Bringing cybersecurity education to the masses is a passion of ours here at Huntress—so much so that we hosted our third hack_it training event just last week! This two-day training was packed with interactive and audience-driven sessions, tours of the dark web and a few demos dabbling in macro-enabled malware. Hundreds of hack_it community members joined us virtually to sharpen their skills, share their security knowledge and sip on some beverages 🥃(especially during the shady after-hours session).
Weren't able to catch the live event? We got you covered. You can watch all of our sessions on-demand here, or keep scrolling for a recap.
Playing A Cybercrime Game of Clue
We went choose-your-own-adventure style for our first session. Modeled after the popular game of Clue, we were presented with a cybercrime—so we worked our way through different rooms (each corresponding to a different MITRE ATT&CK tactic) to analyze our attacker’s tradecraft and track down who hacked us.
In our hypothetical scenario, we observed malicious behavior originating from a network that we manage. The details were vague at best, and management has tasked our team to figure out what happened. We had one hour to determine:
- What type of threat actor hacked us?
- What did they target?
- Were they successful?
As we put on our detective hats and walked through each room, we picked up clues along the way to try and piece together how a threat actor compromised our network. Turns out, this was a more difficult task than we expected (between the two times we played this game, we had a 50% success rate). The jury’s still out on if that was due to the audience picking up on the wrong clues or if it was some trickery from our gamemasters Kyle Hanslovan and Lisa Mitchell. 😈
Lessons Learned:
- In cybersecurity, every move counts. This is true from both the attacker’s and defender’s perspectives.
- Vigilance is key when determining who is attacking you and how.
- Tabletop exercises are a cost-effective way to test your team’s preparedness for investigating or responding to cyberattacks.
Dark Web Dumpster Diving
In this fireside chat, Dave Kleinatland was joined by Chris Loehr and Felicia King to explore the messaging and services from different ransomware gangs and discuss what we could learn from the dark web.
But before we kicked things off, we asked the 400+ members in our audience how familiar they are with the dark web and how often they visit. Here’s where the responses netted out:
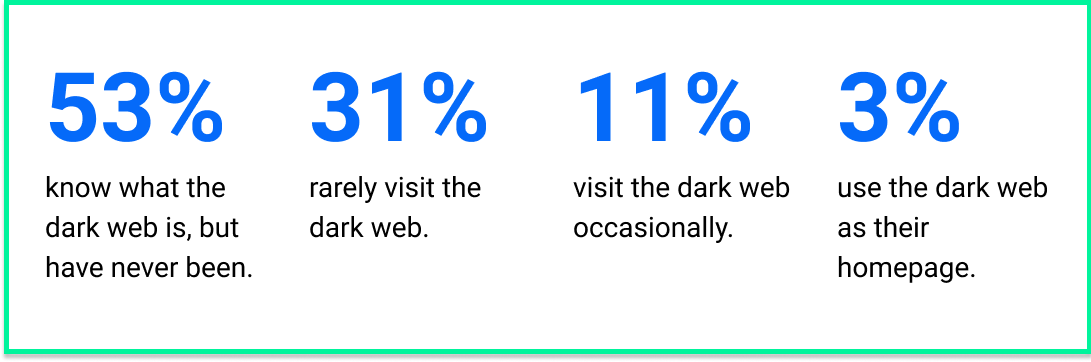
With the majority of our attendees familiar with the dark web, Dave, Felicia and Chris started their session by demystifying the dark web and explored how hackers use it as their playground to sell their services and earn a living. Not only did we get a glimpse of the shady marketplaces where a variety of cybercrime services are for sale and what types of data are most in-demand, we were also left with some solid insights from our three panelists.
Lessons Learned:
- Data leaks are one of the most popular commodities on the dark web.
- Many small and mid-sized businesses still have the old “my data isn’t worth stealing” mindset—but on the dark web, data is like currency. Even if clients don’t feel that their data is important to hackers, you can rebuttal that mindset by asking if their time is important. Most people will realize that they simply can’t afford to take time away from their business or from their life to deal with a security incident.
Phishing for Malware in Macros
With today’s level of cybersecurity awareness, most users know to hover over links within emails or look for the ‘https’ in the browser to avoid falling victim to phishing. But in our last hack_it session, John Hammond and Jason Slagle showed us that hackers have many more tricks up their sleeves. 👀
In this more technical session, John and Jason illuminated how bad actors bait businesses with macro-enabled office documents—and they even showcased how to set up your own internal phishing campaign.
Lessons Learned:
- Phishing is a tried-and-true attack tactic because it still works. Hackers continue to exploit the human element and people continue to fall for their tricks. In fact, we learned that 36% of security breaches in 2021 involved phishing, which is up 11% from last year (according to Verizon’s 2021 Data Breach Investigations Report).
- Despite knowing the scams and noticing the red flags, we’re seeing a trend of more targeted and methodical phishing campaigns. And this might leave many defenders feeling like they’re playing a game of whack-a-mole and reacting to the new tricks and tactics that attackers are using.
- The most successful phishing campaigns do three things: they set the stage with a pretense, strike fear with a threat and demand action through urgency.
















