







On September 7, Huntress was made aware of a new threat against Windows operating systems and Microsoft Office products. With the identifier CVE-2021-40444, the MSHTML engine is vulnerable to arbitrary code execution by a specially crafted Microsoft Office document or rich text format file.
All modern Windows operating systems are susceptible to this attack, with a severity score of 8.8. Currently, there is no patch available, but Microsoft is urging users to mitigate this with workarounds until a formal fix is released. Under scrutiny, it seems this workaround is not effective in all cases.
Huntress has begun validating the effectiveness of the CVE-2021-40444 patch, and during our first set of testing, we see the patch looks to be effective. In the RTF rendition of the CVE-2021-40444 exploit, the malicious CAB file that is used to prepare code execution is not downloaded, and exploitation fails. This also prevents the attack vector present in the Preview Mode of the Windows File Explorer.
In the DOCX rendition of the exploit, it seems the CAB file is downloaded, but the code does not execute, and the exploit still fails. We are still analyzing things further and will share updates as we find them.
We still strongly encourage organizations to apply this patch as quickly as they can.
After the weekend, Huntress has not seen any new information from Microsoft regarding CVE-2021-40444. Security researchers are still experimenting with the vulnerability to understand other potential threats, and a handful are recreating exploits to find other detection capabilities. Huntress has validated the DOCX rendition of the exploit seen in the wild with a local proof-of-concept.
We have seen Windows Defender now trigger and prevent execution, seemingly based off the ../ characters present. Please ensure your antivirus engines are up-to-date!
For a technical deep-dive on what we have learned about CVE-2021-40444, what we are seeing in the security community and what you can do for both prevention and detection techniques, join us for our monthly Tradecraft Tuesday episode on Tuesday, September 14 at 1pm ET. We'll talk about phishing as an attack vector—and CVE-2021-40444 will certainly be the focus of our conversation.
Here’s a recap of some of the developments that happened overnight:
Without a patch available, and without effective mitigation techniques, things certainly look grave. Please remain vigilant and do your best to avoid DOCX, RTF and PPTX files from unknown or untrusted locations. As we know, prevention efforts are not the end-all-be-all—the community is working hard to prepare detection techniques and methodologies to hunt for this threat.
We can hope that a patch might be created within a week, but truthfully, there is no telling when we might see something available. For now, we need to prepare ourselves by understanding this attack chain, monitoring for artifacts and incidents of compromise and keeping our ears to the ground for new information and threat intelligence.
We’ve created a post on Reddit to spread awareness, and folks from the MSP community are chiming in with their own intel/experiences with CVE-2021-40444. Feel free to tune in there for additional intel from the community.
The security industry has seen attacks in the wild targeting CVE-2021-40444. While this vulnerability is typically weaponized with Microsoft Office documents, this threat is especially prevalent in phishing attacks.
Inside of a Microsoft Office document, cybercriminals can craft a malicious ActiveX control that will execute arbitrary code from a specified remote location. Researcher Rich Warren has validated this attack triggered in Windows Explorer with “Preview Mode” enabled, even in just a rich-text format RTF file (not an Office file and without ActiveX). This indicates it can be exploited even without opening the file and this invalidates Microsoft’s workaround mitigation discussed below.
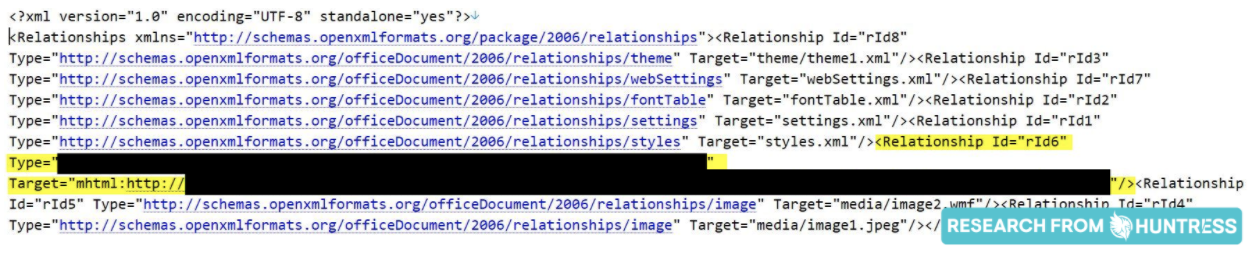
For Office files, no traditional VBA macros are needed for this attack. Any URL beginning with mshtml:http will download a file passed to the MSHTML parser engine, and potentially any way an Office document can call out to a URL can be used to exploit CVE-2021-40444.
Some samples that have been discovered in the wild have been staging Cobalt Strike, a threat emulation framework often abused by threat actors.
As of September 9, Huntress is not aware of any publicly available proof-of-concept exploits being used by adversaries. To better protect organizations while a patch has not been released, the community is not yet sharing samples of or artifacts from this threat.
We always recommend having a layered security approach to protect and defend your environments. Huntress monitors for persistent footholds, and this attack on its own does not yield any persistence mechanisms—but that’s why a layered approach is critical during these incidents and exploits. If the attackers use post-exploit activity like the Cobalt Strike stager, other command and control behavior and/or ransomware detonation, then Huntress will catch it and provide assisted remediation steps.
As always, Huntress will be monitoring the situation and keep this blog post as well as our social presence up-to-date with any future findings.
Ensure your antivirus engines are up to date as providers add detection and prevention capability as soon as they can.
While a patch is not yet released and the mitigating workarounds may not always be feasible, Microsoft suggests disabling the installation of all ActiveX controls in Internet Explorer. Recently, Joseph Roosen and Kevin Beaumont uncovered that this does not require ActiveX controls and the workaround below may be ineffective.
This requires modifying the Windows registry, and can be done by these commands from an Administrative command prompt:
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0" /v "1001" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0" /v "1004" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1" /v "1001" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1" /v "1004" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2" /v "1001" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2" /v "1004" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3" /v "1001" /t REG_DWORD /d 00000003 /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3" /v "1004" /t REG_DWORD /d 00000003 /f
These commands can be readily placed in a script to be pushed out to your RMM solution if so desired.
To undo this workaround, modify these same commands to use reg delete rather than reg add.
To scan a DOCX file you feel might have the CVE-2021-40444 exploit, researcher @decalage has shared a Python script to use oletools and look for an mshtml:http external reference abused in this attack. The Linux command-line utility oleobj will also display external references. While the mshtml:http syntax may not be the only form of weaponizing this attack, this method alone should not be relied on as the single source of truth.
SwiftOnSecurity has also showcased that there may be artifacts left in the HKEY_CURRENT_USER Registry hive and can be detected with Sysmon.
The security industry has released information for active threats they have uncovered, including the suspect filename, file hash, referenced domain and/or IP address.
3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf
938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52
8a31b04c1396c79efca3daa801310a16addf59d41834ea100fe9cededd3e3bad
2e328b32f8c7081fbe0aa8407b1b93d1120ac1c8a6aa930eeba1985c55a0daa0
4d5acce20cfa4ff5cf5003b03aa6081959db25e4eca795b2e5f4191c04c5be32
4477d161958522d5d0dd0cfc4e6d38b0459654184c4ee2b9bce78d2524d7bc9d
a5f55361eff96ff070818640d417d2c822f9ae1cdd7e8fa0db943f37f6494db9
049ed15ef970bd12ce662cffa59f7d0e0b360d47fac556ac3d36f2788a2bc5a4
d0e1f97dbe2d0af9342e64d460527b088d85f96d38b1d1d4aa610c0987dca745
5b85dbe49b8bc1e65e01414a0508329dc41dc13c92c08a4f14c71e3044b06185
199b9e9a7533431731fbb08ff19d437de1de6533f3ebbffc1e13eeffaa4fd455
d0fd7acc38b3105facd6995344242f28e45f5384c0fdf2ec93ea24bfbc1dc9e6
938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52
1d2094ce85d66878ee079185e2761beb
http[:]//pawevi[.]com
http[:]//hidusi[.]com
http[:]//dodefoh[.]com
http[:]//joxinu[.]com
45.147.229[.]242
104.194.10[.]21
To do your own digging, it is worthwhile to simply search “CVE-2021-40444” on Twitter or dive into these resources:
Get insider access to Huntress tradecraft, killer events, and the freshest blog updates.
