On August 7, 2023, Huntress caught a business email compromise (BEC) that would have scammed us out of more than $100,000 had it gone undetected. This wasn’t flagged by a flashy security tool or even our own solution. This is a story of good ol’ fashioned security awareness training and security-focused business procedures. Here’s what happened.
Some Helpful Context
Huntress works with a small business vendor to support some of our field marketing efforts. Like most small and medium-sized businesses, the vendor requests electronic bank drafts for invoice payments. It’s a routine process. And after all, a simple email to a known contact with a recognized email address normally doesn’t raise any flags. Except when it does. 👀
Incident Breakdown
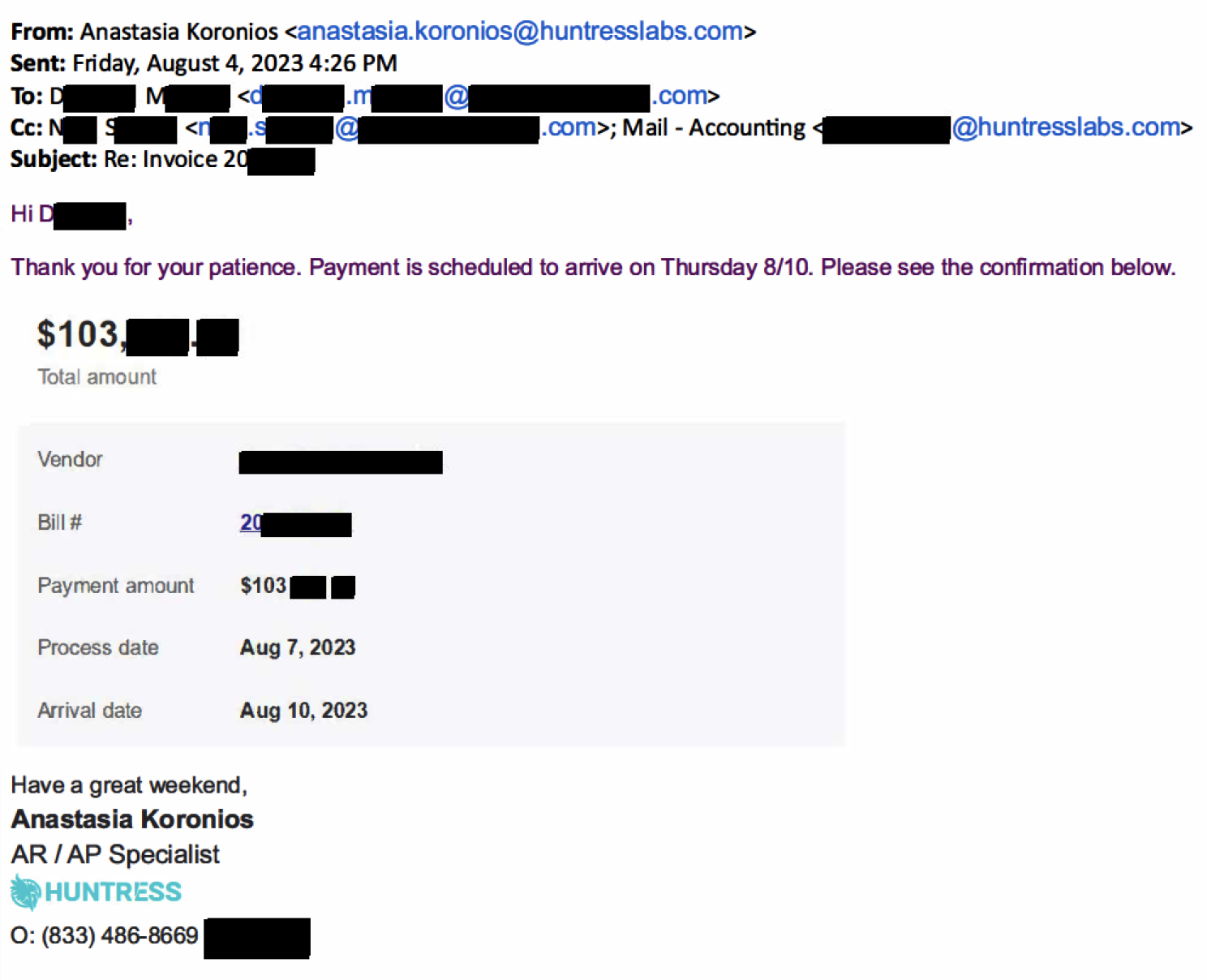
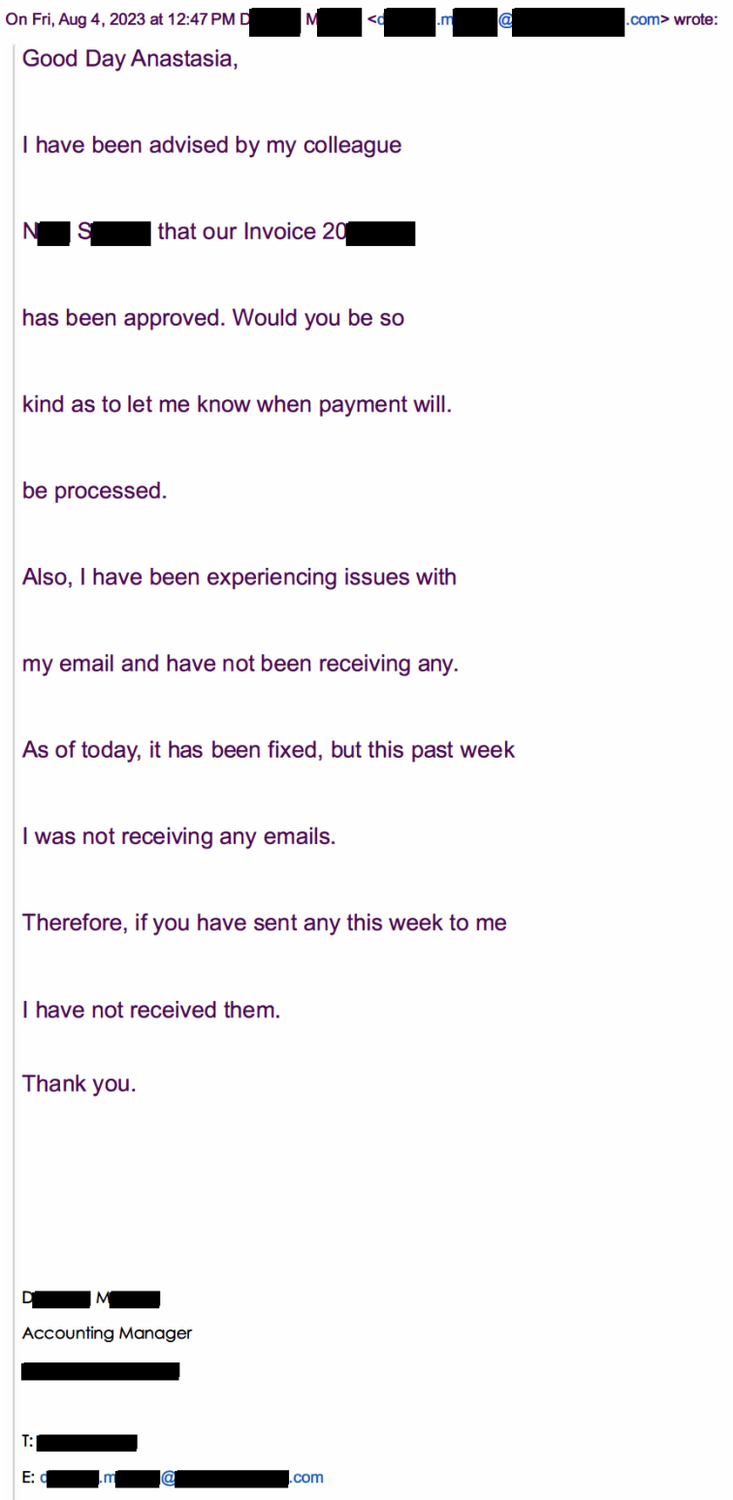
On August 4, 2023, Huntress received a request for payment on an invoice due, so we initiated an ACH payment of around $103,000 to the vendor. Anastasia Koronios, an AR/AP Specialist on Huntress’ accounting team, informed our vendor contact (let’s call her “Darla”) that a payment had been made and that she should expect the money to hit their bank account on August 10.
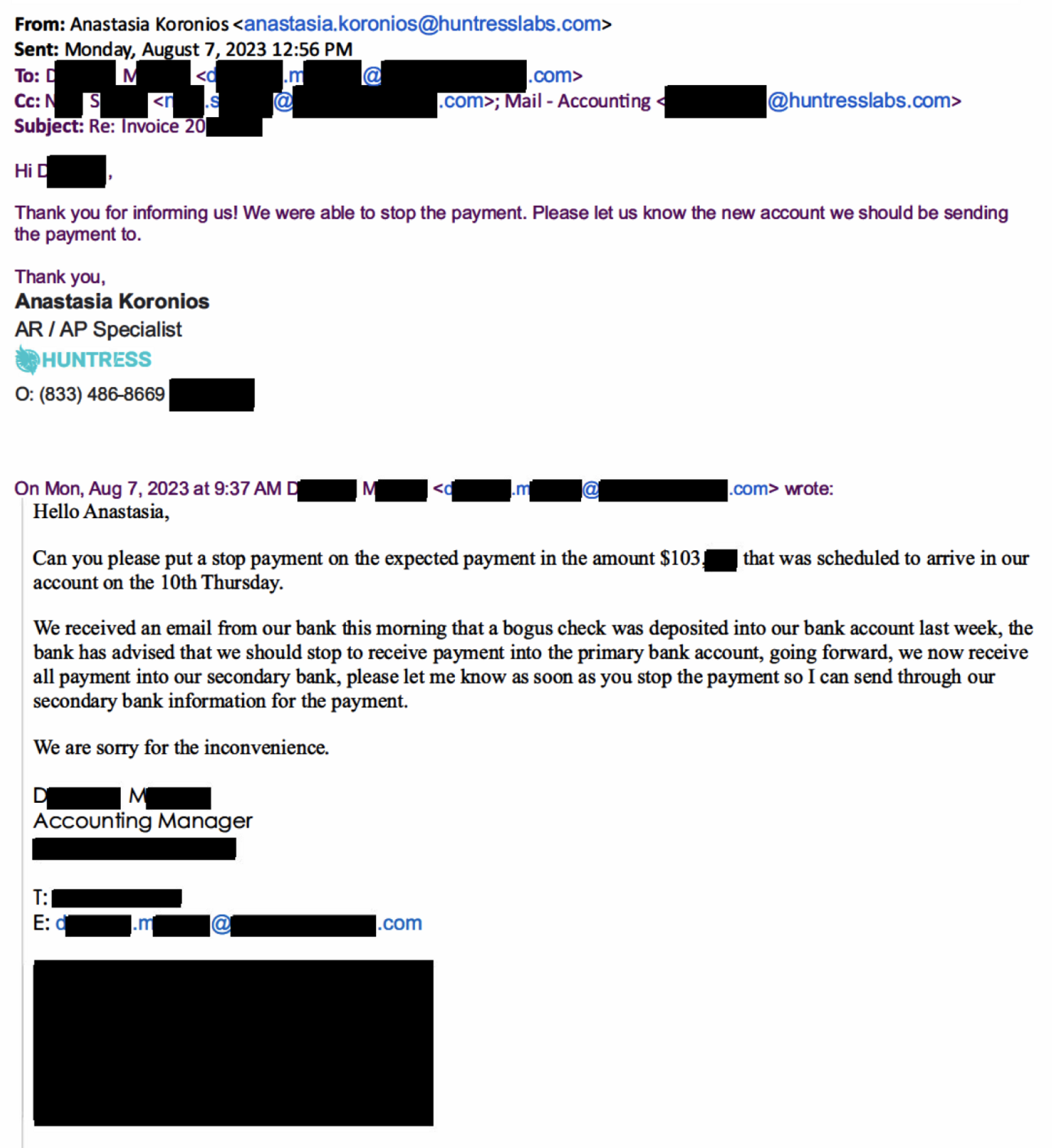
Three days later, on the morning of August 7, Anastasia received an email back from Darla asking us to stop the payment because of suspicious activity in the vendor’s bank account. The email was from the known contact with all of her correct email signatures and information. We stopped payment immediately.
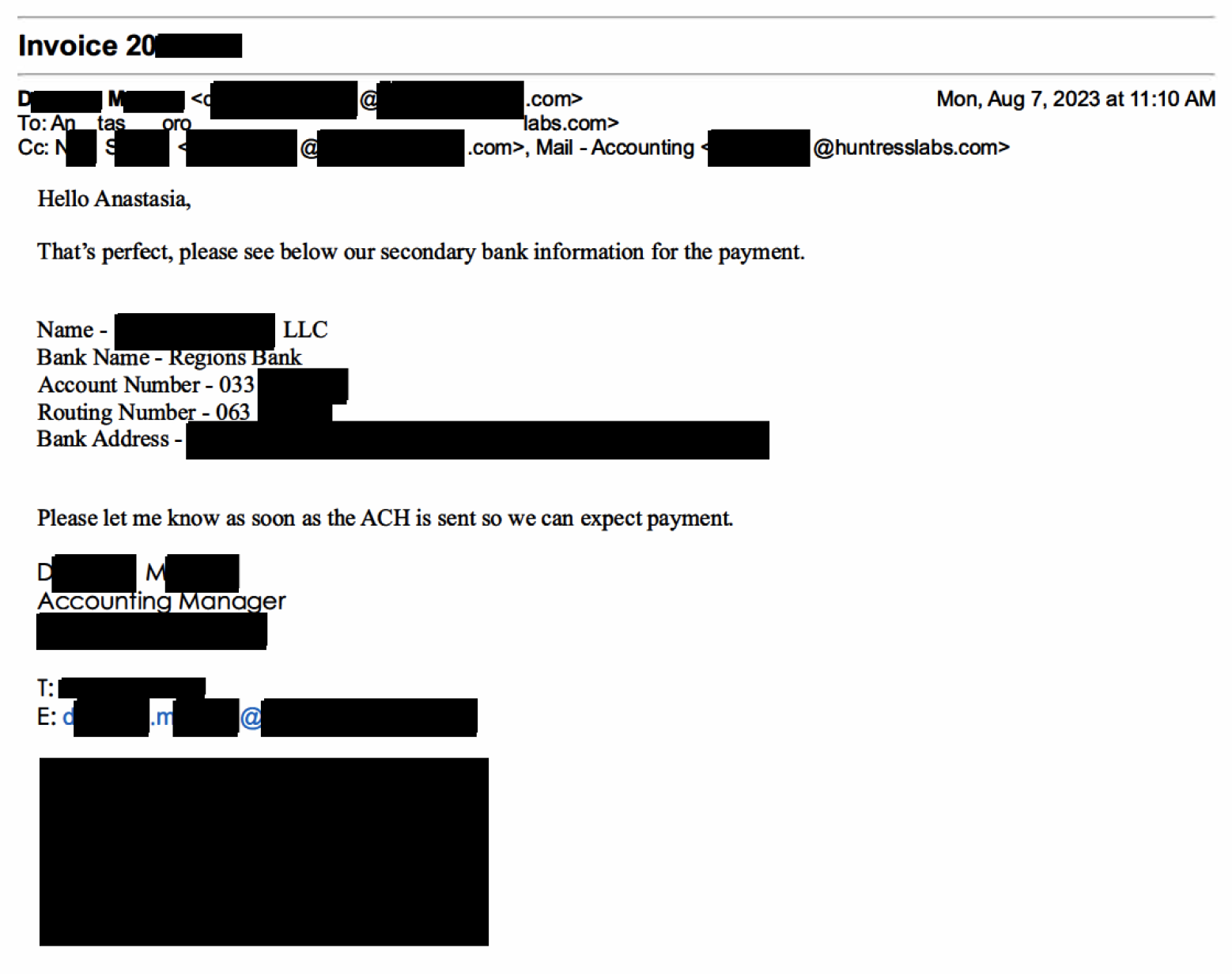
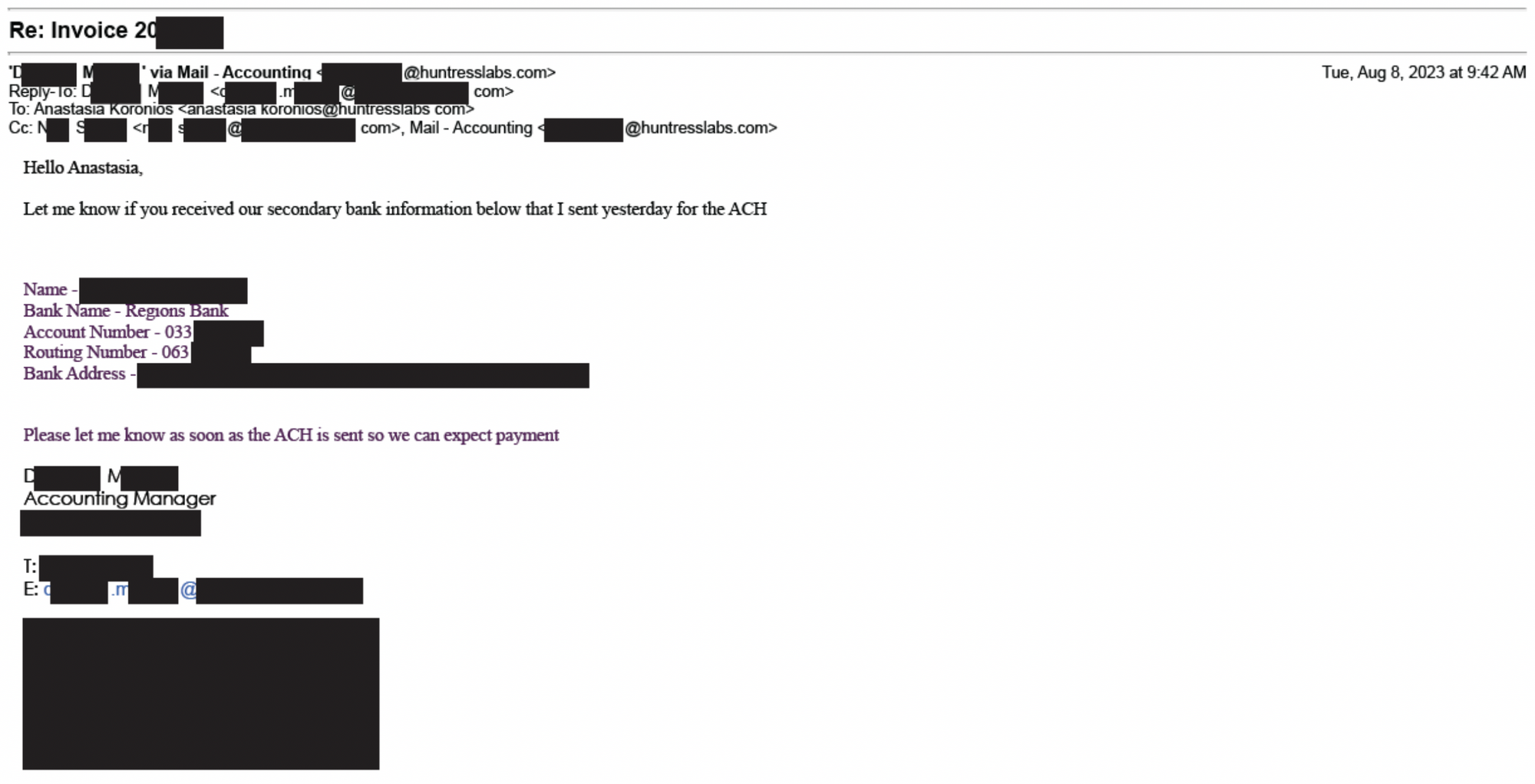
A few hours later, Darla followed up requesting that the payment be re-issued to a new bank, and all of the new account and routing information was included in the follow-up email.
Whenever a vendor presents us with a new bank account, our default procedure is to call our vendor contact and confirm the details. Even though in this case, Darla’s email address was clearly legitimate, we still made sure to call her to reconfirm.
When Anastasia called and asked Darla about the new bank account that she had sent us, she was confused and had no idea what Anastasia was talking about. She said that there was nothing wrong with their bank account, she did not send any emails to us, and in fact, she was having email issues for the past week.
As it turns out, the vendor never sent any of those communications. Their bank never noted strange activity. And the new bank account was not one used by the vendor.
Darla’s email address was completely compromised, and a threat actor was diverting communications and sending fake emails to Huntress regarding the payment and new bank info (which explains her email issues).
After being made aware of the potential compromise, the vendor’s IT team sprung into action. Later that same day, on August 7, Darla called Anastasia back and said that the IT team would be shutting down her email completely. But that didn’t stop our persistent hackers.
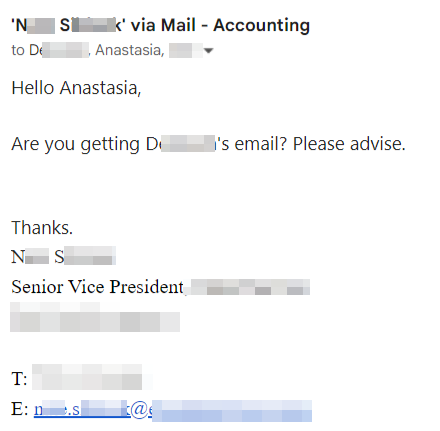
The next day, on August 8, “Darla” sent a follow-up email nudging us on the payment.
Having known her email was shut down, we knew this was the hacker still masquerading as Darla. To further keep up the ruse, her colleague (we’ll call him “Nick”), who was being cc'd on the back and forth, seemed to chime in - which is how we found out that Nick had also met the same fate and was compromised.
As their cyber team investigates how the accounts got compromised, we advised the vendor on next steps for reporting this incident. Our team also reported this to the Regions Bank.
Lessons Learned
Employees are often the first line of defense against these types of attacks. As attackers get smarter and their attacks become more sophisticated, regular security awareness training is critical.
From her own training, Anastasia knew that in situations where new bank information is sent via email, calling the vendor directly to confirm is the only way to ensure the details are accurate. In this case, that training paid off (quite literally), saving the vendor a potential loss of more than $100,000.
Although Huntress wasn’t the one being directly targeted, this event could have still ended poorly for us had it not been for the security-first culture of our accounting team and the organization as a whole. Had our team just sent money like the hackers hoped for, our upstream vendor might not have been able to continue to fund staff to our projects, and we likely would not have recouped the $100k. Equally painful: we would likely also be spending time with lawyers and law enforcement as part of the criminal investigation. But worst of all, we could have lost a key partner had the attackers not been identified.
As a general best practice, if you are unsure of an email’s legitimacy, you should always contact the sender via a separate means of communication before providing sensitive information or funds. We benefited by having bank callback procedures already in place, so when the new bank details came in, we didn’t have to make a one-off decision on whether we should call back to confirm. We just automatically did it.
How do you get this security-first culture beyond the technology team? Consistent and ongoing security awareness training can make a huge difference. Every employee at Huntress uses our own Security Awareness Training solution - through monthly training episodes and regular simulated phishing campaigns, we’re always enabling our internal team to become more cybersavvy in the fight against bad actors.