From CryptoLocker to Locky to Sodinokibi to Maze, ransomware has been a staple in the hacker-verse for a long time. For defenders, the solution to ransomware usually consists of robust incident response and containment, followed by a sturdy backup and recovery plan.
But how do you know when to activate this plan? And what happens when attackers find new approaches?
What Do Ransomware Canaries Do?
Ransomware Canaries are a mechanism to deliver faster detection of a ransomware incident.
Imagine if you woke up at 7am on Monday morning to a flurry of phone calls from your customer about a ransomware incident. You have your incident response playbook in hand and your backup methods ready to go, but executing all the moving pieces still takes time — draining away productive hours at the start of the work week.
What if you had been alerted to the incident on Friday night when it started encrypting? You would have an extra 60 hours to contain, respond, and remediate. Detecting ransomware early accelerates recovery time and shows your clients you’re already on top of the response plan.
What is a Ransomware Canary?
A ransomware canary is nothing more than a file that sits quietly on an endpoint and is monitored for changes. If the file is encrypted due to a ransomware outbreak, this signifies a change to the file and triggers an alert so that investigation and response can begin.
The idea comes from the age old “canary in the coal mine” where miners would bring actual canaries into the mines as early warning signs of carbon monoxide fumes.

How Does It Work?
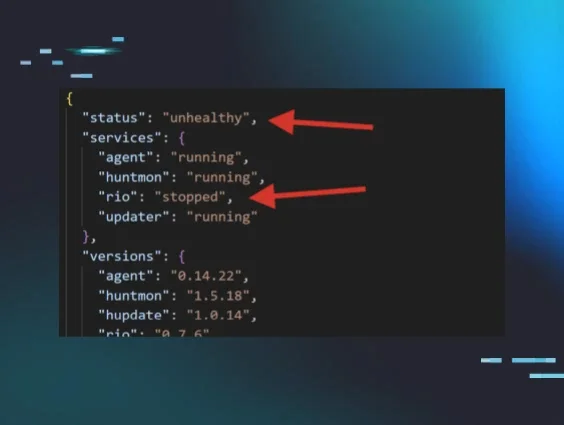
The Huntress agent will simply push out unique canary files onto the endpoint. When changes to the ransomware canary files are detected, it sets off an alert to our ThreatOps team to kickstart an investigation.
By marrying this early detection mechanism with ThreatOps automation and intelligence, we are able to alert quickly and weed out potential false positives (changes to these files may not always relate to encryption by ransomware). If a ThreatOps investigation concludes that ransomware is indeed the cause, a critical incident ticket is sent identifying which endpoints are impacted.
Aren’t My Backups Enough? Why Do I Need This?
Backups are a critical component to any recovery plan, but it helps to know when to actually activate the recovery. At the same time, threats evolve; the ransomware of yesterday is not the ransomware of today. With backup plans essentially voiding their ability to make money, we’re now seeing how bad actors not only hold data for ransom, but also exfiltrate copies in order to extort their victims — threatening to unleash sensitive documents to the dark web when payment is not made.
At Huntress, we look at how things have been done before and how it can be done better. One of the interesting aspects to Huntress’ approach is the implementation of unique canary files. Each canary contains an embedded QR code unique to the user profile; that way if data is released onto the dark web that includes the ransomware canary file, we can trace back to the source of the exfiltrated data.

Why Detect and Not Prevent?
Right now, Ransomware Canaries specifically look at tackling the detection of ransomware and enabling faster response. With a “crawl, walk, run” approach, Ransomware Canaries establish a threat research foundation to identify new holes that need to be addressed to improve prevention. We know that perfect prevention does not exist — the “cat and mouse” game between attackers and defenders is and always will be ongoing. Even though Ransomware Canaries do not directly offer prevention, it offers intelligence to inform actionable steps towards better prevention.
Why This Approach to Ransomware?
When we take a step back and oversimplify how security tools work, they usually require two things: A) the right visibility to monitor for bad behavior and B) the training to recognize when it’s looking at something bad.
Think about it this way: If the threat is happening behind you, you can’t see it to respond. If the threat is happening right in front of you but you don’t recognize it’s bad, then simply seeing it does no good. Each layer in the security stack is merely a different view of the IT environment with a different set of training. This is why ‘stacking’ multiple tools together has been one of the fundamental principles in cybersecurity.
Let’s relate this to ransomware. There are many tools that can potentially detect ransomware but may have a very narrow view. For example, a tool may only be monitoring files or file behavior. So if the ransomware is “fileless” or uses some other mechanism not monitored by the endpoint security stack, then it can’t see it to respond. Even with persistence, there are instances where ransomware simply does not establish a foothold.
There are many solutions commonly stacked together to address prevention — from DNS filtering to endpoint file monitoring — but not as many that focus on detection and response. We’ve chosen to start out with detection and believe this will give us the research and ammunition to help guide new prevention solutions.
What’s Next?

There is a lot you can do with early detection. Early detection can potentially be combined with a response mechanism such as kickstarting backup recovery. And as ransomware continues to change, the beauty of the Huntress Security Platform is that it allows us to pivot right alongside these hackers — meeting and beating them wherever they go.
For more techie stuff, check out our support articles here: