Choosing the right antivirus (AV) tool can be a real headache. With so many options available, how do you know which one is the right fit for you? You’ve seen the ads, you’ve heard the debates around which AV or EDR solution is the best, and now you’re probably wondering what's the best approach for your company's security.
We get it, and we’ve been right there with you. Our team has been through the same extensive search, spending countless hours exploring various security tools out in the market. But in our journey, one name has consistently stood out and impressed us: Microsoft Defender Antivirus. In this blog, we'll walk you through why Defender should be getting more attention from you and should be a top consideration.
Defender History
First, let’s take a brief look at the history of endpoint security in Windows and the journey to today's Defender product. Beginning with Windows XP, we saw Security Essentials show up as an option for removing malicious software and eventually became a full-blown anti-malware solution that provided real-time protection as well. The tool was… in its infancy and certainly lacked some of the robust features that other tools had at the time—but the world was a different place 20 years ago.
Following its introduction, the product changed names several times over the years from Security Essentials to Forefront Endpoint Protection (FEP) to System Center Endpoint Protection (SCEP) and then Defender with the Windows 8 OS. The Windows 8 version was the first fully functional Defender engine similar to what we have today. No longer did you need to download the tool separately, or add it as a Windows feature—it was just there, providing out-of-the-box protection for fresh installs of Windows.
Now with Windows 10 and Windows 11 (and the adjacent versions of Windows Server OS), we see a more robust detection engine with more capabilities along with the ability to pair with Microsoft Defender for Endpoint—Microsoft’s EDR product.
Note: Microsoft has also combined most, if not all, of their preventive tools under the Defender naming convention.
Challenges
One of the main challenges with deciding to switch to Defender is its reputation from the early days that it was ineffective and didn’t perform well. Those early days were full of learning opportunities, and Microsoft took that feedback and evolved. They took those early iterations of the product and continued building what has become a world-class security suite that includes endpoint, cloud and application security.
Another challenge is the management of Defender across a fleet of endpoints which is difficult at best. Many third-party AV tools offer a centralized dashboard for ease of management, tracking endpoint statuses and sending out policy updates. Defender simply doesn’t have a similar option out of the box.
An additional challenge is the investment of time required to implement an AV product. Implementing a security tool across hundreds or thousands of endpoints takes a significant amount of planning and effort, as it’s never quite as simple as “uninstall” and everything just works. And this is where Huntress comes in…
Huntress' Solution
If you’re familiar with Huntress, you likely already know that one of the components of our EDR offering is our Managed Microsoft Defender feature. We combine Defender's powerful platform with a team of analysts reviewing detections in real time. Our offering includes multi-tenancy and visibility into other third-party AV statuses for an endpoint in a single dashboard.
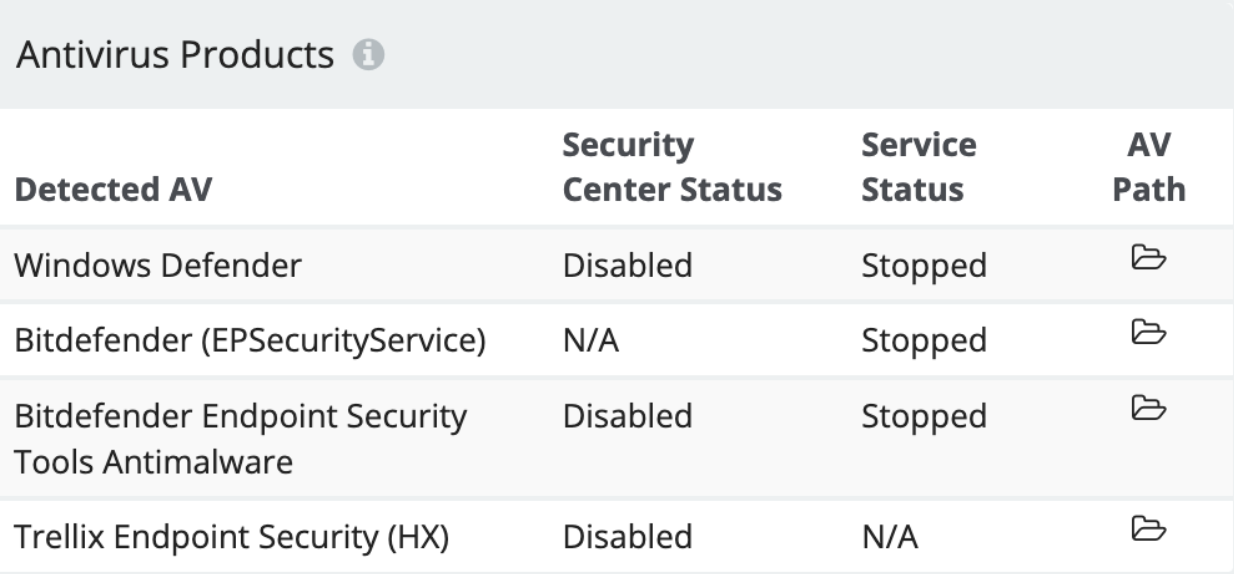
We often find leftover components of a third-party AV or machines that are running multiple AV products, and our portal displays these to help you focus on fixing troubled endpoints.

Using a new endpoint security product can be complex, so we work with teams during their transition to Huntress Managed Antivirus to make it as seamless as possible and provide documentation to help with the process as well.
But the transition to a new AV platform is just the beginning. Who in your organization is going to monitor and review the alerts? Do you have someone who can dedicate their time and skills to determine why winexecsvc.exe is being used and if it’s legitimate or not?
Often, AV alerts are unhelpful without broader context, and that’s where the Huntress SOC and our team of experts come in. Combining our EDR telemetry, AV detections, event logs and skilled analysis, we work to weed out false positives and only bring items to your attention that require direct action.
Ultimately, there are several ways we could have developed our Managed Antivirus solution, including building our own AV engine or potentially ingesting data from any number of third-party AV products. But when considering the challenges that SMBs face today, Defender checked all the right boxes. It is built into all modern Windows operating systems, it receives excellent scores in third-party testing and the breadth of Microsoft’s telemetry is unrivaled.
Notable Features
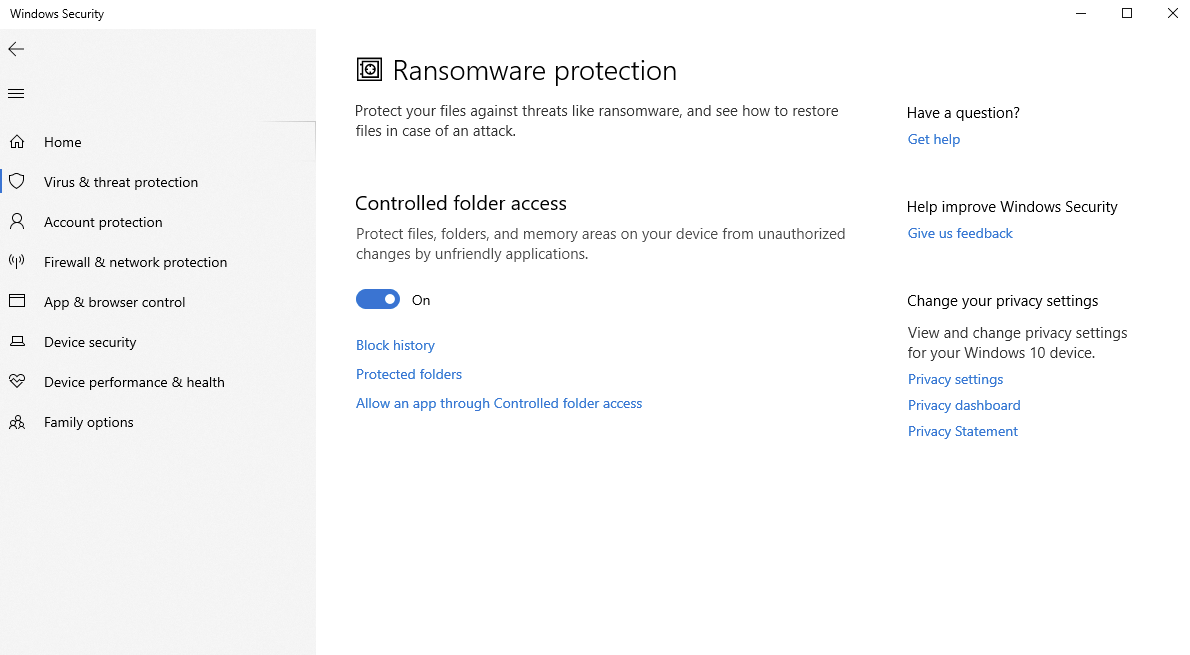
In addition to the expected feature set of a modern next-generation antivirus solution, Defender provides other features that help protect data and keep systems safe. Their ransomware protection (controlled folder access) allows control of what applications are permitted to write to certain folders, which is helpful in preventing ransomware from encrypting all of your documents.
Another feature called potentially unwanted application (PUA) blocking allows you to prevent apps from preying on unsuspecting users by presenting ads or even installing a malware backdoor. This one is particularly helpful as it allows an administrator to not only prevent PUAs from being installed via the browser, but also from installations via network share or a user's downloads folder.

Next, Defender has the cloud-delivered protection feature that contributes to Microsoft’s telemetry for better efficacy of AV signatures and EDR detectors. As most modern malware is polymorphic, cloud telemetry allows Microsoft to provide almost-instant determinations on new samples based on their behavior.
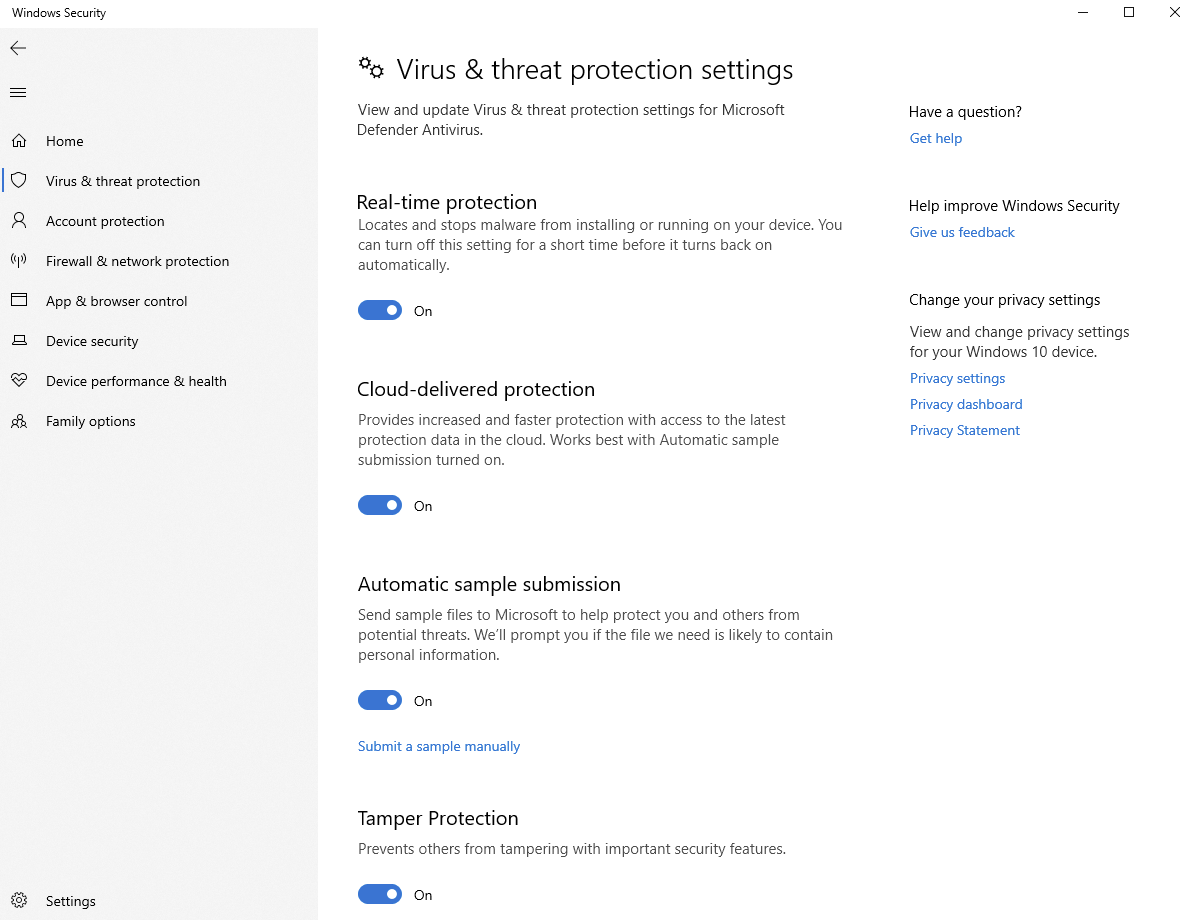
The last notable and seemingly-obvious valuable configuration feature is Tamper Protection. This particular feature has been improved over the last few years and is now enabled by default—preventing others from altering configured security settings like real-time protection, AV exclusions and cloud-delivered protection.
Resources
To wrap up here, I’d like to note that finding resources on Microsoft Defender is really tough. I've gathered a lot of resources while working with our team to provide support for some of Defender’s more advanced features.
So, instead of leaving you with a call-to-action of simply dumping your current AV and moving to Defender, I’ll put a list of resources that have been really helpful for us and hopefully will help you in your research or implementation of Defender. The links below are in addition to the resources I’ve linked throughout this post.
Resource
Notes
Microsoft Defender for Endpoint in Depth
Also available on Amazon, this book has been tremendously helpful to folks on our team and for this blog.
What is Microsoft 365 Defender?
Microsoft’s “overview” documentation page for all the M365-related Defender offerings.
Cloud-delivered protection in Defender Antivirus
Details on the cloud-delivered protection feature within Defender AV.
Cloud protection and sample submission
Details on the sample submission feature and how it functions (including information on PII).
Microsoft’s tool for managing Defender as an MSP.
Microsoft’s Tech Community announcement about the new endpoint security product for SMBs.
Group policies for managing Defender
This link is to a specific policy, but the entire section is for Microsoft Defender Antivirus and is helpful for understanding feature definitions and controlling settings for domain-joined PCs.
Defender AV compatibility with other security products
Even though some vendors suggest running both their solution and Defender, Microsoft clearly states they do not recommend it.
Microsoft documentation to understand how signature updates work and what’s happened in recent platform updates. This is a combination of a knowledge base article and release notes.
Ever wonder what to do with the names of threats as shown in Microsoft Defender AV? This is the article for you.
Because we all want to block these things.
Applies to the Defender for Endpoint and Defender for Business products, as well as Defender Antivirus.
Huntress Managed Microsoft Defender
All of Huntress’ Managed Microsoft Defender-related documentation.
Microsoft Defender Antivirus received the AV-Test Institute’s award for Best Advanced Protection.
2023 Real-World Protection Test (AV Comparatives)
Microsoft Defender’s real-world test by AV Comparatives.
















