Huntress has been hunting malicious actors across 50,000+ user accounts for 1,500+ small businesses enrolled in our Managed Identity Threat Detection and Response (ITDR) product. As ITDR for Microsoft 365 moves into general availability (GA) soon, we wanted to shine a light on some of the interesting incidents we’ve identified during our beta phase.
This blog is kicking off a new series covering the tradecraft around business email compromise (BEC) and how our ITDR for Microsoft 365 product provides expert threat analysts with the data they need to find and remediate threats.
Read Part Two: Threat Hunting for Business Email Compromise Through User Agents
Setting the Stage
The cybersecurity landscape is evolving and creating new challenges for Managed Service Providers (MSPs). During the Huntress Managed ITDR beta, one participating MSP encountered three business email compromise (BEC) attacks within 72 hours, affecting three individual client environments.
For this MSP, the three clients that were targeted fell into the following industries:
- Law Firm
- Building Contractor
- Retail Store and Distributor
This series of back-to-back incidents highlights the widespread and frequent nature of Microsoft 365 compromises that MSPs are facing today.
The Common Theme: Inbox Rule Manipulation
Adversaries abuse email inbox rules to siphon sensitive information away from the victim and deny the victim access to critical information. Malicious rules that forward emails to unused folders like RSS Feeds, Deleted Items and Conversation History allow the adversary to control what the victim can see and respond to.
Ultimately, this minimizes the chance of a victim discovering that they have been compromised until actual damage occurs. Once an attacker has access to an employee’s account, they can abuse that access to facilitate invoice scams, banking fraud, phishing of other employees, data theft and more.
The Law Firm
An employee of a law firm was targeted on June 21, 2023. The threat actor proceeded to create a new inbox rule named `...` which redirected emails from a specific employee of a national auto insurance company into the RSS Feeds folder. This is noteworthy as the law firm specializes in automobile-related cases.
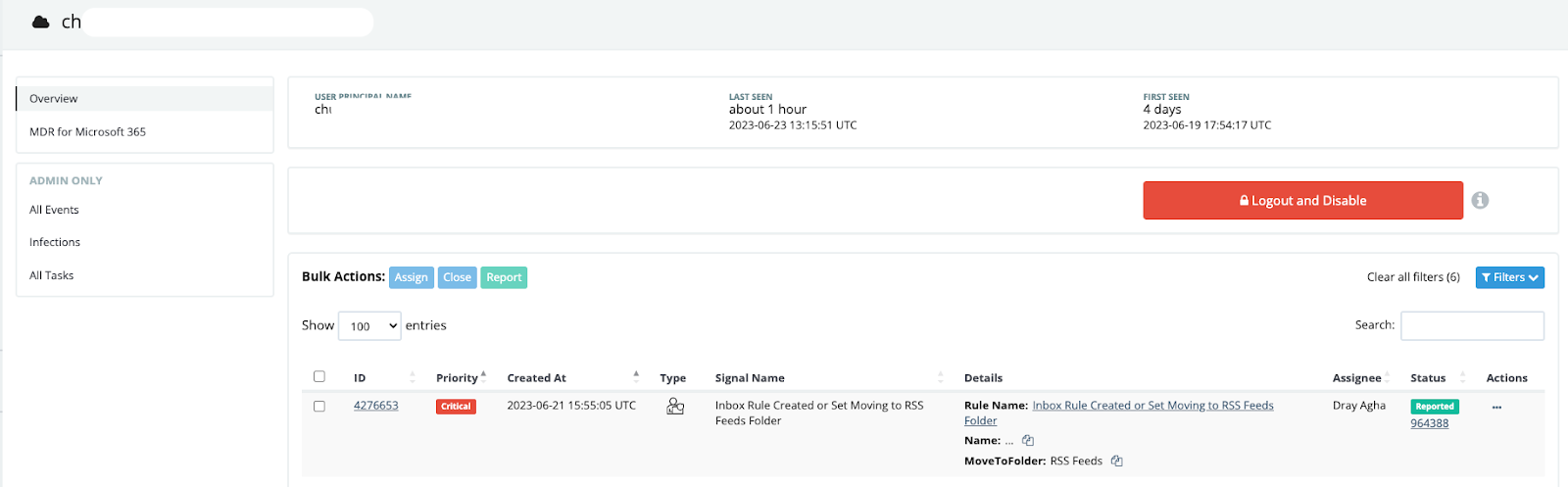
Prior to the inbox rule that redirected emails into the RSS Feeds folder, Huntress identified the following activity:
- The law firm employee logged in from both Michigan and New York in quick succession
- The user appeared to log in with two distinct User Agents, indicating that the account was authenticating from multiple devices, which can be seen in the below log data and in the CyberChef Diff output

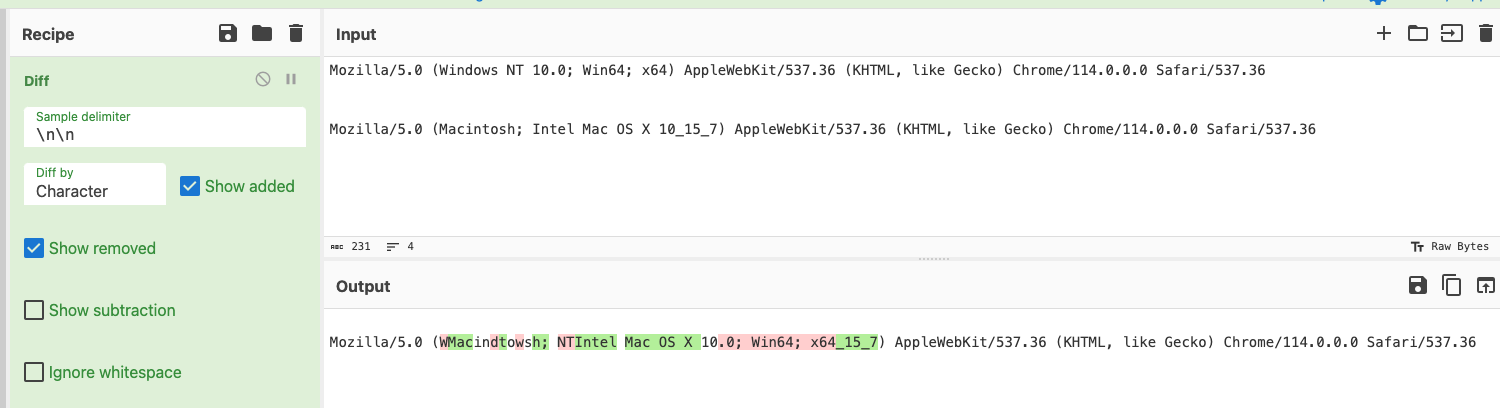
These events contextualize the inbox rule manipulation as malicious, and Huntress issued a report that subsequently locked out the law firm employee’s user account and notified the partner of the compromise.
The Building Contractor
Huntress responded to an alert on June 22, 2023, involving the user account of a contracting firm that manipulated inbox rules—similar to the previous case—in this case naming the forwarding rule `xx`.
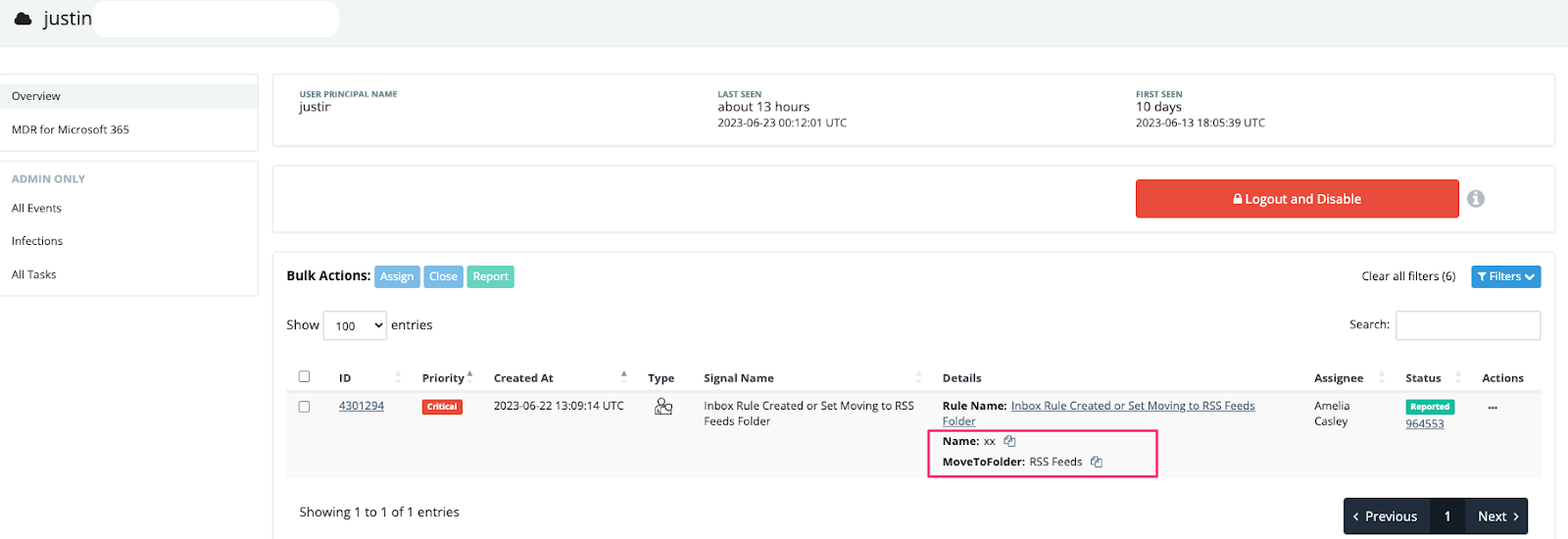
Upon reviewing the configuration of the new forwarding rule, there are no parameters other than the rule name and the folder to move to (RSS Feeds). This resulted in all emails being sent automatically to the RSS Feeds folder for this user.
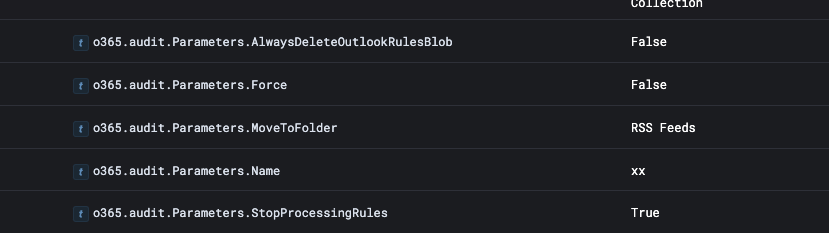
Digging deeper into the data, we can see that the user consistently signs in from the same places, with the US state of Virginia being an anomalous location.
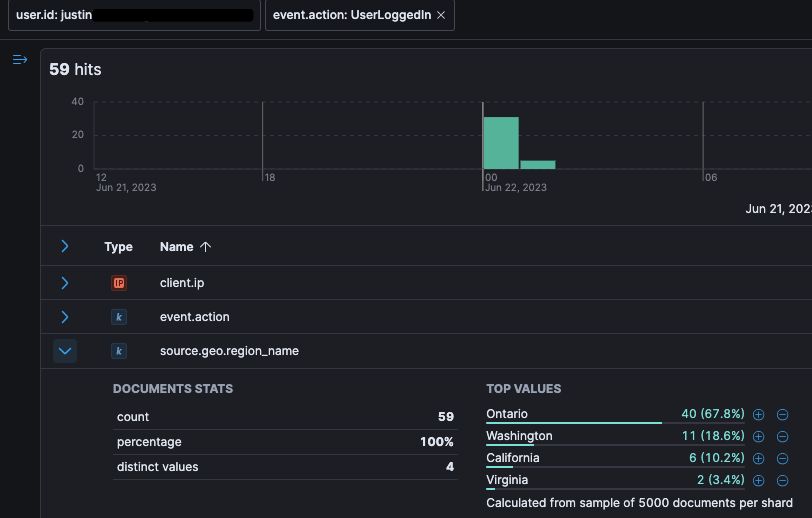
When filtering on user actions taken from Virgina, we quickly correlate the anomalous location with the suspect RSS Feed forwarding rule.
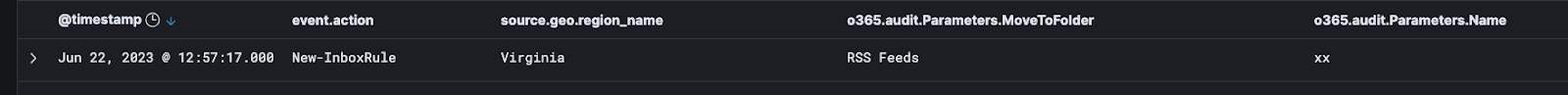
With the above contextual information, the Huntress SOC issued a report advising the partner of email compromise, locking out the account, and ultimately removing the threat actor from the Microsoft 365 instance.
The Retail Store
The details for this intrusion targeting several employees of a retail store and distributor are slightly more complex, but it features inbox rule manipulation as a component of overall permissions abuse in Azure. This comes after a threat actor gained access to an account with full administrative permissions.
- The store employee did not have mandatory 2FA authentication, and initial malicious activity was seen while the user was logged in via a Nigerian IP.
- In quick succession, the employee’s account had a successful login via an IP geolocated in Ireland, indicating probable proxy usage.
- The account went on a spree of assigning themself permissions and privileges, granting themself full access to the mailboxes of other users.
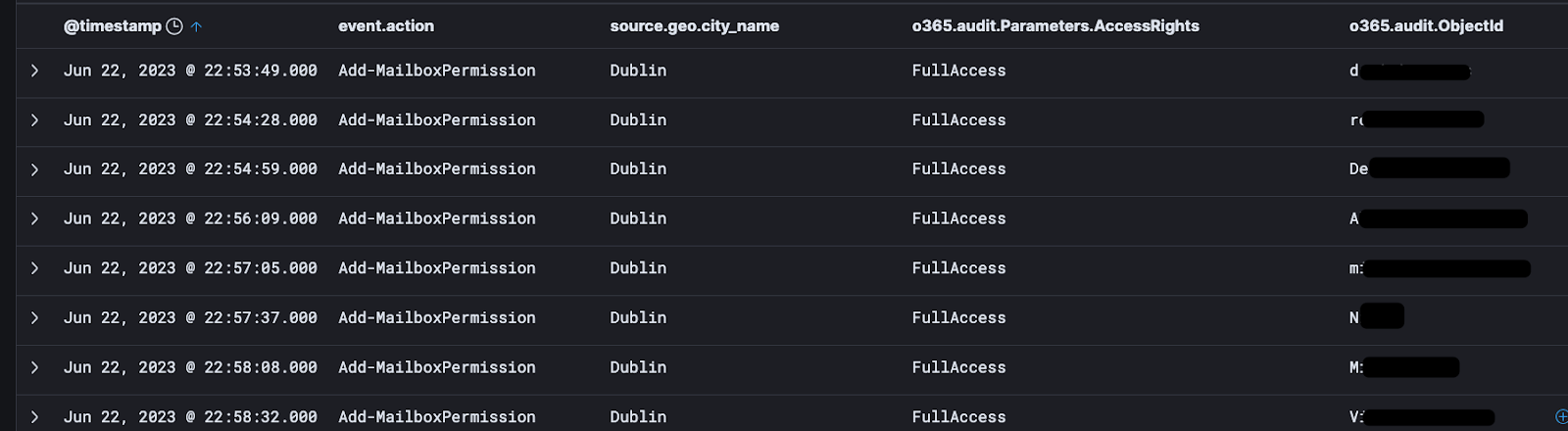
- Throughout the attack, the adversary continued taking additional actions while moving between the Nigeria and Ireland proxies.
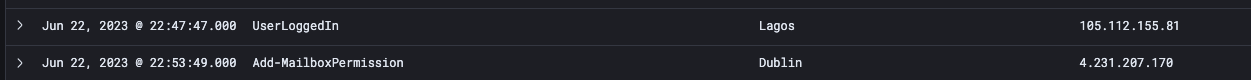
- Finally, the attacker manipulated inbox rules for multiple employees of the company.
- The adversary created a rule to push emails from specific construction and car rental companies into the Conversation History folder.
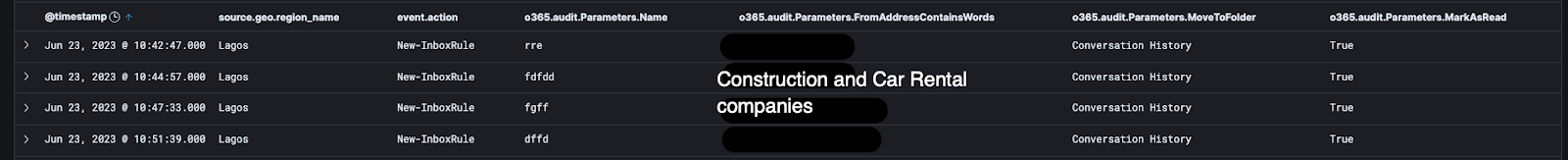
- The purpose of these rules is likely to achieve invoice manipulation, where the legitimate invoices would never be seen by the desired employee. This allows the attacker the ability to swap in a spoofed or modified invoice, which directs payment to the attack-controlled bank account.
Parting Thoughts
MSPs face a significantly expanded attack surface in the cloud as they take on the responsibility of managing and maintaining infrastructure for multiple individual companies, each with their own unique business requirements. This broader scope of operations introduces challenges for MSPs as they strive to define what constitutes "normal" for each client.
In this case, our Managed Identity Threat Detection and Response solution enabled us to identify and respond to an MSP that faced three attacks across three customers in only three days. BEC attacks are a rising trend and are incredibly lucrative for attackers—but thankfully, you’re not alone in the hunt for business email compromise.
Special thanks to Faith Stratton (@f0xtrot_sierra), Dray Agha (@Purp1eW0lf), Sharon Martin, Rich Mozeleski and Max Rogers (@MaxRogers5) for their contributions to this blog post.
















