Endpoint Detection and Response (EDR) is simply named, yet it’s anything but simple when trying to understand the variance, capability, and efficacy of EDR solutions in the market. In this blog, we’re going to try to cut through some of the noise and shed some light on what EDR is, and more importantly, what it means to us here at Huntress and how our Managed EDR solution gets the job done.
Emerging Visibility Gaps Necessitated EDR
Taking a quick trip down memory lane, most security stacks revolved around network monitoring and antivirus (AV) solutions to provide the needed overlapping coverage to detect threats in the network. It became too apparent that adversaries were bypassing AV and the increased adoption of encryption over the network reduced protocol and content visibility.
Around this time the emergence of cloud computing and the explosion of Machine Learning (ML) tools aided in the creation of the Next Generation Antivirus (NGAV) solution. Additionally, this also brought about the first EDR solutions to the market. The observation, collection, and storage of endpoint telemetry could now be done on an economic scale that was not previously feasible.
Why EDR If NGAV is Better at Prevention?
This is a valid question and one we hear a lot.
Traditionally, AV relied on static signatures that would match indicators associated with known malware. NGAV solutions make use of trained models to make predictions. These models represent the means by which it was trained to recognize patterns without the explicit use of code to tell it what to do. Essentially, the model was given training data to learn from using various statistical methods.
Once a model was trained, it would be tested against a control set of data that wasn’t labeled. The trained model is then measured by the accuracy and efficacy of its produced predictions. Hopefully, you’re starting to see the benefits of ML in this use case. We can detect variances of malware based on previous observations of all malware in the training set. The better the quality of data that is added to the model, in theory, the better the prediction.
What better way to get some insight into what machine learning is and its inherent areas of weakness than to ask it itself? Enter ChatGPT:
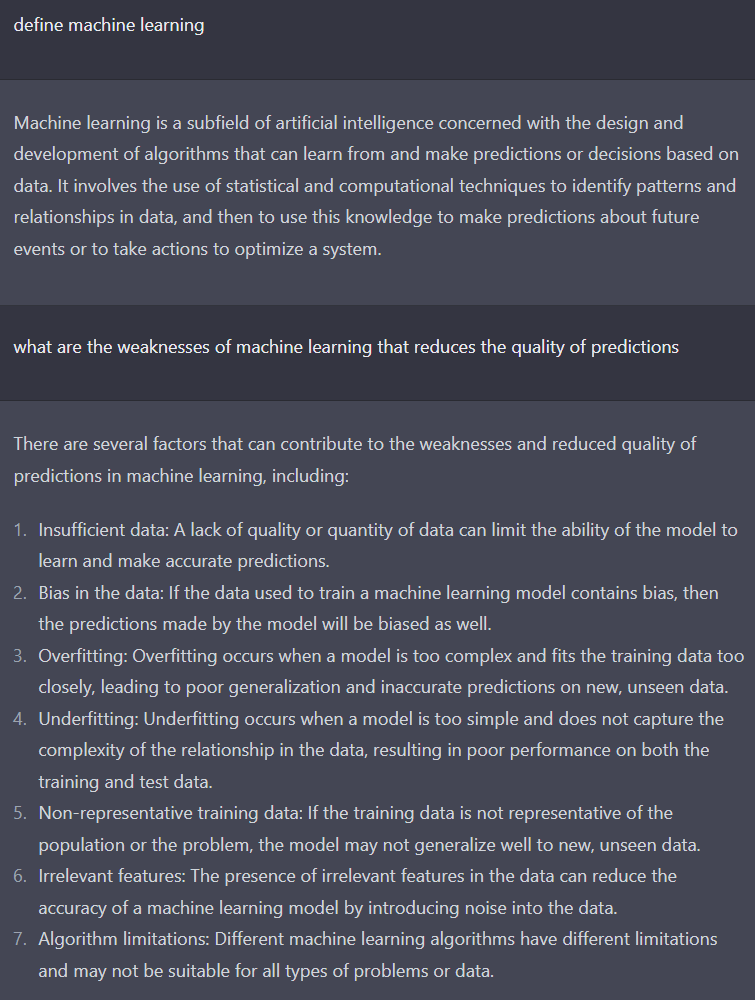
So this sounds great; we can scale our detection based on historical observations and statistical deviations! So again, why EDR?
- We’re attempting to use technology to combat human ingenuity. Humans write (at least for now) the malware that is deployed and used against us. Every control or mitigation put in place will be researched, reverse-engineered, and negated with enough investment on the part of the adversary. This creates deviations from what is expected and/or previously seen. Humans will continue to think outside the box.
- Because we’re dealing with consistently new territory, AV and even NGAV start to fall short. If you recall, models and signatures are trained and built on known behaviors and patterns with the ability to detect suspicious deviations from those behaviors. This in and of itself is the ultimate weakness with signatures and models - adversaries adapt and employ new techniques and methods that we do not always have an understanding of until after an incident.
- AV and NGAV attempt to make a decision during key points in the malware deployment/execution lifecycles. The first is when the file is written to disk and the second is when the API call is made to start a process. The AV solution in these instances will investigate the image on disk and process it at these points of interest and make a decision. The problem here is that once the decision is made, the AV solution moves on to other tasks. Once AV is evaded, adversaries for the most part have free-range access.
- AV detections are a SYMPTOM of the problem. Because your AV or NGAV solution successfully stopped a malware infection does not mean it's back to business as usual. Adversaries will try again and again until they succeed. We’re now talking about detections, priority, analysis, inference, and decision making and–depending on your network size and available triage resources–alert fatigue.
- EDR provides context before, during, and after an AV/NGAV detection that allows for more in-depth risk analysis and root cause assessment of the attack vector employed. AV solutions know a lot about a few milliseconds of activity and quickly lose value when the questions “when,” “where,” “why” and “how” are brought up regarding the left or right of the AV alert timeline.
EDR Collection, Analytics, and Analysis
EDR is, first and foremost, a collector of telemetry that can either be extracted from the host to an external appliance or cloud infrastructure. Some EDRs keep all their telemetry on the endpoint which can put that data at risk of encryption from ransomware, modification/deletion by adversaries, or loss of data due to a logical or physical failure of the host itself.
EDRs by nature are more adept at identifying and detecting interesting behaviors seen on the host as they monitor many data points over time. Adversaries may be able to bypass AV/NGAV, but they’ll still run commands, modify files and the registry, and make additional external and internal network connections.
The temporal awareness of EDRs enables us to observe and “detect” behaviors to create signals in the noise. Not only can we detect malicious or suspicious events, but also those that are normal or benign yet provide value into the development of host, user, and process behaviors. These are very beneficial during host triage and incident response activities.
Advanced adversaries capable of evading AV and even some EDR collection methods still leave trails of evidence that can be captured and analyzed to provide insight into host deviations that warrant human intervention and investigation. Huntress does this through the collaboration of our capability development, detection engineering, threat hunting and SOC analysts to detect and respond to both known and emerging threats every day.
What Does Huntress’ Managed EDR Collect and Do?
This is not an exhaustive list of data points collected and analyzed but provides a holistic view of the types of data that are collected on our customers' behalf to hunt, detect, and respond to events in our monitored networks. Additionally, there are some early teasers on what new capabilities are coming to our Managed EDR in the next few months.
|
Telemetry/Feature Type |
Details |
|
Process Events |
Visibility into the characteristics of running processes, their commands, lineage, and details about their state, privilege, and additional process attributes related to the system and user interaction. |
|
User Events |
Insights into user logon events, methods of logon, process and application events associated with the user. |
|
File Events |
Create, Read, Update, and Deletion (CRUD) events for monitored host files. |
|
Registry Events |
Survey of registry and key/value states to support configuration, status, and abuse of the registry. Very soon our EDR will have registry monitoring similar to our file monitoring capability: Create, Read, Update, and Deletion (CRUD) events for monitoring keys. Q2/3 2023. |
|
Network Events |
Detailed logging of network connections, states, ports, and protocols with directionality and flow rates i.e. bits and bytes upload/download. Currently in early testing and expected for wider release in Q2 2023. |
|
Autoruns |
Surveyed forensic extraction and analysis of known, unknown, and malicious persistence mechanisms on the host. Additional visibility of these events is gained through process, file, and registry telemetry. This is also the core capability of what Huntress built its reputation and service delivery around. Look how we’ve grown! |
|
Host Surveys |
Beyond event-driven monitoring, Huntress employs surveys on the host to gain insight into the state and configuration of a host to both help with delivering the service and hunting for indicators of compromise. |
|
Utilizing a playbook from deception techniques, ransomware canaries are hidden files that are monitored for tampering and abuse that provide a signal indicating the host is potentially compromised and may be a victim of ransomware. Our canaries enable us to act fast and isolate targeted hosts or even the organization depending on the scope and severity of the intrusion. | |
|
Tasking |
Our ThreatOps Center utilizes agent tasking to collect data from hosts under investigation to enable deeper forensic insights during manual analysis. |
|
Remediation |
Using our tasking framework, our ThreatOps analysts and analytics empower customers with one-click remediation actions on compromised hosts. |
|
Managed Detection and Response (MDR) |
Huntress utilizes a dedicated Detection Engineering & Threat Hunt team that works around the clock to research, hunt, and scale the detection of our findings across all customers. This team is affectionately called the DE&TH team. Our telemetry is aggregated at scale in our secure cloud where we deploy custom detection logic and analytics to make sense of the noise on our customers’ behalf and to further empower our internal ThreatOps analysts to deliver value every day. |
Let’s Dispel Some Rumors
Hopefully, this blog was able to provide some context around what EDRs do with respect to their close resemblance to AV/NGAV solutions. They may collect a lot of the same data, but how it’s extracted, stored, and analyzed are the key differentiators here.
With that said, it’s probably a good time to tackle some rumors or myths we’ve heard from our partners and customers with regard to “Huntress’ EDR.” Some of these are innocent questions that are more than warranted and deserve a solid answer, but some come from confusion put into the market by our competitors and we just hope that going forward this helps reduce the frequency of these rumors and misinformation.
Rumor #1: Huntress’ EDR relies heavily on Windows Defender AV i.e. Huntress Managed Antivirus
- True to form EDR isn’t really a preventive solution, but we cannot ignore the value of preventive solutions as part of the stack. With that being said, it’s only obvious why AV/EDR has become nebulous and hard to differentiate from a feature/delivery perspective. Almost every vendor of an EDR product has a proprietary AV solution that bundles with that capability (for an additional cost). Huntress’ Managed EDR DOES NOT rely on Microsoft Defender for detection, behavioral monitoring, tasking, and remediation. It is an additional preventive measure integrated into our platform (at NO additional cost to our customers). Again, the list of Huntress’ Managed EDR telemetry collected and features above does not make use of or mention a reliance on Microsoft Defender.
Rumor #2: Huntress’ EDR is not a real EDR
- I think this perception can be related to the first myth. We deploy collection and forensic monitoring to endpoints to detect and respond to a myriad of suspicious and known threats in our monitored customer networks. While there is definitely an efficacy variance between vendors and what they focus on or value most in their product, our managed EDR is very much that, an EDR.
Rumor #3: Huntress’ Managed EDR isn’t reviewed by real human analysts
- While we’re fans of Artificial Intelligence and Machine Learning, it’s just not to the level of replacing the context-building capabilities of humans. Black box analytics do great at detection, but we’ve been talking about detection for 20+ years in the security industry. Humans, who are empowered with technology that can additionally provide input into improving that technology (did you know we built 100% of our security stack??), are the secret sauce that’s not so secret. We utilize true 24-hour security ops via follow-the-sun hiring and point of presence. No exhausted analysts working the swing shift here.
Closing the Hood
Huntress is all about sharing knowledge and breaking down the topics that may evade certain groups of individuals due to jargon or complexity, but we also want to make sure we cater to those that seek the heavier content. We love hearing from our community, and in fact, this blog was written as a response to actual user feedback wondering how it all works on a more technical level. We sincerely hope that this breakdown of how our EDR functions on a more granular level has been helpful.
















