







Our team is currently investigating new 0-day vulnerabilities in Microsoft Exchange servers that could lead to Remote Code Execution (RCE) for an authenticated user.
Our ThreatOps team discovered this blog, and the team began to research and see if anyone else in the community had flagged it. We found this tweet from Security Researcher Kevin Beaumont, where he notes that “significant numbers of Exchange servers have been backdoored - including a honeypot.”
We’ll continue to update this blog with our latest findings and research.
Update 1 (9/29/22 @ 8:18pm ET): Clarified GTSC updated language to affirm this is a new vulnerability and 0-day.
Update 2 (9/30/22 @ 9:23am ET): Included Microsoft official details and CVE identifiers.
As of 9/29/22 @ 8:18pm ET, the GTSC has been updated to reaffirm that this is a new 0-day vulnerability and Remote Code Execution exploit. Unfortunately, this means that the latest patch and Cumulative Updates are not sufficient to protect Exchange servers from this threat. Currently, there are no known proof-of-concept scripts or exploitation tooling available in the wild.
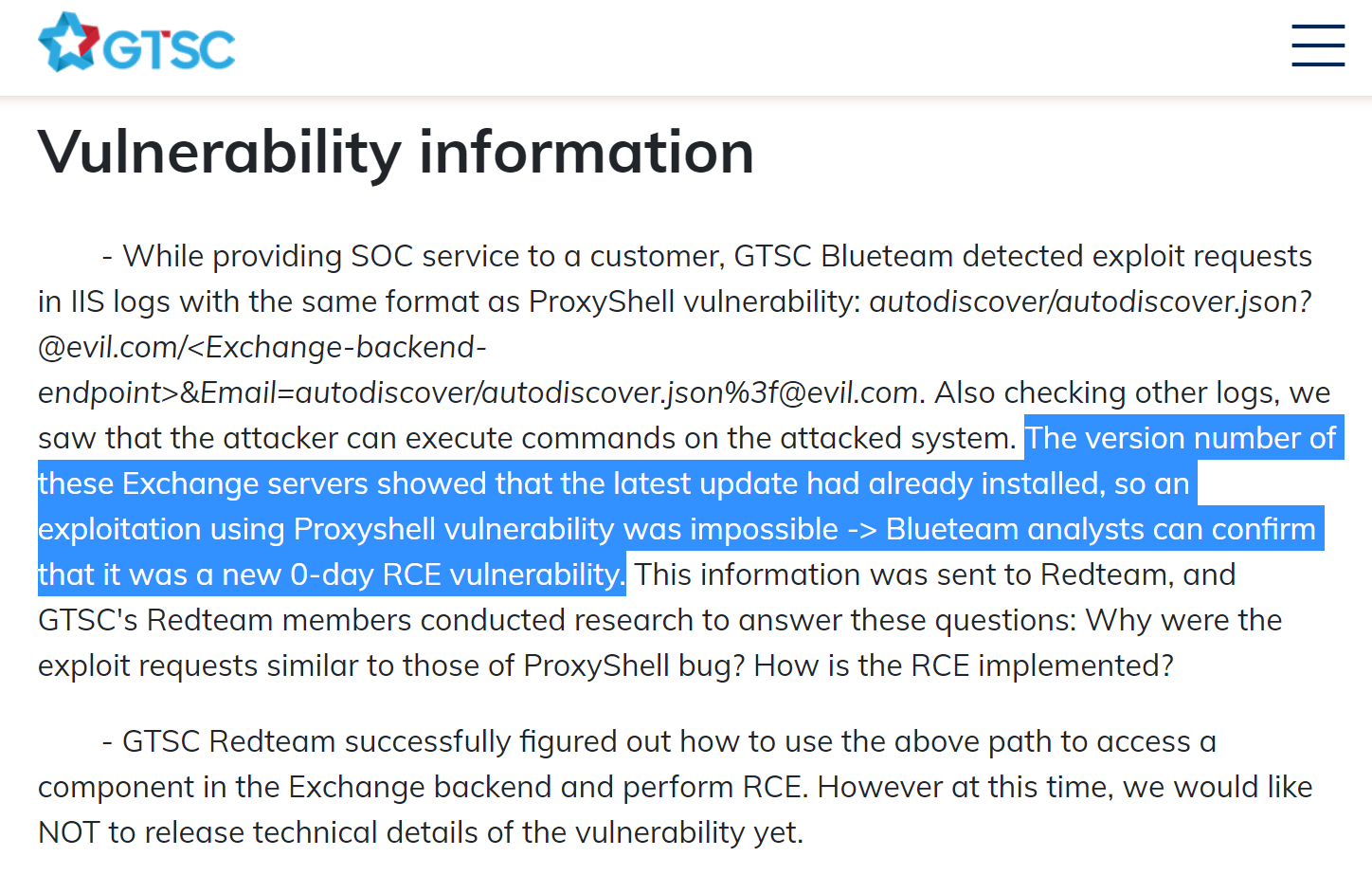
The best thing you can do right now is to follow the containment steps outlined in GTSC's post.
As another resource to monitor, the Zero Day Initiative is tracking two issues related to the observed exploitation so far, tagged as ZDI-CAN-18333 and ZDI-CAN-18802.
As of 9/30/22 @ 9:23am ET, we see that Microsoft has recently offered details about this issue. They have announced there are two new vulnerabilities:
The first vulnerability can be used to achieve the second, but it must be clear that this is only an attack vector for an authenticated adversary. Currently, no official patch has been released by Microsoft yet.
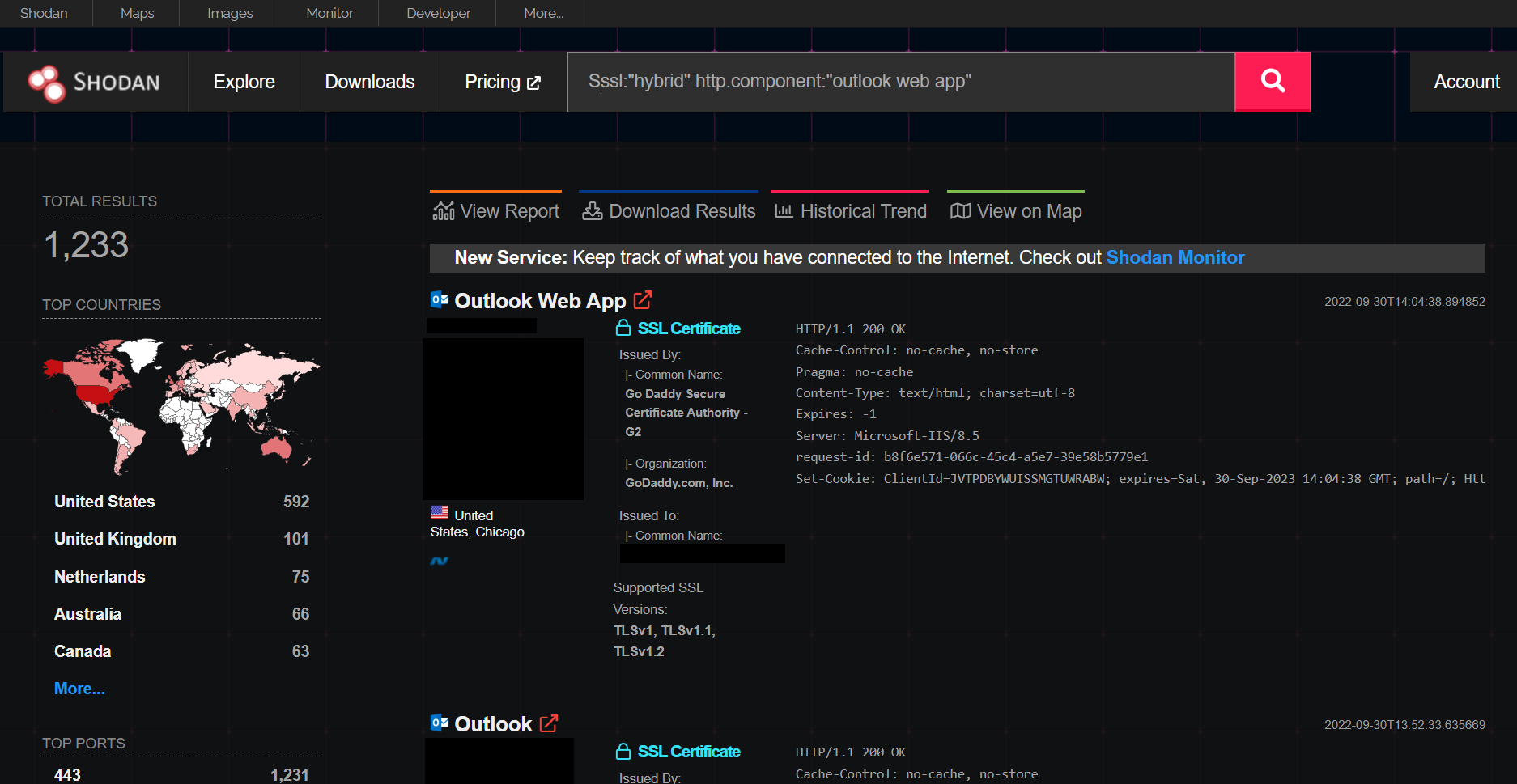
Kevin Beaumount has pointed out that there is still a risk to Exchange Online users, as a significant number may be running a hybrid server that migrated to Exchange Online and are still vulnerable to this post-authentication threat. Shodan reports over 1,200 potentially vulnerable endpoints with this attack surface.
The freely available Microsoft Defender antivirus will detect the current publicly known post-exploitation attempts as Backdoor:ASP/Webshell.Y and Backdoor:Win32/RewriteHttp.A.
We’ve got ~4,500 Exchange servers with our agent on them, and we’re actively looking into any red flags and potential signs of exploitation in these servers.
The Huntress Managed Antivirus service will notify our ThreatOps team of any of the above Microsoft Defender detections and enable our team to begin to triage and investigate. At the moment, Huntress has not seen any signs of exploitation or indicators of compromise on our partners' devices.
(Credit to this blog published by the GTSC Team)
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
