In a recent episode of Tradecraft Tuesday, I was joined by Patrick Wardle, Founder of Objective-See Foundation, to talk all about how macOS malware is evolving and what it means for security today. We hit on a few key topics surrounding macOS, such as the BTM (Background Task Management) database, the current state of macOS malware, and more.
You can watch the full episode recording here, or keep reading for a recap of all the action, plus a glossary of common macOS terms and acronyms at the end of this post.

Our conversation in its entirety tied together nicely, as it alluded to macOS persistence and how malware remains on the system, as well as how some researchers have found malware via CrashReports.
In the past, we here at Huntress have discussed persistence at length, including listing all of the persistence mechanisms familiar to macOS. Apple has since collated some of the persistence items under one roof, called BTM.
Background Task Management (BTM)
As of macOS Ventura, Apple released a new database on disk at /System/Library/PrivateFrameworks/BackgroundTaskManagement.framework/Support/BackgroundTaskManagementAgent.app/Contents/MacOS/BackgroundTaskManagementAgent. This binary plist (property list) keeps a serialized record of the Launch Items and Login Items. Launch Items, normally simply stored in one of a few locations, can now be bundled within their own applications, making them more difficult to track. Dumping the BTM database, via running sfltool dumpbtm, can show you the persistence item, its path URL, the developer name and team identifier, and other helpful information.
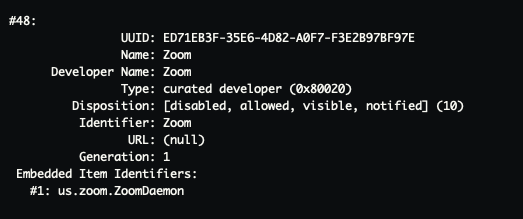
Accessing the BTM does not need to be done strictly from the command line but can be accessed through Apple’s Endpoint Security, a C API that allows developers access to lower levels of the operating system. Apple provides two different events to give visibility into BTM, the first being ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD. This event will notify if a new item is added to the BTM database, while the second event ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE tracks if an item is removed.
More information on Endpoint Security and how macOS interacts with it is available in this blog.
Current State of macOS Malware
As the amount of malware seen on macOS seemingly increases exponentially year-over-year, we start to see a whole gambit of new variants. From ransomware perpetrated by the LockBit ransomware gang in mid-April, to sophisticated nation-state malware dubbed RustBucket, to frustrating adware and search engine hijacking like Pirrit and Adload, the malware targeting macOS has become more abundant.
As Apple has updated macOS, they have included more checks into what software is and isn’t allowed to run.

Whether we talk about code signing an application, notarization status, or TCC permissions, all of these security mechanisms have been put in place in an attempt to reduce the overall attack surface on macOS. This has helped stop many different families of malware from being able to access sensitive, end-user information without explicit authorization from said user. This especially applies, in large part, to the malware that authors first deploy to Windows devices, before porting over to macOS. Simply writing malware as cross-platform, via something like the Go programming language, is not enough for overly sophisticated attacks, due to these security mechanisms.
There is a lot to see in November’s Tradecraft Tuesday episode, and the current state of affairs is just one of them. Watch the full episode for more goodness and more information about Objective-See’s free, open-source tools.
Common macOS Terms and Acronyms
When speaking about macOS, there are so many acronyms and/or terms that may be helpful to know. Whether talking about macOS security specifically, the filesystem, or some of the primary applications you’ll use, it’s always helpful to have a cheatsheet.
To help you make sense of it all, we hope the following list provides you with a one-stop shop of common macOS terms and acronyms you should know about.
- App Sandbox: provides protection to system resources and user data by limiting your app’s access to resources requested through entitlements. If you desire to have your application distributed through the Mac App Store, you’ll need to enable this feature.
- Application bundle: a common way you package applications for installation/distribution. The extension of this file type is usually .app.
- Bundle ID: a resource that represents the app's unique identifier that you can register, modify, and delete. Naming convention generally follows com.companyName.applicationName.
- Codesigning: applying a developer’s developer/team ID (see below) to an application, so people know who the owner is and not a spoofed/faked copy. Also leveraged by Gatekeeper/File Quarantine/Notarization to look for and detect malicious content.
- Daemon: a process that runs in the background, typically with “root” (i.e., administrator) privileges. The Huntress Agent would be an example of a daemon.
- Developer ID (aka Team ID): a ten-character alphanumeric string that is associated with an application (and is assigned by Apple). It’s how you claim an application as your own.
- Entitlement: a privilege that grants a program a specific capability on a Mac, such as accessing a user’s Documents directory or (in some cases) installing system extensions. The latter is an example of a restricted entitlement, which requires users to distribute a provisioning profile with our app specifying the entitlements it has been granted.
- ES (often called ESF): Endpoint Security (Framework): a low-level C API provided by Apple designed for monitoring system events for potentially malicious activity.
- File Quarantine: file quarantine is part of built-in macOS security. It assigns an extended attribute to newly downloaded files. It then moves them to a temporary folder, where it then prompts the end user if they trust the file or not.
- FileVault: Provides full-disk encryption for a user's data. Ensures that the user's data is securely protected from unauthorized access in case their Mac is lost or stolen, adding an extra layer of security to their files and information.
- Finder: similar to Windows Explorer start menu. It is an easy way to search through files, launch applications, and other basics. Similar to how the macOS Launchpad/Dock is equal to the Windows Start Menu.
- Full Disk Access (FDA): to access features such as directories with user (or sensitive) data, library directories, etc, without having to explicitly approve each directory. This is part of Transparency, Consent, and Control (TCC).
- Gatekeeper: a security feature in macOS that controls and verifies the authenticity of applications before they are allowed to run, preventing the execution of unauthorized software.
- Hardened Runtime: a macOS security feature that restricts and monitors an application's behavior. It enforces runtime protections, including code signing and runtime code integrity checks, and prevents code injection, DLL hijacking, and memory tampering.
- Keychain: a macOS app that stores your passwords and account information, and reduces the number of passwords you have to remember and manage. Stored in the secure enclave.
- LaunchAgent: a persistence item that will execute a binary once a user session has started
- LaunchDaemon: a persistence item that will execute a binary once the system starts (does not require an interactive user session)
- M1/M2: series of ARM-based systems-on-a-chip designed by Apple Inc. as a central processing unit and graphics processing unit for its Mac desktops and notebooks, and the iPad Pro and iPad Air tablets
- Mobile Device Management (MDM): enables administrators to remotely configure settings, enforce security policies, distribute apps, and secure device usage within the organization. Apple is moving heavily toward this model of security by declarative configuration. Examples of MDMs are Addigy, Intune, Jamf, or Kandji.
- Notarization: similar to codesigning, it is a security mechanism provided by Apple that involves submitting your application to Apple to be reviewed (they’re looking for malware)
- pkg: the file type of an installer. Generally contains a pre-install and/or post-install script
- Plist: a structured file format that typically contains settings, preferences, or metadata for applications. This is the file structure for LaunchItems (LaunchAgents, LaunchDaemons).
- PPPC Payload: PPPC stands for ‘Privacy Preferences Policy Control’. When using an MDM, administrators can deploy a PPPC payload (or policy). This can specify TCC permissions for applications without requiring explicit approval from the end user. An example would be giving the HuntressAgent full disk access. This is only available when using an MDM to deploy.
- Provisioning Profile: a sort of manifest distributed with third-party apps, describing, among other things, which entitlements the app requires and where it is allowed to run (for example, only on select development/testing machines, or anywhere). macOS apps do not typically require provisioning profiles, but there can be a need to include one if you are making use of restricted entitlements (see entitlement).
- Secure Enclave: a secure separate co-processor found in some Macs and iOS devices that handles sensitive operations like biometric data (Touch/Face ID) and encryption keys.
- System Integrity Protection (SIP): a system of security features that prevent modification of system files.
- System Extension: similar to the OSR driver on Windows. It’s the way you can communicate with the low levels of the operating system.
- TCC: Transparency, Consent, & Control (database on disk). This is a common location to begin troubleshooting after installation or application functionality issues.
- Unified Logging: provides a comprehensive and performant API to capture telemetry across all levels of the system
- XPC: an Apple-specific protocol for communicating between low levels of the operating system. It allows for bidirectional communication between processes.
















