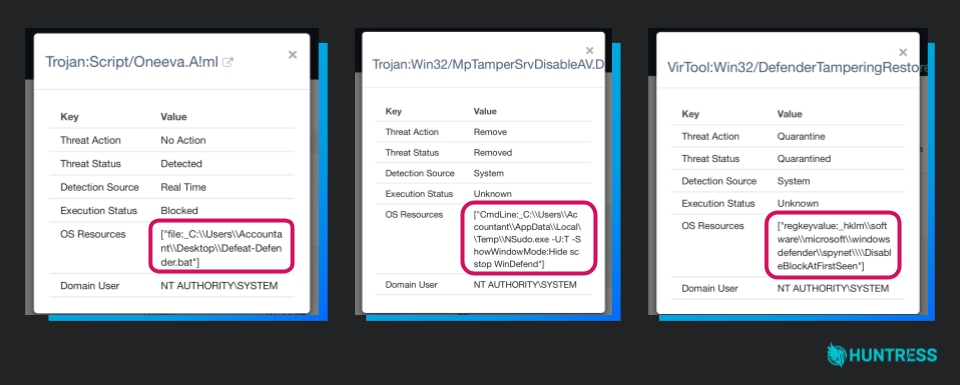
Even when AV does its job, oftentimes, there’s a thread that needs to be pulled by a security analyst. Just look at some of the examples below. These are successful quarantine alerts of a hacker trying to disable or bypass AV. In this case, Windows Defender has technically done its job. However, there’s clearly something shady going on with this host that needs a security analyst’s review.
But finding the time to manage antivirus is tough. Alert fatigue is real—and that’s something we talked about during the webinar. AVs can generate a lot of chatter and noise, and someone has to manage it if you actually want effective antivirus protection.
That’s a big reason why we built Managed Antivirus in the first place.
Dealing with those alerts and managing an AV in general can suck up a lot of time and resources. So our goal with Managed Antivirus was really to deliver on the “Managed” piece. We wanted to alleviate that time and resource burden and provide valuable insight for front-end protection—all without adding a number of new attack surfaces or need to buy a security tool that eats into your profit margins. And building it around Microsoft Defender Antivirus was a no-brainer because Defender consistently ranks as a top product for endpoint protection, performance and security.
Huntress Managed Antivirus vs. Wild Threats
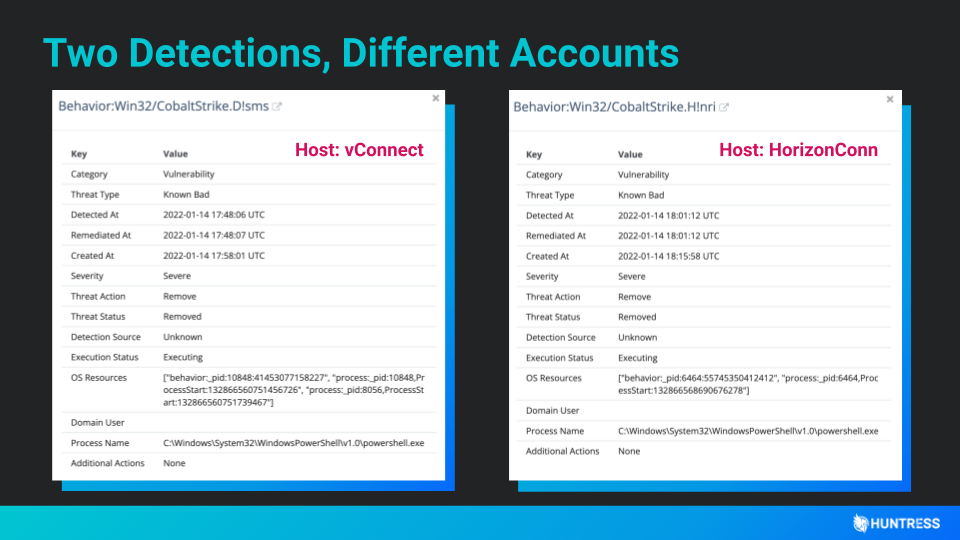
Throughout the webinar, we dove into how Microsoft Defender has held up against Cobalt Strike, Mimikatz and more. I won’t spoil all of the stories, so for the purposes of this recap we’ll stick with one example… the time when a Managed Antivirus detection tipped our SOC to new exploitation of the Log4Shell vulnerability in VMware Horizon.
Actually, our early response to the Log4j exploitation was kicked off with two Defender alerts. At first, we saw an alert that warned our team of a Cobalt Strike implant on one of our partners’ networks. Within minutes, another similar-looking Defender alert came in from a completely different organization.
After doing some research and digging into both alerts, we found a commonality: Hackers were targeting VMware Horizon servers using Log4Shell vulnerabilities. And the rest is history (here’s a technical play-by-play if you’re interested in said history).
It’s hard to believe, but our ThreatOps team comes across stuff like this every day. We’ve actually seen over 2.1 million detections to date! It’s not always at the caliber of Log4j—but as we sift through those AV alerts, we’re always keeping an eye out for shady sh*t.
Interested in learning more? Check out these real-world examples of Huntress partners who have made the switch to Managed Microsoft Defender.