What are the basics of threat hunting and malware analysis? Our experts sought to answer this burning question in a recent episode of Tradecraft Tuesday, featuring Huntress' Lead Threat Hunter Anthony Smith and Senior Security Researcher David Carter.
Both threat hunting and malware analysis work hand-in-hand to provide a better understanding of an environment's risk level, places to explore when searching a system, and where a hidden threat may be lurking. Let’s dive into each.
The Basics of Threat Hunting
Threat hunting is a critical function for proactive security that combines multiple data inputs to form a hypothesis for discovering unknown threats and security gaps in your environment. Data inputs can be any combination of external or internal threat intelligence, security tool alerts, or logs from numerous sources. Input information helps to determine what type of hunt you should conduct:
- Intelligence-driven - Using intelligence from various sources
- Data-driven - Using internal data sources on lower-priority alerts
- Knowledge-driven - Using aggregated data on adversary tactics, techniques, and procedures (TTPs)
- Hybrid - Using a combination of the three above to narrow the scope of the hunt

A threat hunt can be either structured or unstructured. The difference between these two hunts is that structured threat hunting is hypothesis-driven with strong research to back it. On the other hand, unstructured threat hunting is more data-driven and opportunistic, usually spurred on by a hunch.
The most efficient and recommended hunting approach is structured. In the structured threat hunting process, time is spent to form a well-scoped hypothesis that will result in the most useful hunts and investigations. The unstructured approach tends to lead to an inefficient hunt that could waste countless hours pursuing partially formed ideas while chasing preliminary hypotheses.
Why Should You Threat Hunt?
The importance of threat hunting boils down to one simple fact: Detectors can only find known threats. Typically, detectors are created after a new threat is discovered in an environment or from information publicly shared. But, threat hunting lives in the space between the unknown threats and detectors. It answers questions like:
- What are common TTPs of well-known threat actors?
- What drives hackers? Money, data extortion, or general chaos?
- What might a threat actor do next?
These evaluations help fill security gaps that were otherwise not thought of or not prioritized. The overall goal is to be able to assess what (if any) threats were missed by current security measures.
Tactical Malware Analysis Defined
What is malware? The simplest definition is a program, process, or service doing something it's not supposed to do. There are immeasurable variations of malware, some that are super stealthy, and others that are more obvious if you look for certain behaviors.
Tactical malware analysis involves analyzing a system to discover malware and adversary activity using built-in system tools and capabilities.
The below list doesn't cover every TTP malware may use, but it’s the starting point for a search. If you see something that is doing at least two of these three things, you should consider it odd behavior and a big RED flag:
- The process takes up a large amount of your system resources
- The process sends and receives network communications, but normally should not
- The process performs behaviors that help it hide in your system
Tools for Tactical Malware Analysis
Disclaimer: Do not perform any of these actions during an active incident as you could accidentally compromise forensic data. Volatile artifacts are temporary digital traces residing in a system's volatile memory (RAM), offering crucial insights into its operational state during a compromise. However, interacting with malware during triage can significantly impact these artifacts. Engaging with malware can modify running processes and network connections, potentially distorting the accuracy of investigative findings. Inadequate preservation before system restarts or shutdowns can result in the loss of volatile data, eliminating vital evidence needed for analysis. Mishandling malware during triage might unintentionally trigger further malicious actions, complicating the understanding of the initial attack. Triage activities have the potential to introduce new traces into volatile memory, confounding efforts to distinguish between original and post-triage states. Given these risks, it's essential to conduct a comprehensive forensic investigation before any form of triage to ensure the accurate preservation and interpretation of volatile artifacts.
Learning what to look for and determining unusual behavior takes repetition, a keen eye, and an appropriate toolset. Thankfully, Microsoft has several native tools to help you get a proper lay of the land.
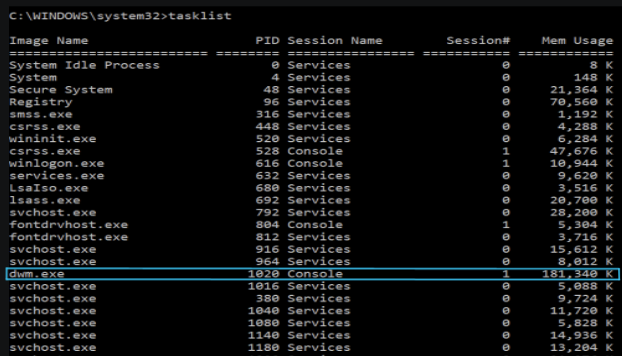
A good place to start is with the process list using the tasklist command line tool. Looking at a process list may seem a bit daunting at first, but after you learn what should be there, it makes it a lot easier to see something that shouldn't. Often, malware will try to masquerade as a regular process by switching up the order of letters or using the same name but in a different folder location. This is also a good place to see if a process is using an unusually high amount of memory.
Now that you've checked out the process list (keep that info handy), you want to bring up network connections using the netstat command line tool and the -anob options. This will show you all connections, associated IP addresses, and the process ID (PID)/executable making the connection or opening the listening port. Start by looking for processes that should never make network connections or ports that seem very obviously bad (think 1337). When you find one, note the PID and go back to your process list to see where the file is located.
After you've looked at the process list, you've looked at network connections, but where does the malware actually live? Unless the malware is running in memory only, its original executable and the mechanism that kicks it off hides somewhere on the system.
Finding persistence is arguably the most difficult step in tactical malware analysis, but there are some common places to always check: Services, Scheduled Tasks, and the Registry. While Services and Scheduled Tasks can be easily viewed via command line tools, it may be easiest to check all three possible persistence locations in the Registry using the Registry Editor application. The keys to search for are:
- "HKLM\SYSTEM\CurrentControlSet\Services"
- "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache”
- "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
- "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce"
There are many, many more registry keys that you could check, but this is a good starting place. You want to look for the possible malware names that you found while searching the process list and network connections. If you find them, you may have found the persistence!
Warning: Everything in Windows lives in the Registry, use caution when interacting with it and do not modify anything unless you know what you are doing!
It’s worth noting that until you spend hours and hours learning about the Windows system, you will go down many rabbit holes looking at things that are actually normal. This is okay and also a good way to educate yourself. Also, this blog gives a very high-level overview of threat hunting and tactical malware analysis and is not at all comprehensive. These are two subjects that take years to master, and even then you will find you have more to learn.
If you’re curious about learning more or starting your journey, check out these resources below.
Resources
- Process List (tasklist): https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/tasklist
- Network Connections (netstat): https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/netstat
- Services (sc query): https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/sc-query
- Scheduled tasks (schtasks): https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/schtasks
- Registry (Registry Editor): https://support.microsoft.com/en-us/windows/how-to-open-registry-editor-in-windows-10-deab38e6-91d6-e0aa-4b7c-8878d9e07b11
Special thanks to David Carter, Anthony Smith, Kaleigh Slayton, and Joe Slowik for their contributions to this write-up.
Want a more in-depth discussion of the basics of threat hunting and tactical malware analysis? Watch our Tradecraft Tuesday episode on-demand here.
If you’re not already registered, register for the series today!
















