We are no longer battling against the classic Hollywood depiction of cyber criminals. Hackers are now acting at the same maturity level as leading software vendors — using advanced automation tactics to find their next targets, making it easier to deploy and scale their attacks, and innovating faster than ever. They’re even packaging their skills and services and selling them to the highest bidder on the dark web.
One of the most common targets of phishing and business email compromise are Microsoft/Office 365 credentials. Although most security geeks would focus on the technical wizardry it takes to conduct these attacks and bypass protection mechanisms, this is not that tale. Instead, we chose to focus on the people and economics behind these attacks that tend to lurk on underground hacking forums.
To show you just how much the playing field has changed, we took a quick trip to some of these shady marketplaces. The Huntress team hopes you enjoy this screenshot rich saga.
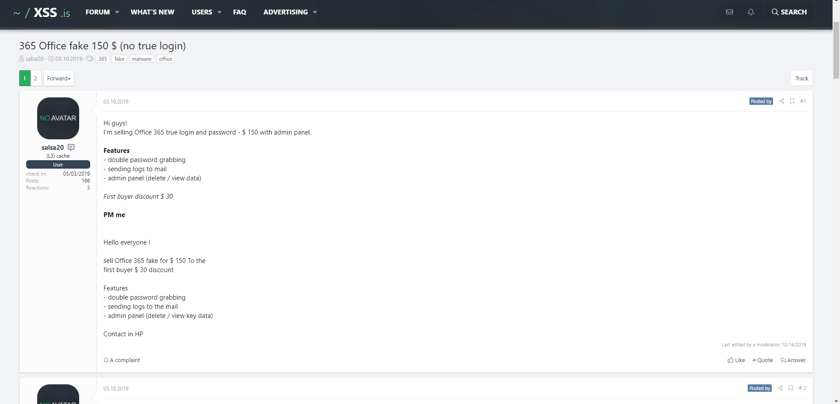
365 Office Fake 150 $ (no true login)
Source: https://xss.is/threads/32243/
To kick things off, it seems appropriate to highlight that cyber criminals — like friends/family/employees — come in many shapes and sizes. In 2020, you’ll often discover hackers have divided into specialized skill sets.
A perfect example of this is the below “for sale” thread where one hacker will provide fellow hackers a fake Office 365 login page that can be used in phishing attacks for $150. When victims mistakenly submit their data, the fake login page will send captured usernames and passwords (“logs” in underground jargon) to the purchasing hacker via email.
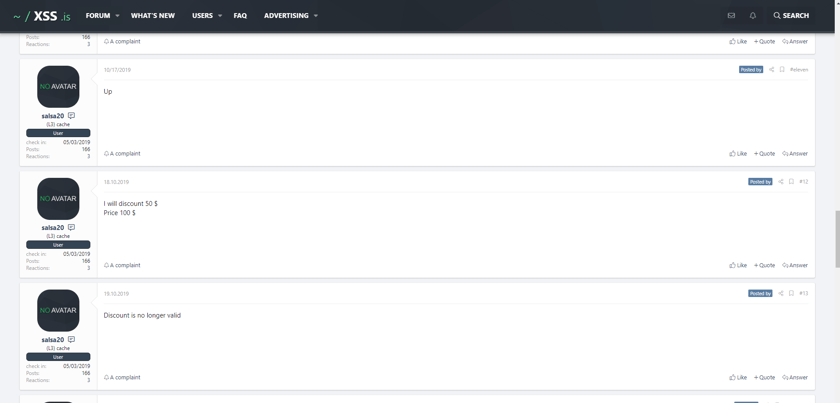
Notice how the seller “bumps” their for sale thread with a daily post. These new daily posts cause the thread to show up at the top of the for sale queue, which maximizes the amount of inbound traffic the thread will receive. We agree that increasing awareness is a slick marketing skill, but we were most impressed with their use of limited-time discounts to entice customers. The fear of missing out is a powerful sales tactic. 😉
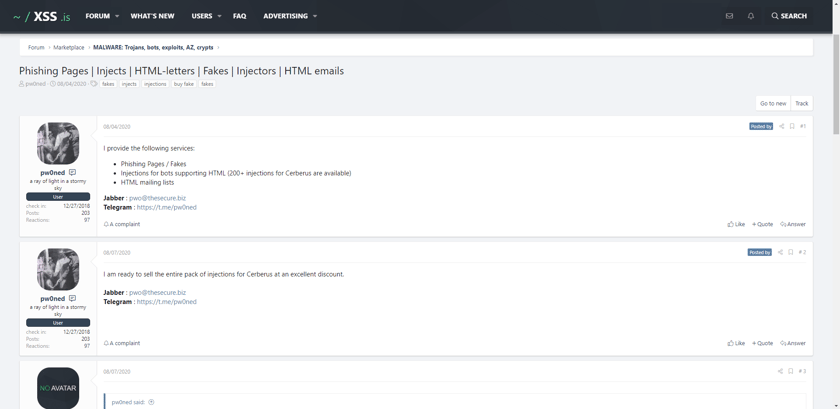
Phishing Pages | Injects | HTML-letters | Fakes | Injectors | HTML emails
Source: https://xss.is/threads/40424/
Although access to corporate Office 365 accounts are highly prized, there are phishing solutions for just about anything you need. Some hackers provide more generalized services, and some even specialize in different sales techniques.
Looking to save a buck but can’t find a coupon? This hacker allows you to buy phishing templates in bulk for all the most common banking, social media and productivity websites!
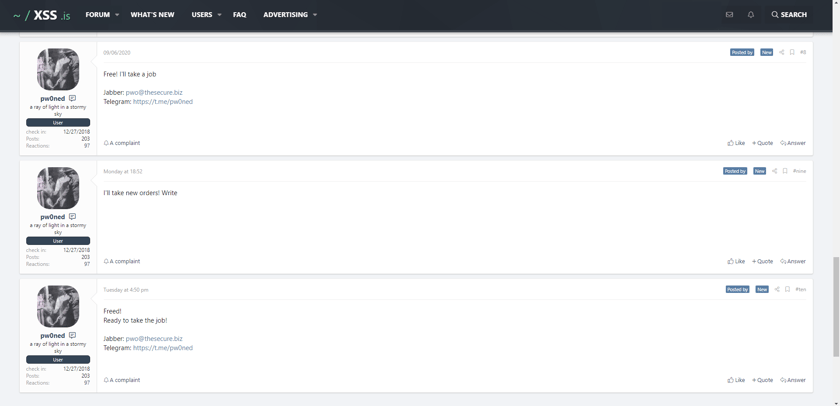
Just like companies coming out of the COVID-19 recession, this seller also wants everyone to know they are open for business. 🤣
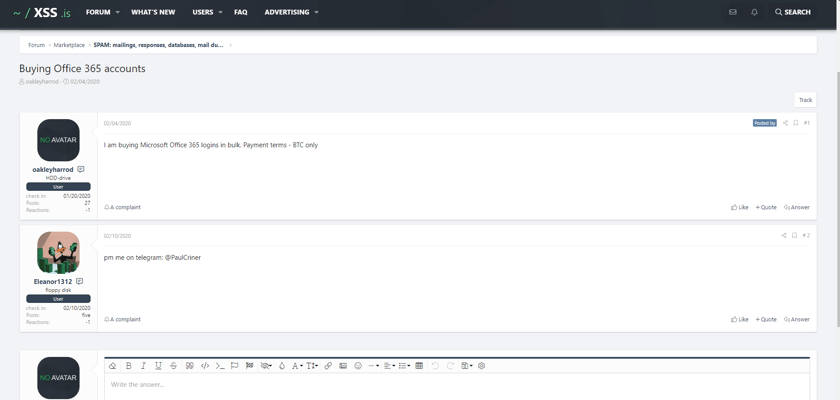
Buying Office 365 Accounts
Source: https://xss.is/threads/34785/
However, some hackers are savvy enough to understand that they don’t need to know every ingredient that goes into the sausage. Why waste time phishing for credentials when you can simply post a “wanted ad” for logins in bulk?
When you specialize in profiting from compromised Office 365 accounts, your time is money — and the slight overhead from outsourcing your password harvesting will hardly impact your margins. 🤑
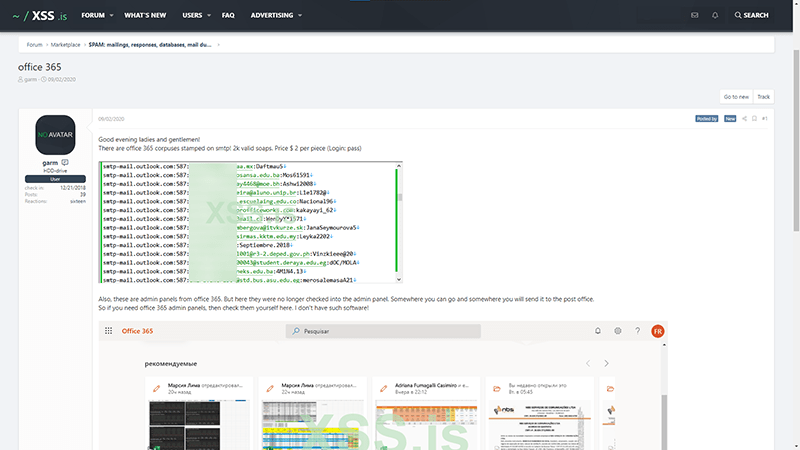
Office 365
Source: https://xss.is/threads/41693/
As you can see, the economic principles of supply and demand clearly apply to these dubious marketplaces. As a result, there are plenty of hackers willing to phish and steal credentials for you.
This “for sale” thread offers prospective hackers Office 365 email addresses and passwords served on a silver platter for $2/each with a minimum purchase of 100 accounts.
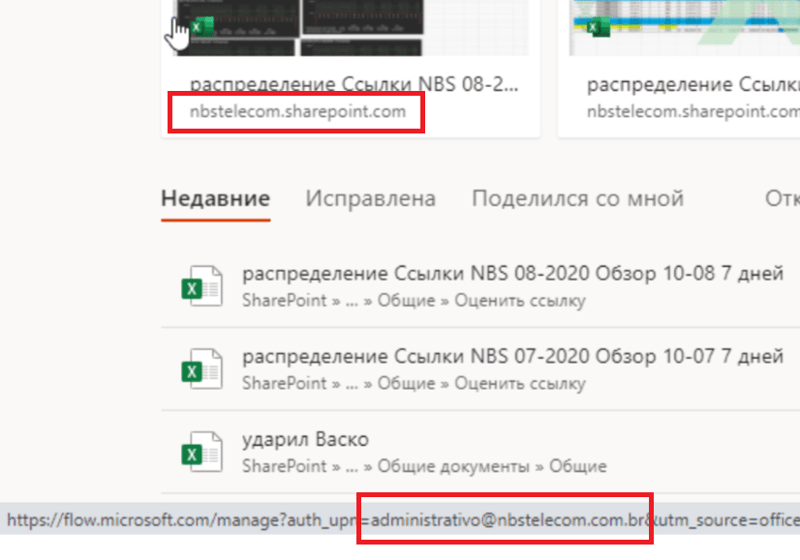
The hacker even highlights that some of these accounts have access to the Office 365 administrative panels and includes a screenshot that claims to be from Brazilian Internet Service Provider (ISP) NBS Telecom’s administrator account as proof.
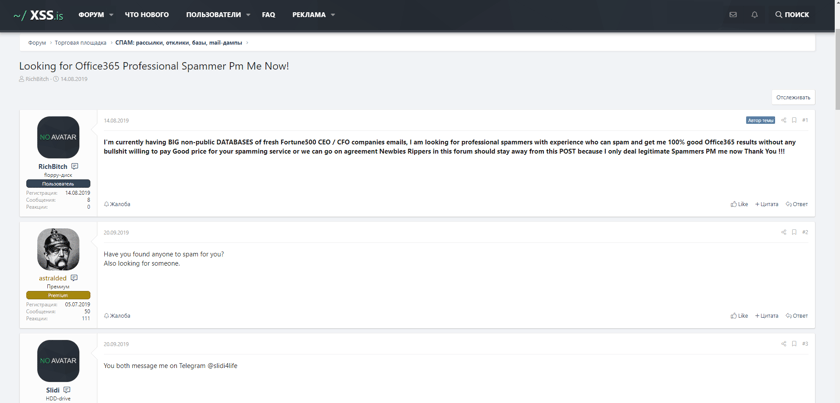
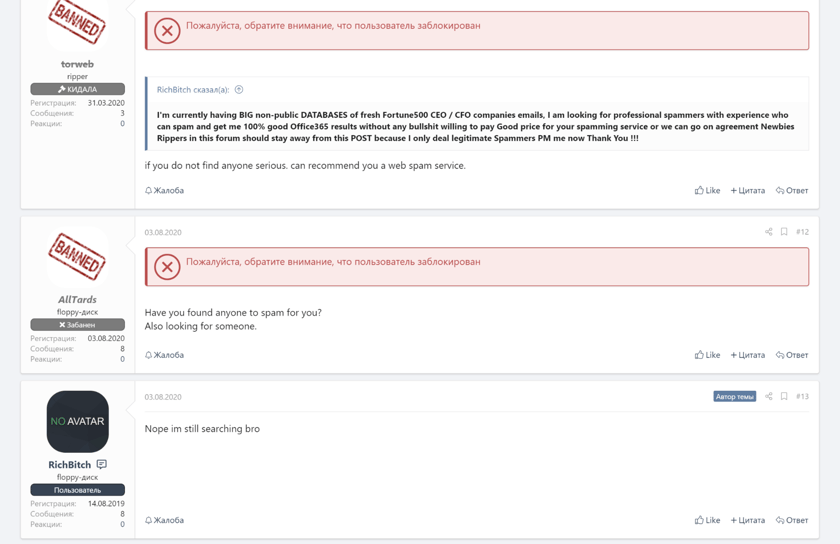
Looking for Office365 Professional Spammer Pm Me Now!
Source: https://xss.is/threads/31074/
So you might be wondering, “who are the targets of these phishing attacks?” For this hacker, they specifically call out their need for help with phishing (aka “spamming”) their large private database of CEOs and CFOs using Office 365.
Interestingly, it seems good help is sometimes hard to find in the underground business email compromise market. 🤷🏻♂️
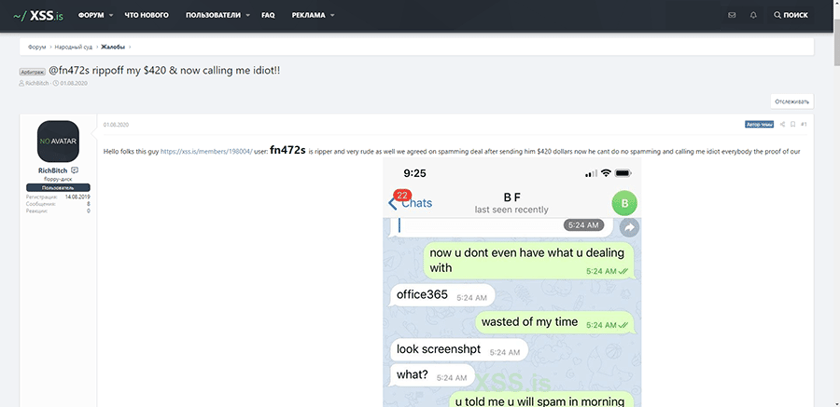
@fn472s rippoff my $420 & now calling me idiot!!
Source: https://xss.is/threads/40292/#post-247905
For that hacker targeting CEOs and CFOs, it appears their hunt for a phishing expert continued to sour. As highlighted in the screenshot below, the hired help received a $420 payment but allegedly never followed through with the goods.
Although the average person may be quick to conclude “there’s no honor among thieves,” we’re going to hold our judgment until the hacker forum formally announces its verdict in their People’s Court system. 🤣
Not only are hackers getting better at their tradecraft, their skills are becoming more and more accessible to other bad actors. And as attackers continue to innovate, scale and commercialize their operations, it’s more important than ever that we step up our defensive game.
We sincerely hope you enjoyed this brief overview of the ever-maturing threats targeting businesses. Although we fully expect underground markets to continue growing, attacks on your business don’t have to spell disaster. Just like preventive medicine, early detection and swift response actions can enable your IT department to quickly address security incidents before the situation becomes terminal.
Looking for help with detection, response and recovery? Try out Huntress in a free trial.