Update 1/26/2020: MITRE assigned CVE-2020–7984 for this vulnerability.
Update 12:55pm 1/24/2020: SolarWinds has released two hotfixes for the vulnerabilities! You can find these fixes on their support website. According to the documentation these hotfixes disable N-central’s device auto-import feature temporarily. A future release will re-enable the feature.
• 12.1 SP1 HF5: https://community.solarwindsmsp.com/Support/Software-Downloads/MSP-N-Central/MSP-N-central-12-1-SP1-HF5
• 12.2 SP1 HF2: https://community.solarwindsmsp.com/Support/Software-Downloads/MSP-N-Central/MSP-N-central-12-2-SP1-HF2Update 10:58am 1/24/2020: SolarWinds has published some mitigation instructions to expunge the credentials from the N-central service. This should clear the passwords that attackers are able to extract using the Dumpster Diver vulnerability. As with most mitigations, this brings with it some impact to normal services (see the instructions for details). However, we believe that it’s absolutely worth performing these mitigations until a patch is released.
Update 1/24/2020: We’ve been in close contact with the SolarWinds N-central team and their executive leadership. They are taking this vulnerability very seriously and understand the impact exploitation will have on their customers. They are working around the clock to implement and test a patch and expect that patch will be available by the end of the day.
When the patch is completed they will be able to update their cloud customers immediately but any customers who use the on-premises version will need to apply the patch, so keep checking back for updates and have your teams prepared to update your systems when the patch becomes available.
Original Post
Thanks to the effort of multiple MSP partners, our team was notified about a zero-day vulnerability posted to Packet Storm for SolarWinds N-central. In this post, engineer Justin Oberdorf suggested the fully patched product would allow an unauthenticated user to perform several alarming actions. These included registering agents and dumping the customer configurations which can contain cleartext active directory credentials.
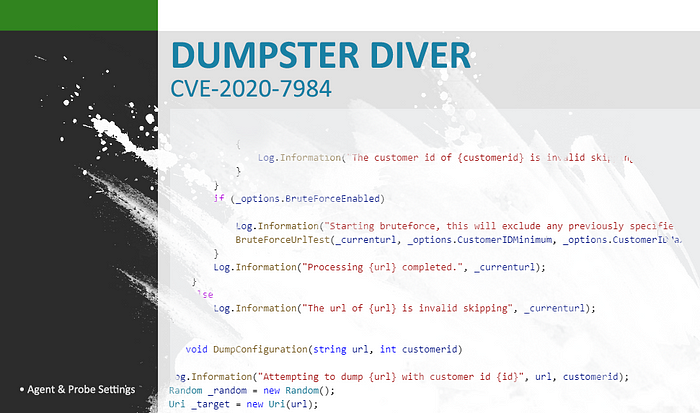
With the help of the Huntress community, we’ve now validated that this exploit works as described and were able to retrieve the domain admin password our partner stored within the product’s Agent & Probe settings. We are not aware of a patch for this issue yet, but will update this as soon as we learn otherwise.
Please don’t hesitate to post your questions to r/MSP.
How Things Unfolded
On January 21st, 2019 the previously referenced Packet Storm article was published. According to the article, this was after a 90 day responsible disclosure period had lapsed.
This was reported to SolarWinds PSIRT(psirt@solarwinds.com) on 10/10/2019.
Almost immediately after, the news was reposted across social media by automated services like the one below:
Within the article was a link to a Proof of Concept (PoC) that gives novice IT staff (and novice hackers) the ability to easily exploit this vulnerability. The same code was also published to Justin’s GitHub repository:
Sometime shortly after, the Packet Storm article and the GitHub repo were both taken offline. We don’t have any context regarding why this happened.

Despite these resources being taken offline, we discovered at least a half dozen individuals had access to the original files. It was also a bit of a humbling reminder that the internet doesn’t easily forget things.
Proof of Concept Contents
Inside the PoC archive were two redacted screenshots demonstrating the Customer ID bruteforcing capability and the dumped configurations.
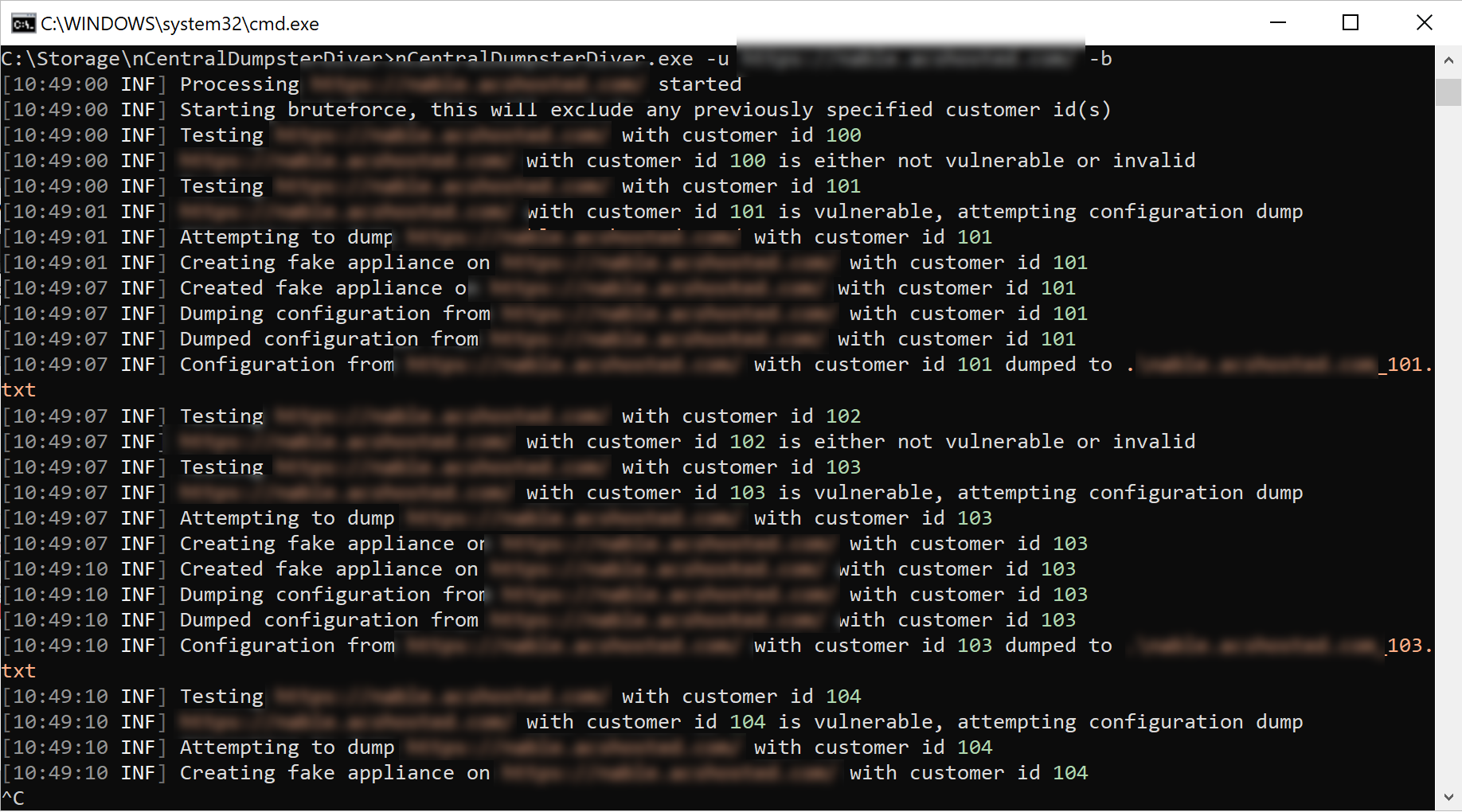
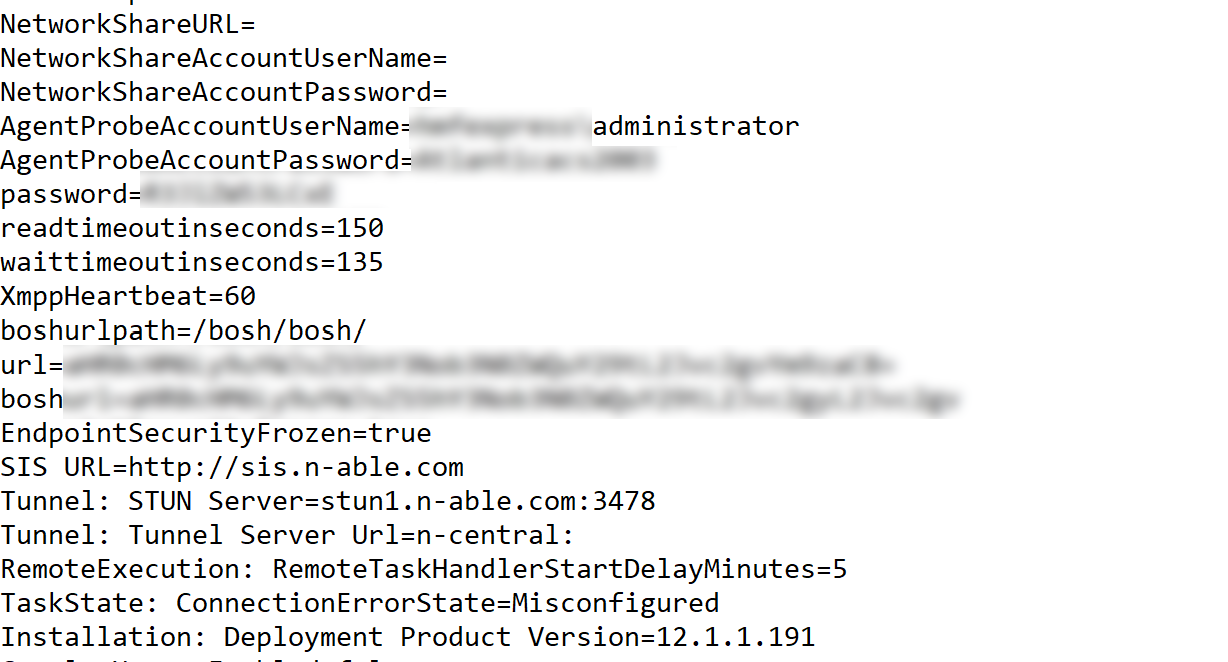
Additionally, there was a screenshot highlighting how a hacker might find these vulnerable servers online using Shodan. For those not familiar with the Shodan service, check out this awesome Tradecraft Tuesday episode featuring YouTube superhero Tom Lawrence. Needless to say, 4,000+ results is a bit nerve-racking.

Validating the Vulnerability
Within a few hours after receiving the PoC source code from two MSP partners, the Huntress ThreatOps team completed their review and understood how to trigger the vulnerability.
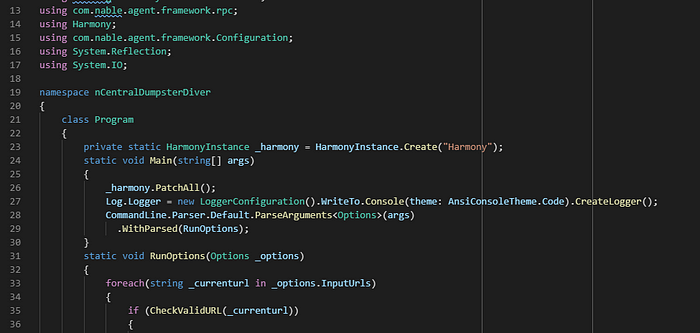
With a compiled PoC, we worked closely with one of our partners to determine if the vulnerability truly existed and what risks the MSP community would face if this was true.
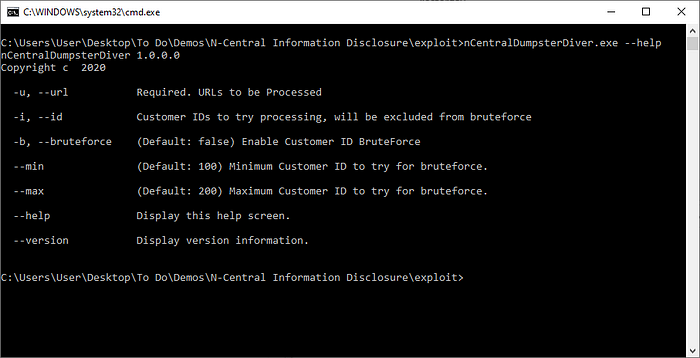
Rather than use the bruteforcing capability, we decided to more surgically target a single Customer ID.
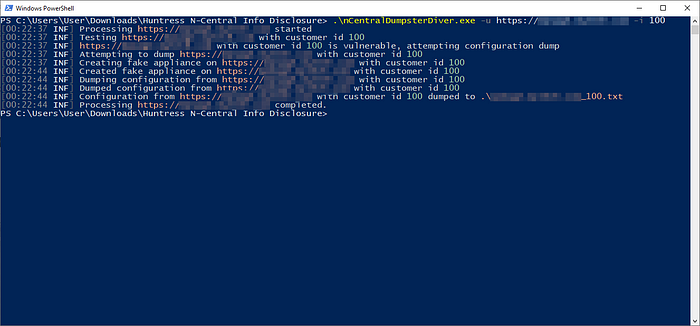
In less than 30 seconds later, our fake Windows agent registered in their dashboard and we discovered the domain admin credentials we saved within this customer’s Agent & Probe settings. The whole effort took ~3hrs which was half the time it took to publish this advisory. Needless to say, this situation is pretty critical.
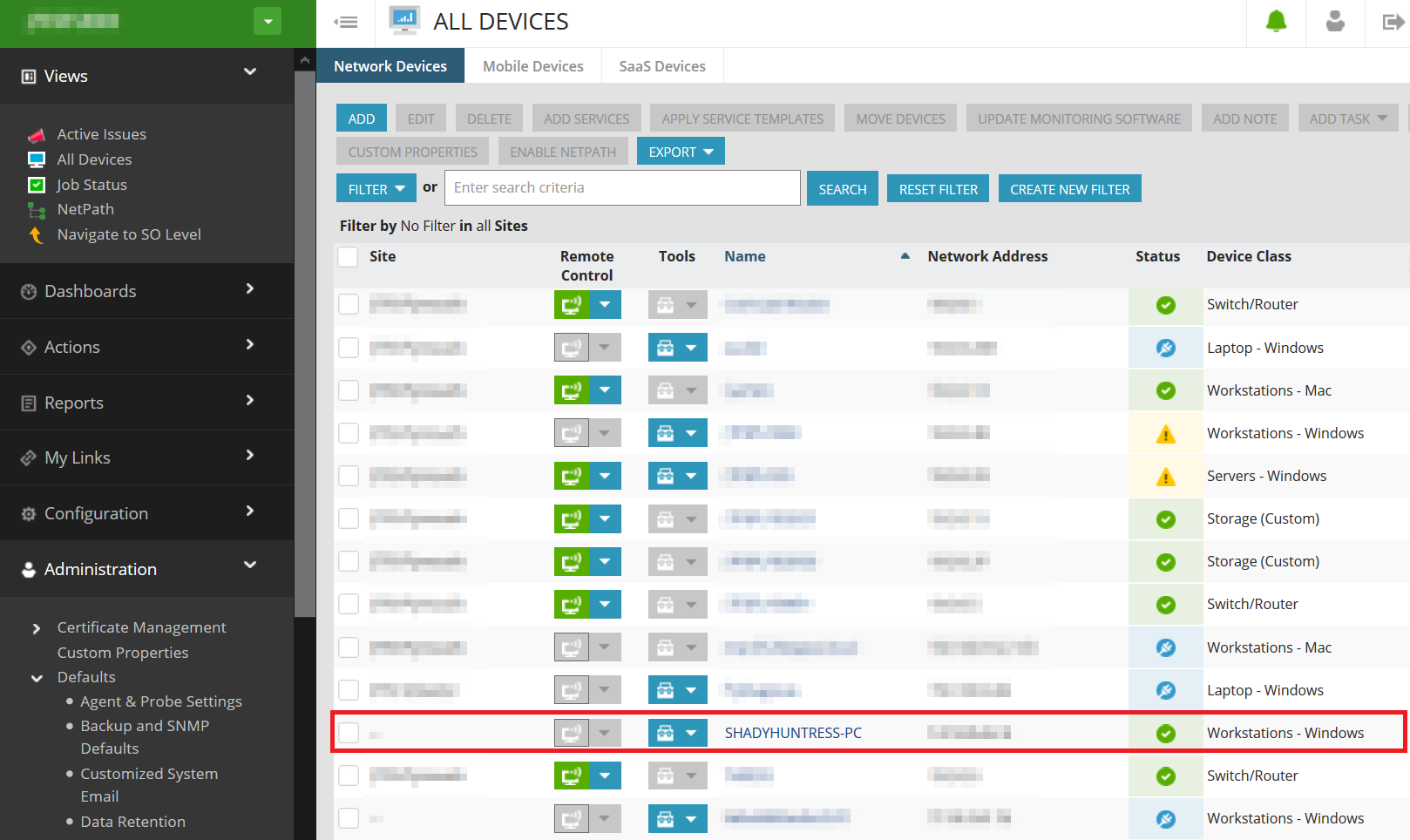
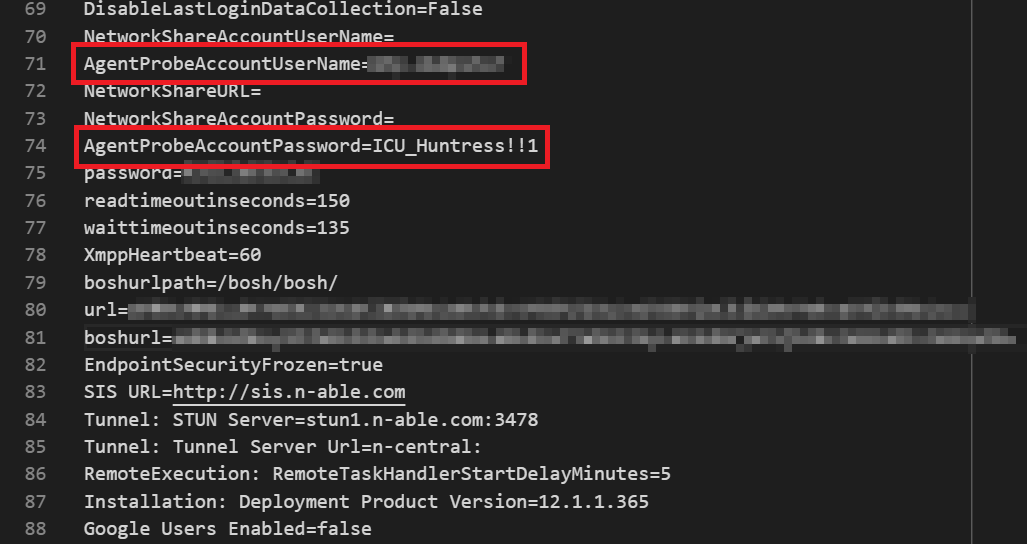
Mitigating Actions
Our partner was concerned hackers (or other MSPs) might have already dumped their user names and passwords so they decided to disable all of the N-central stored accounts out of an abundance of caution. They also changed each customer to a new set of credentials not linked to a domain account as a temporary stop-gap measure until the vulnerability gets patched.
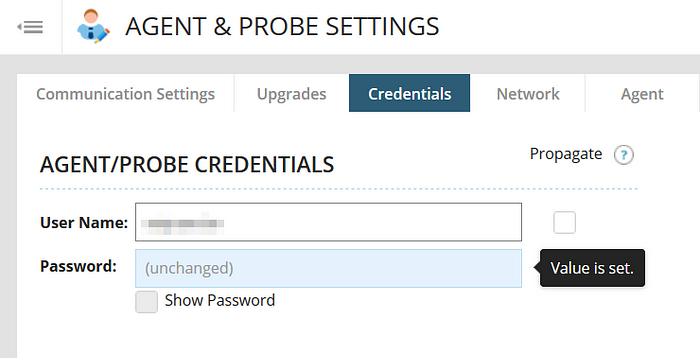
You could also consider blocking internet access to the RMM but this will likely significantly hinder productivity. With that said, we’ve requested more formal guidance from the SolarWinds team and will share it as soon as we learn something.
Our Conclusion
The MSP community has been on fire lately and we still haven’t finished the Bishop Fox conclusion. Give us a hot minute to catch up 😉














