Cybersecurity Awareness Month is here, and it’s an ideal time to reflect on whether your silly security mishaps have earned your photo a place on your IT team’s dartboard.
In this blog, we’ll break down user security habits that push your IT team dangerously close to launching laptops out of windows. But we’re not just here to roast your facepalm security moments.
Cybersecurity is a team sport, so we’ll show you what to do instead to keep your tech running smoothly and your IT crew sane.
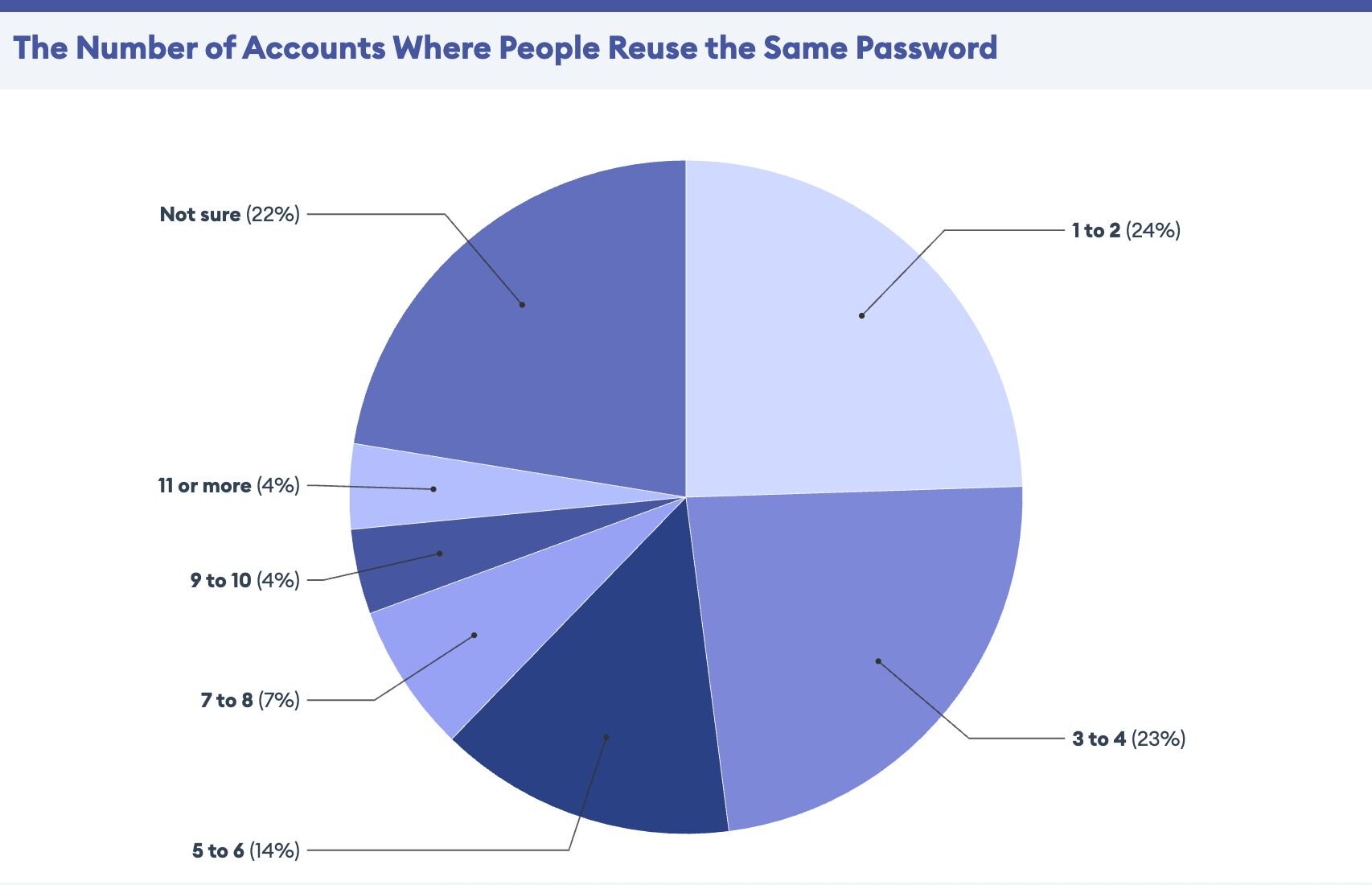
Use the same password...for everything
Congratulations! You've cracked the code to password perfection. Why strain your brain remembering multiple passwords when one beautifully crafted masterpiece can unlock your entire digital kingdom?
Because your IT team is collecting overtime since your recycled password was the source of a data breach. You’ve used it on your work laptop for personal email, banking, and social media. This gave the hacker enough initial access to get a foothold, pwn your machine, and leap from your personal accounts to business endpoints.
The reality check: When hackers figure out that one password works for multiple accounts, your entire digital footprint is at risk.
Do this instead: Use a password manager, like LastPass, to generate and store unique passwords for every account. Don’t double-dip with passwords. Most password managers automatically create complex passwords and fill them in for you. You still have to track one password, but it’s the master password to your hard-to-crack passwords in your digital vault.
Click every email link (it's probably important!)
Your inbox is a treasure trove of personal and professional opportunities just one click away!
-
The CEO needs something ASAP? No problem! Gift cards on the way.
-
There’s a problem with your account credentials? Phew, you can fix it by clicking a link in an email.
-
The perfect job, salary, location, and you’re the best sparkly unicorn candidate they’ve ever seen! Just click the link to start the application process.
-
You’ve won a trip to Hawaii! You don’t remember entering a contest, but who cares! You’re heading to a Pacific tropical paradise after you click that link!
Sleep is overrated. Your IT team loves conducting emergency response meetings at midnight, and nothing says "job security" like a good ol' fashioned phishing incident.
The reality check: Phishing attacks have evolved far beyond the obvious red flags, like messy grammar, sloppy spelling, and weird vibes from dubious princes. Modern cybercriminals send convincing messages that can fool even the most tech-savvy individuals.
Do this instead: Tell your IT team if you clicked a weird link in your email. You can also hover over links to see where they actually lead before clicking. If something seems off, navigate directly to the website through your browser, instead of clicking links from a sketchy email. Your IT team provides security awareness training for a reason, so embrace it!
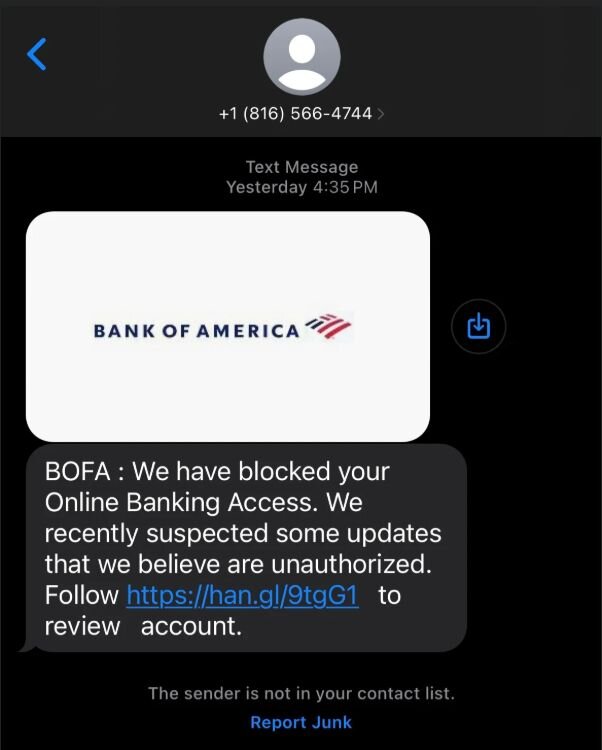
Smishing example. Don't let the use of a legit logo fool you.
Share credentials (because sharing is caring)
Team building is important. What better way to boost morale than sharing your login info with colleagues? That intern who needs access to the system for their short summer stint? Hand over those credentials and get started! Your coworker who forgot their password? It’s your time to shine, helpful password hero!
Your IT team will definitely submit you for a bonus and applaud your collaborative spirit when they explain to management how several endpoints were compromised and had to be remediated with external third-party help ($$$$), all thanks to your generous nature.
The reality check: Shared credentials make it difficult to track who accessed what information and when, creating security blind spots and compliance nightmares.
Do this instead: There's never a reason to share credentials, and it sends offenders straight to the naughty list. Work with your IT department if temporary passwords are needed. If someone needs access, they need their own authorized account.
Install software first (ask questions never)
Your computer is your creative digital playground. It’s fun to try new things that level up your user experience and work productivity, right? After all, if you see it on your work computer, it must be legit. The random toolbar that promises to speed up your browsing? And the free software from that sketchy website with 17 pop-up ads? You’ll definitely be up for a promotion after downloading these efficiency gangbusters.
Don’t tell anyone, but your IT team secretly loves spending their weekends removing malware and rebuilding infected systems.
The reality check: Unauthorized software installation is one of the fastest ways to introduce malware and security vulnerabilities while messing with compliance requirements.
Do this instead: Don’t install new software without checking with your IT team. Security-savvy organizations maintain approved software lists or have processes for vetting new applications. If you need specific tools for your work, there's usually a secure way to get them approved and installed.
Connect to public wifi (it's free for you...and hackers too)
Coffee shops are the new corporate office. Why risk cabin fever when you can do all the same work from your local café? If you use headphones and sit at a table alone, it’s totally safe. Nobody can hear your customer call or see the latest sales numbers on your screen. Need another espresso shot? Don’t worry about leaving your laptop screen open at your table while you order. And that unsecured network named "Free_WiFi_Definitely_Not_Malicious" is probably just another cybersecurity professional who likes to joke around.
Luckily, your IT team loves a good mystery, like solving for the unknown, unauthorized users who got access to your sensitive data from a public wifi network.
The reality check: Public wifi networks are often unsecured, meaning anyone on the same network can potentially intercept and steal your traffic, including passwords, emails, and sensitive documents.
Do this instead: Don’t barricade yourself in your home office, but when you want to plug in somewhere else, turn on your company's VPN. Or spin up a mobile hotspot from your phone instead of connecting to public wifi. If you have to connect to public networks, don’t tap into your organization’s sensitive info, and make sure all websites use HTTPS encryption.
Ignore software updates like you ignore the assembly manual (and hope things don’t fall apart)
Your computer runs perfectly fine right now. And you live by the mantra: if it ain't broke, don’t fix it. Those constant update notifications are clearly just Microsoft trying to slow down your machine and throw a wrench into your day.
Your IT team will be super pumped to explain to auditors why your operating system is 15 versions behind and has 47 known security vulnerabilities.
The reality check: Software updates often roll out critical security patches that fix newly discovered vulnerabilities, including zero days. Delaying updates leaves systems exposed to known attack methods that attackers actively exploit.
Do this instead: Turn on automatic updates or establish a regular schedule for installing them. Rely on your IT team to get the lowdown on which updates are critical, and how to apply them without shaking things up during your workday.
Store everything on your desktop (because folders are for quitters)
Organization is just a suggestion, not a rule. A little mess is part of the magic—you’re more productive when your desktop looks like a digital tornado touched down.
Why take time to use secure network drives when you can store client data, financial records, and confidential emails right on your local machine? Sure, they're impossible to back up or protect, but it’s so much easier to grab them when something urgent crops up.
It’s a good thing your IT team is always down for a brain teaser, like trying to recover lost data from crashed hard drives after hours and on weekends.
The reality check: Local storage means hardware failures, theft, and loss of data and documents, especially the sensitive stuff. If your digital footprint chills out on your desktop, it’s nearly impossible for IT teams to do proper backup and security controls.
Do this instead: Jump into your org's approved cloud storage or network drives for important documents. You’ll get automatic backups, access controls, and security monitoring that protect your data more than any local storage option ever will.
Overshare now (incident response later)
You’re the office social butterfly. You proudly share cool details about company projects on social media, gab about sensitive client info in public spaces, and verify your identity to helpful strangers who call asking about system access.
Your IT team appreciates how you keep things spicy by giving cybercriminals exactly what they want, with no hacking involved.
The reality check: Social engineering attacks rely on collecting seemingly innocent info from multiple sources to build convincing attack scenarios. Oversharing gives cybercriminals the details they need to trick other employees or impersonate legitimate contacts.
Do this instead: Think before you share, especially on social media or in public spaces. Be skeptical of unsolicited requests for information, even from people who seem to know about your organization. When in doubt, check identities through official channels before sharing any business info.
You don’t have to be an IT pro to make a difference
Nobody's perfect. Even the most security-conscious pros click the wrong link or forget to update their software once in a while. But what separates the squads of security aware from the unaware isn't perfection: it's the willingness to learn from mistakes and pick up better habits.
Your IT team isn't trying to make your life difficult with security policies and procedures. They're working day in and day out to protect your organization's data, reputation, and bottom line from shady, no-good cybercriminals. The best way to support them (and keep yourself out of trouble) is to treat security as everyone's responsibility, not just something the IT department handles.
Small changes in daily habits can positively shift your org's security vibe: strong passwords, a pause before you click, keeping software updated, and securely storing data. These aren't complicated ideas, but when done consistently, they get the job done.
Hackers thrive on victims’ slip-ups, so don’t make things easier for them. By developing better security awareness and habits, you're not just helping your IT team—you're leveling up your own offense game to disrupt hackers and threats that can impact your entire organization.