Ransomware has been around for decades, but some variants have evolved to become more advanced—finding new ways to spread, evade detection, encrypt files and even coerce users into paying up.
To combat this, Huntress developed a Ransomware Canaries service two years ago. Ransomware has evolved quite a bit since then, so we figured it’s about time for our own evolution, too!
What’s New with Ransomware Canaries?
Just in case you’re new to Ransomware Canaries, these are simply small hidden files that sit quietly on an endpoint and are continuously monitored for changes. Similar to the “canary in the coal mine” concept, Ransomware Canaries help to quickly alert us if and when ransomware has encrypted data on a machine so that an investigation can begin, triggering an earlier response to the incident.
For our latest service update, we have two main goals:
- Empower partners to own the security conversation with their users
- Increase our visibility surface for better detection and efficacy
Let's dive in!
Owning the Security Conversation
As you might know, the Ransomware Canaries v1 service used canary files hidden on the user’s endpoint. However, we suspected that more curious end users might eventually come across a canary file. Because of this, we decided to include information and follow-up instructions to help end users self-educate.
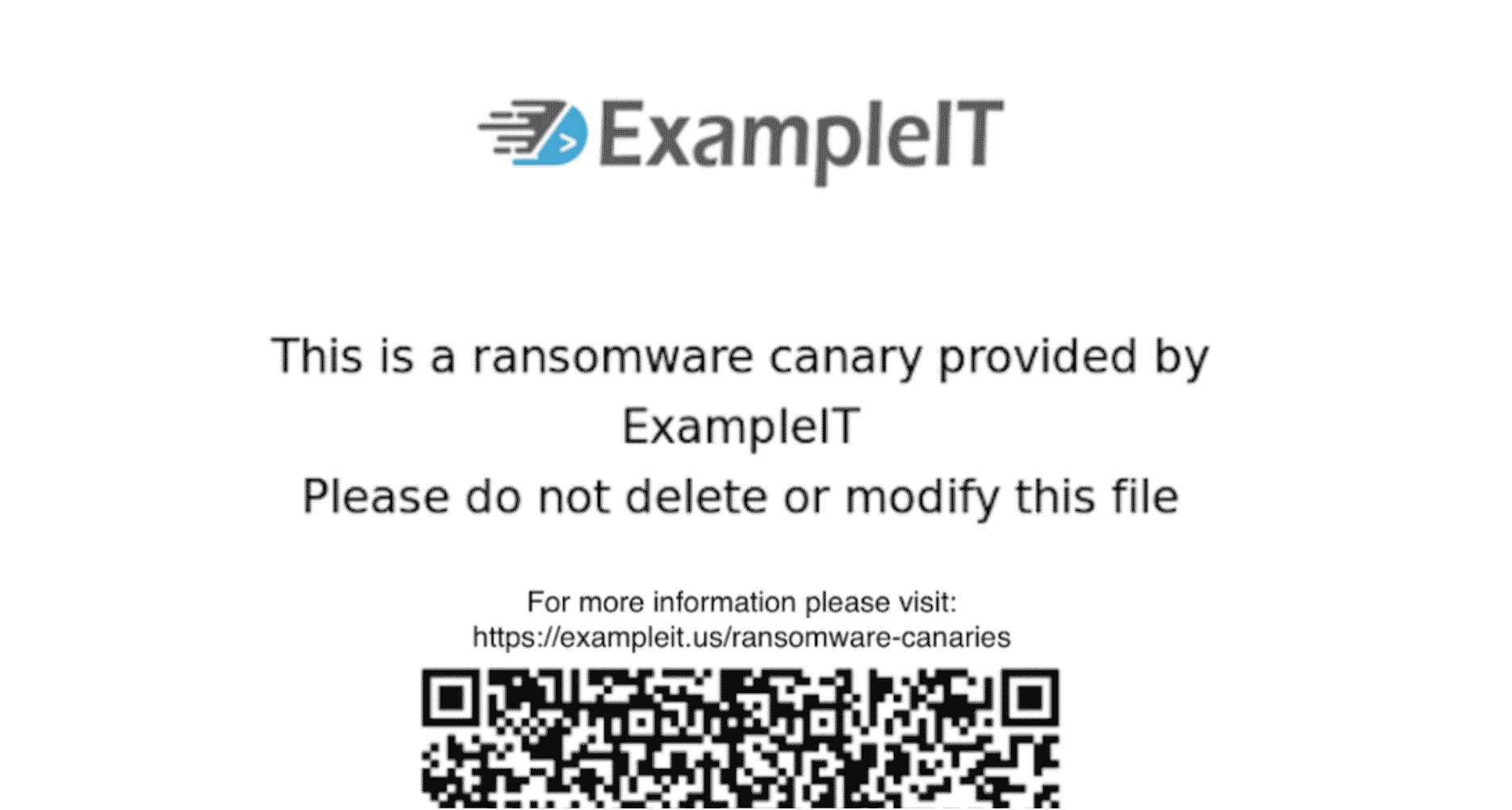
These v1 canaries embedded a helpful “this is a canary file” message and a QR code linked to our Huntress support page—providing an explanation of what it is, what it’s used for and how it adds to their cybersecurity stack.
Thanks to user feedback, we learned that end users actually did run into these files—more often than expected. And since these users mostly interacted with IT support teams or managed service providers (MSPs), opening up a canary that redirected to Huntress often created more questions than it answered—resulting in extra support tickets and inquiries.
To return the IT security conversation to our partners (so they can showcase the value they bring to clients), we added branding capabilities to canary files. So, if an end user bumps into a canary file, they’ll see their own company’s logo first and then be directed to its respective support page.
Increasing the Visibility Surface
When we started with Ransomware Canaries v1, we wanted to test out the viability of the solution from end to end. We started small and focused on .docx canary files placed only within user profiles. Coupling with our ThreatOps analysts, we were able to distinguish between when a file is tampered with (specifically due to ransomware encryption) versus when the file is undergoing a change due to end user behavior.
Fast forward to today.
The visibility we’ve put in place has been helpful, and we’ve successfully been able to detect indications of endpoint encryption due to ransomware. But we want to continue to expand our visibility further.
A big part of this new Ransomware v2 rollout is adding the following capabilities:
1. Additional canaries with new file types—specifically .xlsx and .pdf canaries
Adding canaries with different file types expands our visibility and file intrusion detection capabilities. For example, there might be a potential scenario where a ransomware variant only encrypts PDF files instead of Word documents. Now, we can keep tabs on both scenarios.
2. Canaries monitored within the system profile
Expanding canaries into the system profile affords visibility into ransomware that might be encrypting files at the system level (as opposed to the user level).
3. Encrypting File System (EFS)
EFS allows data encryption at a user profile level so a user can decide to end-to-end encrypt a specific file or directory so that only they have access to it. Our v1 iteration of Ransomware Canaries revealed that we couldn’t distinguish between files encrypted due to EFS and files encrypted due to ransomware. This hindered our visibility into Ransomware Canaries.
However, our v2 iteration allows us to distinguish between when a file is encrypted due to EFS and encrypted due to something else potentially malicious, reducing false-positive reporting in these scenarios.
We’re excited about how our Ransomware Canaries capabilities are evolving! Like we’ve always said, as long as hackers keep hacking, we'll keep hunting.
• • •
To learn more about our new Ransomware Canaries features, visit our support page. You can also see Ransomware Canaries in action by starting a free trial.