Apple's commitment to user privacy is well known. One of the key components of their privacy controls is the Transparency Consent and Control (TCC) framework. When observing the difference in security between macOS and Windows, there are many large, distinguishable differences, as well as some that are more nuanced.
Released in macOS Mojave 10.14, TCC is one of the primary differences when it comes to how macOS handles sensitive user data. The TCC database plays a crucial role in ensuring that users have control over the access permissions granted to applications on their devices.
What
TCC stands for Transparency Consent and Control and is a framework developed by Apple to manage access to sensitive user data on macOS. The primary goal of TCC is to empower users with transparency regarding how their data is accessed and used by applications.
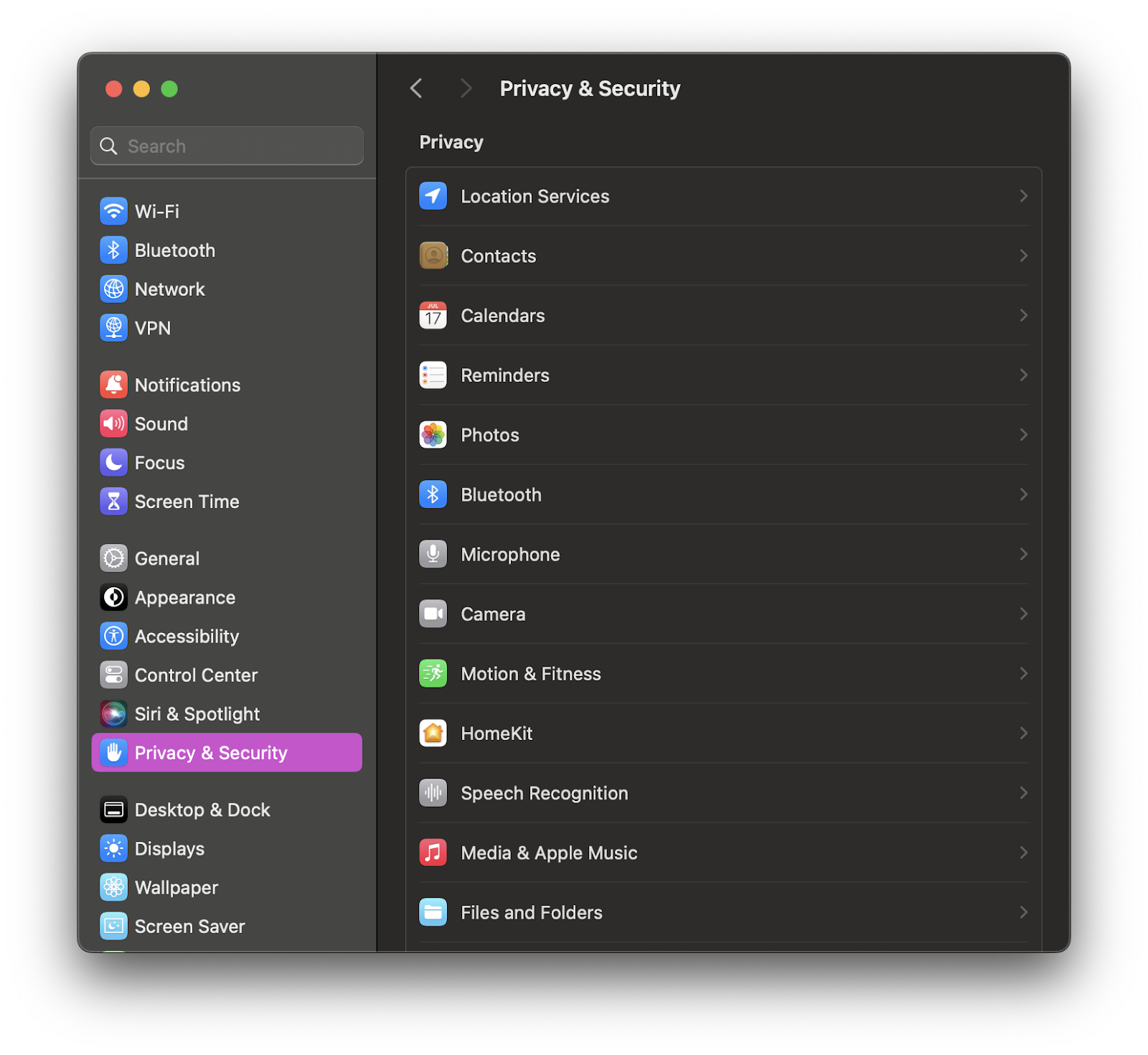
To get visibility into TCC permissions, users can navigate to their System Settings, and click into Privacy & Security. In this pane, you can see the vast majority of TCC permissions. This includes, but is not limited to, applications that have requested access to the camera or microphone, location data, and specific files and folders such as the Desktop or Documents.
Where
As mentioned, TCC is actually a database that lives on disk. There are multiple TCC databases on macOS – one per user, and also one at the root level.
~/Library/Application Support/com.apple.TCC/TCC.db
/Library/Application Support/com.apple.TCC.db
One of the primary differences between these two databases is that something like Full Disk Access (one of the more well-known permissions) is only located in the root Library. The reason is that this permission can give access to certain administrative settings for all users on the device. To grant Full Disk Access (FDA), a user will need to enter their administrator password to grant or revoke access. At this point, that change is reflected in the database located, in this case, in the root directory.
Key Aspects
Privacy & Security Preferences
The TCC framework is integrated into the Privacy & Security Preferences Pane on macOS. This setting allows users to review and modify the permissions granted to apps for accessing sensitive data such as location, camera, microphone, contacts, calendar, and more.

User Consent
TCC ensures that applications must seek explicit consent from users before accessing certain types of data. When an app attempts to access sensitive information, a system dialog prompts the user to grant or deny permission. This process provides users with control over their data and prevents unauthorized access.
Database by Design
The TCC database maintains a record of the permissions granted by the user to each application. This database includes details about the app, the type of data it requested access to, and the user's response (allow or deny). The structured database ensures that user preferences are consistently enforced across the system.
Encryption
Apple places a strong emphasis on the security of user data. The TCC database is encrypted to protect the stored information from unauthorized access. This ensures that even if a device is compromised, the user's privacy remains intact.
Sandboxing
TCC works in conjunction with the application sandboxing feature in macOS and iOS. Sandboxing restricts an app's access to the system and other applications, adding an extra layer of security. TCC ensures that apps can only access data for which they have received explicit user consent.
Troubles
Over the years, there have been some problems pop up here and there with the introduction of TCC. Now, I believe these struggles are worth it, given the value and privacy that TCC provides—however, it’s worth noting some of these difficulties for users.

For one, TCC is yet another permission that users need to take action on. Whether we talk about notification fatigue, or the troubles this can bring to software developers, this does introduce new struggles. If we discuss the installation of software, on an individual level, I don’t think there are substantial changes. The story may go like this: A user installs a new antivirus on their computer, and that product guides the user to approve full disk access. Or, a user installs Zoom and then has to click the Approve button to use the camera, microphone, or for screen sharing.
Yet, once we start trying to deploy this software to a number of devices, say in a corporate environment, the complexity starts increasing exponentially. If this business leverages an MDM to deploy their software, they will need to build a new PPPC payload to deploy to their devices that grants these permissions immediately, so users don’t have to do the manual work on clicking and approving. Alternatively, if a business does not use an MDM, then this is up to the user to do. Again, this is adding additional complexity to, what should be, the simple act of installing software.
Additionally, the introduction of a new security mechanism can in and of itself introduce new security concerns. macOS Security Researchers like Csaba Fitzl or Wojciech Reguła have garnered a number of CVEs in bypassing TCC protocols and mechanisms.
Conclusion
Apple's Transparency Consent and Control (TCC) database is a pivotal element in the company's commitment to user privacy, but as with any new feature, there are caveats. However, by providing users with transparent control over their data, TCC ensures that privacy remains a top priority in the Apple ecosystem.
As technology continues to advance, frameworks like TCC play a crucial role in maintaining the delicate balance between innovation and user protection.
















