If you’ve been following Huntress for a while, you already know that historically, our place in cybersecurity stacks has been to catch the threats that other preventive tools miss.
When our founders brainstormed the concept behind Huntress, the cybersecurity space was jam-packed with tools designed to keep attackers out. To be fair, in years past, a solid firewall, good antivirus, email filtering and DNS filtering could keep most businesses fairly safe. But the focus was almost solely on prevention, which—as we all know now—is only part of the cybersecurity battle.
There were few tools to help businesses react once attackers made it past those preventive tools. And that's why Huntress came to be—to help small and midsized businesses (SMBs) survive cyberattacks.
At the time, Huntress filled a need that many businesses overlooked: a safety net to fall back on if and when the worst happened.
But things are different now.
Endpoint detection and response (EDR) has become just as important as having a game plan for when bad actors sneak into your environment. This integrated endpoint security solution detects, investigates and responds to cyber threats. Being able to actively monitor endpoints, collect data for analysis, alert quickly when a threat has been detected, and assist with remediation are just a few of the benefits of EDR.
It’s a feature our partners have been requesting—and it’s a feature we’re proud to offer to the SMB market.
Clear Guidance Partners
One of our partners who's been on the hunt for a solid EDR solution is Clear Guidance Partners.
They're a Texas-based managed service provider (MSP) that partnered with us in 2019 to add an extra layer of cybersecurity to their offerings for their clients.
Over time, they realized that to keep pace with today’s attackers, they needed to add a layer that included a managed EDR service to their stack. But a solid solution that truly delivers on its promises at a reasonable price point is hard to find in the EDR space.

Enter Huntress Managed EDR
While Anthony was researching managed endpoint detection and response capabilities, the Huntress team was doing their own research. That research ultimately led to the development of Huntress Managed EDR.
This feature enables our partners to evict hackers from their environments faster with near real-time EDR and unparalleled visibility and detection of advanced threats. It helps our partners…
- Understand threat actor behaviors and motives by mapping malicious or suspicious processes to the popular MITRE ATT&CK framework
- Identify actively exploited systems, including tracing back to cause
- Capture threat actor activity that happens between the initial access to a device and the eventual desired impact (e.g. ransomware, data theft, etc.)
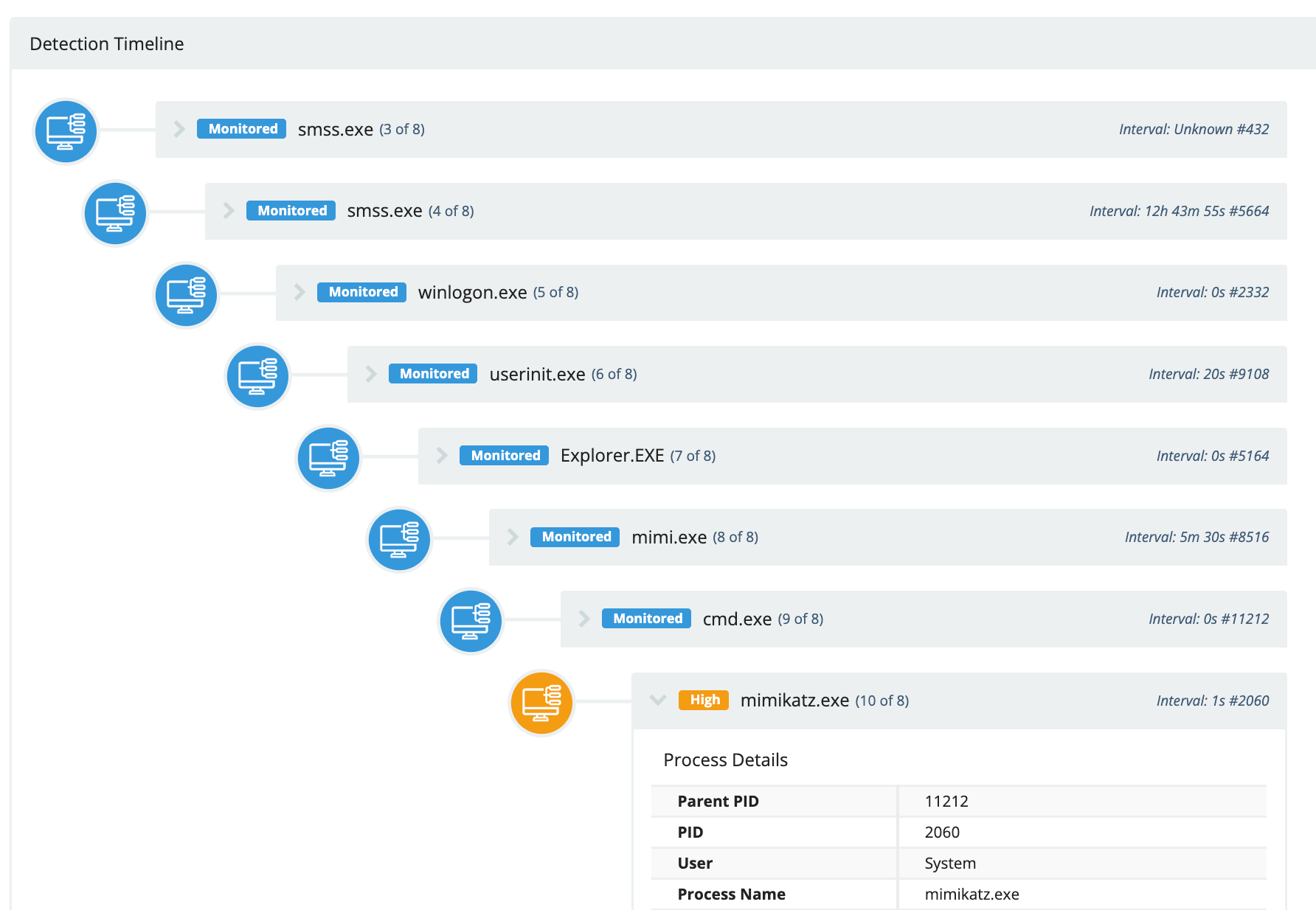
And in the event of an incident, our SOC analysts will use Huntress Managed EDR to conduct near real-time forensics and hunt for threats in our partners’ networks.As one of our partners, Anthony and his team were a few of the first to know about Huntress Managed EDR. Once the feature entered public beta in February 2022, Anthony was eager to roll it out to his client base.

And as fate would have it, Anthony and his security team rolled out Huntress Managed EDR just in the nick of time.
Huntress Managed EDR vs. An Active Ransomware Attack
One of the capabilities of Huntress Managed EDR that we’re most excited about is that it can conduct near real-time forensics through monitoring process executions and associated metadata on endpoints. As a result, our 24/7 SOC team has the threat intelligence to spring into action faster than ever before.
While our SOC team was investigating abnormal traffic and suspicious activity happening on some of Clear Guidance’s partners’ networks, Anthony was investigating alerts that were popping up from his antivirus about attempted trojan installers on those same clients’ devices.
With the news of confirmed malicious activity to share, Huntress SOC analysts immediately got in touch with Clear Guidance to verify their suspicions of a cyberattack and provide personalized remediation steps, which included activating Huntress’ Host Isolation feature to isolate the infected hosts and prevent further access for the bad actors.

Once the infection was contained, Clear Guidance was able to purge the bad actor from the network and help their clients resume normal business operations within 30 hours of the attack.
Watch the video below to hear our interview with Anthony from Clear Guidance Partners as he recounts the attack in his own words.
Post-event Analysis
Huntress Managed EDR collects forensic data to take responding to threats a step further. This forensic data enabled Anthony and our SOC team to work backward and identify the attacker’s point of access. As it turned out, stolen credentials served as the bad actor’s initial access point.
Luckily for all involved, Huntress Managed EDR empowered the Huntress and Clear Guidance teams to work together to stop this attack in its tracks.

Learn More
To read Clear Guidance Partners' full story, check out this case study. To learn more about Huntress Managed EDR, visit this page.
















