Hollywood: home of some of the craziest, cringiest, out-of-this-world hacking scenes. Maybe it’s two characters in NCIS partnering up in a strange attempt at isolation (literally partnering up, by frantically typing on the same keyboard). Or maybe it’s a detective slinging one-liners like: “I’ll create a GUI interface using Visual Basic, see if I can track an IP address” (thank you for that gem, CSI: NY). Or maybe it’s just Swordfish. The entire movie!
But it’s not all terrible. Some directors take the time to hire technical advisers, and the payoff is both thrilling and accurate. Mr. Robot is a shining example: it includes everything from Metasploit to mimikatz, and features some truly poetic monologues from Rami Malek’s Elliot: “At my fingertips the zero day is wrapped in code like a Christmas present, then becomes an exploit, the programmatic expression of my will. I live for this sh-t.”
In our July Tradecraft Tuesday episode, Huntress hacker movie aficionados Greg Linares (Principal Threat Intelligence Analyst), Matt Kiely (Principal Security Researcher), and John Hyland (Principal Software Engineer) talked about their favorite Hollywood hacking scenes, along with the ones that were epic fails.
You can watch the full episode here.
The Beekeeper: The IT scam scene
At the start of The Beekeeper is a scene where retired school teacher Eloise Parker falls for an IT help desk scam, which results in her life savings being drained. And that kicks the plot of the movie into motion.
The movie does a good job of depicting a typical real-life IT scam. Victims get a pop-up alert saying they’ve been infected by malware, with a phone number for them to call for further assistance. In the movie, the scammers tell Eloise that they’re part of the antivirus company that was pre-installed on the machine. The scammers are also working in massive office spaces that have been converted to call centers, which is another accurate detail.
As an added bonus, while the scammer is on the phone with the victim, we see a remote desktop solution website. This indicates that the scammers will have the victim download a Remote Monitoring and Management (RMM) tool from the site, something that absolutely happens in real-world attacks. In the background, we can also see various phones lined up, which is a nod to an ongoing, separate clickjacking operation.
Figure 1: An accurate scammer scene, complete with clickjacking and RMMs in the background. Still from The Beekeeper (2024), courtesy of Amazon MGM Studios.
Finally, after the scammers convince Eloise to download the RMM software, giving them access to her accounts, they tell her to type in her master password. This likely gives them access to the victim's password manager, another level of detail that makes this scene more realistic.
The Good Doctor: A ransomware attack on a hospital
Season 4, episode 10 of The Good Doctor (called “Decrypt”) focuses on a ransomware attack at a hospital—something that we’re all too familiar with these days, unfortunately. The episode portrays some of the realistic challenges that hospitals face when they’re hit by ransomware, like the impact on the Pyxis system, which helps healthcare professionals dispense the right medications to the right patients at the right times. The episode also shows the impacted hospital rerouting non-critical patients to other hospitals, which we’ve seen happen many times.
The episode includes a good level of detail about the ransomware attack, all the while with minimal UI display (minus a scene where a character restores the hardware and restores the backups). One plot detail reveals that the initial break-in occurred 30 days before the actual ransomware deployment, with the attackers waiting for the onsite and cloud backups to sync before encrypting them. The plot even brings in cyber insurance, with an insurance representative performing a failed negotiation attempt with the group.
The one questionable part of the episode is references to a “botnet worm” that could destroy all hardware unilaterally. But, it is later revealed that these references are actually a scare tactic by the threat actor. This use of emotional manipulation by attackers is definitely more realistic, with real-life threat actors using an array of techniques to pressure their victims to pay.
Bones: “Whoever did this wrote malware on bone…”
We won’t beat around the bush: the depiction of hacking in season 7, episode 6 of forensic crime show Bones (“The Crack in the Code”) is atrocious. Haven’t seen it? This should speak volumes:
Figure 2: Bones attempts to envision a world where bones can include a computer virus. Image from Bones, © 20th Television / Fox Broadcasting Company.
The premise of the episode is that someone carved fractals into bones, which apparently had the ability to set off fires by modifying a computer’s CPU so its fans don’t go off. Outside of the ridiculousness of this premise, there are certain concepts that are at least adjacent to what was referred to in this episode. For instance, safe-seeming images (PDFs, PNGs, XML documents) can contain malware—but fractals on bone is another level. And real-world malware can also cause physical changes portrayed by the scene (when malware turns off the fan), as we’ve seen with Stuxnet destroying centrifuges in Iran's nuclear program.
While these concepts are very much real at a high level, it doesn’t take away from the sheer silliness of the episode, especially this line:
“Whoever did this wrote malware on bone that took down a million bucks worth of computers.”
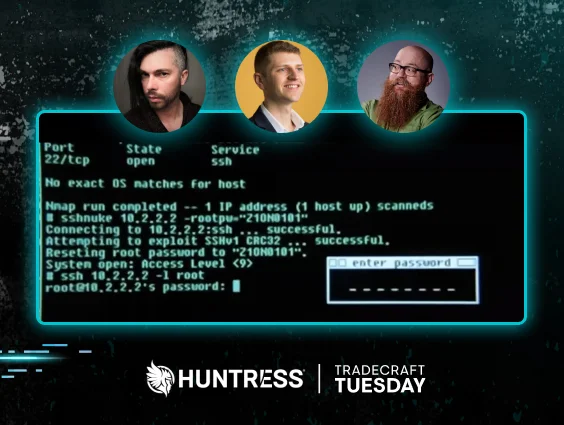
The Matrix Reloaded: SSH and nmap = 👌
Let’s look at a Hollywood hacking win for a moment as a palate cleanser from that Bones scene. Specifically, check out the still below from The Matrix Reloaded, which comes from a scene where Trinity is targeting a power grid computer.
Figure 3: The Matrix Reloaded shows an SSH exploit. Clip from The Matrix Reloaded (2003), courtesy of Warner Bros. Pictures.
Here, Trinity relies on legitimate hacker tradecraft, including the use of:
- Nmap, a widely used port scanner, is used to figure out what services are running on the servers they’re trying to hack
- An SSH exploit. While there is no evidence that the script used in the movie (“sshnuke”) exists, the scene specifically references an actual vulnerability in SSH CRC-32 that was found only a few years before the movie was released
- Once Trinity gets in, the RRF-Control power station OS looks at least plausible, with the command structures similar to the old Cisco IOS interfaces
While it wasn’t completely accurate—there was one niggling UI ACCESS GRANTED pop-up—this scene was pretty close to perfection.
Skyfall: Is Q hacking here, or getting hacked?
In Skyfall, Q gets physical access to the laptop from villain Raul Silva while Silva is in custody. What’s the first thing he does? Connects Silva’s computer to the MI6 network, of course.
Beyond this blip, there are several other questionable parts of the scene. Q said that Silva has established failsafe protocols to wipe the memory if there are any attempts to access certain files. “Only about six people in the world could program safeguards like that,” he claims.
Realistically, it wouldn’t be that hard to write a fail-safe like this to detect when a file is being accessed.
Figure 4: A strange mix of x86 assembly language and JavaScript in Skyfall. Still from Skyfall (2012), courtesy of Metro-Goldwyn-Mayer Pictures / Columbia Pictures.
Now, while Q mutters things like “security through obscurity,” let’s take a closer look at the representation of Silva’s laptop (in Figure 4 above). On the upper-left side, there’s a relatively accurate portrayal of x86 assembly language, which is used to represent human-readable code instructions for x86 processors. For instance, we see MOV EDX (used to move data into the EDX register) and MOV EDX (used to move data into the EDX register), and we see MOV ECX 1BH (the instruction for copying the hex value into the ECX register).
But then, as we start reading further down, we start to see things disintegrate a little bit. For instance, we have try/catch lines, and then, below that, we have just straight-up JavaScript, with some twists that were an apparent attempt by the directors to tie the code back to elements of the movie plot, like Q and MI6:
If {windows.nav.Qname.appName - - MI6><Explore>Element>”}
There are a few other sketchy parts of the scene, including a strange hexdump involving columns rotating along the different axes, before finally clicking into place to spell out “Granborough.” All of a sudden, hexdumps have the magic ability to move across an axis, and the characters like G, R, N, U, and H have mysteriously been added as hexadecimal letters!
And of course, we can’t leave out the use of Weird Abstract Shapes™ for representing cybersecurity concepts.
The Social Network: Accurate Capture the Flag event depiction
Rounding out our list are two hacking scenes from The Social Network (the 2011 movie about the founding of Facebook).
The first is a pretty accurate portrayal of a Capture the Flag event, where interns are competing for full-time jobs at Facebook. Mark (as in Zuckerberg) says that the interns have 10 minutes to get root access to a Python website, expose its SSL encryption, and intercept the traffic over its secure port.
Certain parts of this scene are realistic, like the ability to get root access to a Python web server, while others are a little iffy. For instance, for exposing SSL encryption, SSL/TLS uses asymmetric cryptography for the initial handshake (after the initial handshake, everything is symmetric), so the public key for the website is already available. What Mark could mean instead is that the interns would need to recover the private key off of the server after they root it. However, even then, Perfect Forward Secrecy (PFS, which most web servers implement) would prevent the decryption of traffic even in the case of having the private key.
As a bonus scene, one of the more epic parts of The Social Network is when Mark builds an application in his dorm room that gives him the eventual inspiration for Facebook. This requires him to use scripting and wget as he navigates different individual Harvard “Facebooks” to retrieve pictures of students. The scene perfectly captures the hacking methodology, as Mark narrates the technological setup of what he’s trying to go after, what the blockers are, and how he gets around them.
Hollywood hacking scenes: Capturing the feeling of hacking
We’ve outlined the good, the bad, and the ugly of hacking scenes in Hollywood, from viruses apparently in human bones to ransomware attacks on hospital Pyxis systems. Have your own thoughts on the worst Hollywood hacking scenes? Check out our bracket, here, and sound off with your own!
The main takeaway is that Hollywood does have an interest in using hacking techniques for plot devices—of course, with varying levels of care when it comes to accuracy. And, while sometimes it’s easy to get hung up on the technicalities, or lack thereof, in film and TV show hacks, Hollywood in certain cases does a good job encapsulating the feeling and emotions that go into hacking.