Recently, I represented Huntress at mWISE (Mandiant’s Worldwide Information Security Exchange) in Washington, DC. Over the three days (September 18 to September 20), there were over 90+ speakers and 80+ talks on exploits, security operations, threat intelligence, and cloud security. Among them, I gave a tech talk on the Security Operations track entitled Pairing SOCs with Automation: You Won’t be Replaced by a Robot Yet. The nature of this talk was on open-source technologies and Slack-related capabilities that security teams can leverage to immediately add value to their security operations center (SOC).
You can watch the recording of my talk on YouTube, or read on for a quick overview and key highlights.
Why Automate?
SOC analysts spend a large portion of their days on triage and case analysis. While the foundations for a SOC may lie in playbooks and hands-on investigation, it is essential to identify quick, simple, and effective solutions for making analysts’ lives easier. Automation is the key to not only optimizing workflows and tools used on a daily basis, but also easily saving time and resources. For example, a tool where an analyst can query a host or IP to get various forms of data enrichment for a compromised machine, instead of manually checking across disparate data sources.
Foundations for SOC Automation
To enable automation in your SOC, there are a few preliminary steps required to ensure a strong foundation for developing automations. This goes back to the cyclical nature of the NIST Cybersecurity Framework v2.0: Identify, Protect, Detect, Respond, Recover [and repeat]. The NIST Cybersecurity Framework is a continuous model that businesses can follow for cybersecurity best practices.
Recommended Reading: Breaking Down the NIST Cybersecurity Framework
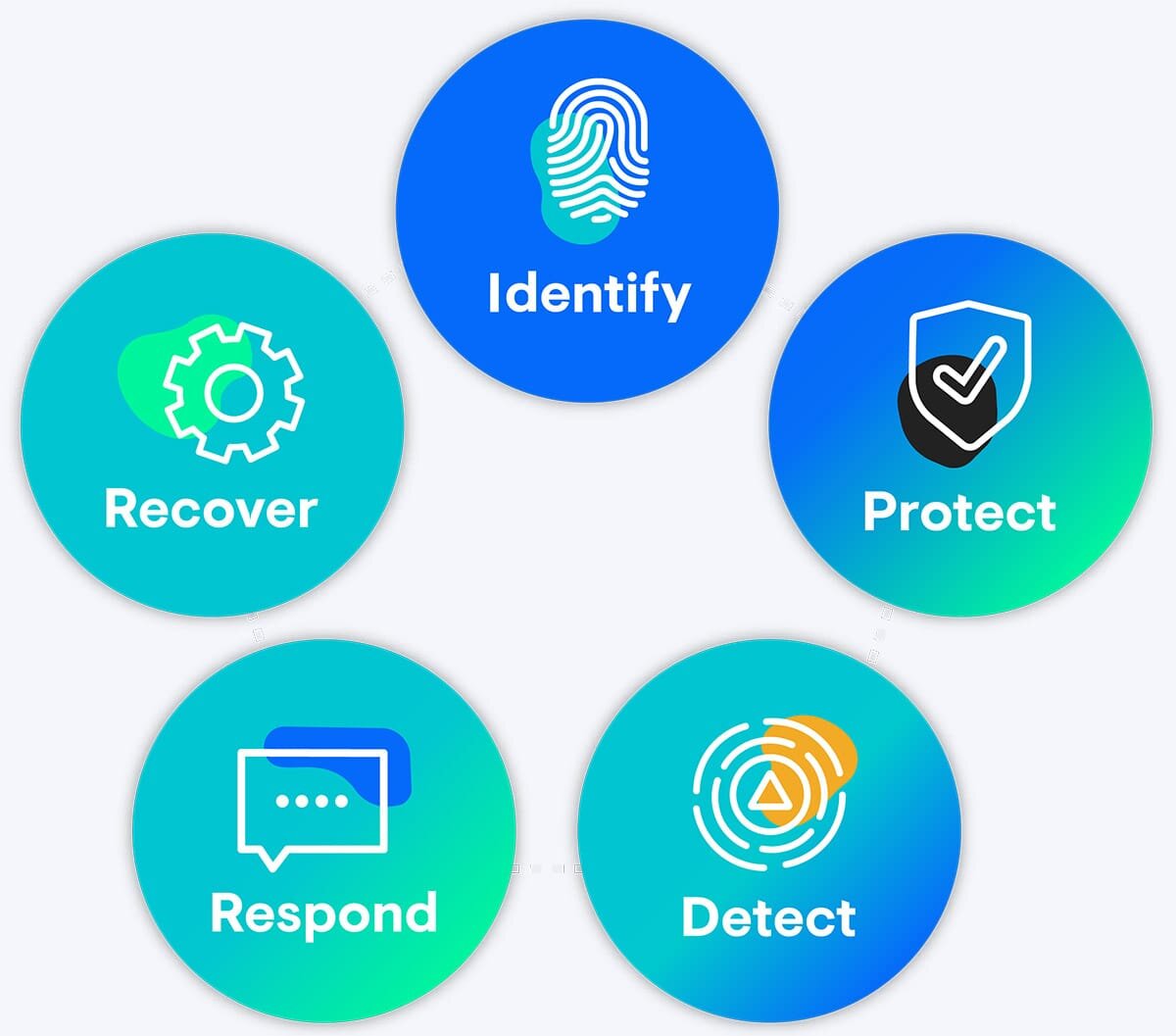
Before we focus on the Detect and Respond components, let alone automating those steps, we need to understand why we care about Identify and Protect.
- Identify your critical infrastructure, systems, and data.
- Protect and secure your data (on-prem vs. cloud, encrypted at rest vs. in transit, centralized vs. disparate data stores, data retention) while ensuring identity, access, and secret management.
3 Types of SOC Automation
When aligning with the NIST framework, SOC automation mainly falls into the Identify, Detect, and Respond phases. Furthermore, you can take steps to build automated capabilities in the following three areas:
- Identify your event enrichment; this involves pivoting from IOCs (indicators of compromise) from threat intelligence and disparate data sources to contextualized events, which we can build meaningful detections and alerts from.
- Detect events of interest and streamline day-to-day operations through workflow automation. Slack and other communication platforms can automate otherwise manual workflows in the form of ChatOps.
- [Analysts] Respond to incidents by leveraging in-house, open-source tools and services.
Let's break down each of these.
Event Enrichment
Event enrichment allows a SOC to programmatically identify interesting events and anomalies, which can be used to develop detections, alerts, and automated capabilities. Setting up event enrichment and a data orchestration layer is critical to identifying events of interest, which can be leveraged for building meaningful automation.
The keys to enabling event/log source and data orchestration are:
- Identify and track threat intel feeds for IOCs as well as event/log sources of interest for detection engineering.
- Contextualize events of interest from IOCs and log sources.
- Develop and fine-tune detections.
- Implement data orchestration layer for automated event/data processing.
Workflow Automation
Workflow automation removes the need for routine, day-to-day tasks and replaces them with abstracted workflows to share information, garner feedback, free up time, and be more productive. Universal chat platforms, including Slack (via Workflow Builder) and Microsoft Teams (via Workflows App), have streamlined, easy-to-use, no-code workflows that can be applied to a SOC.
To enable workflow automation:
- Identify day-to-day manual tasks done by your SOC.
- Evaluate existing processes and brainstorm how they can be automated.
- Develop the automation.
- Demo and share documentation.
- Maintain and finetune as needed.
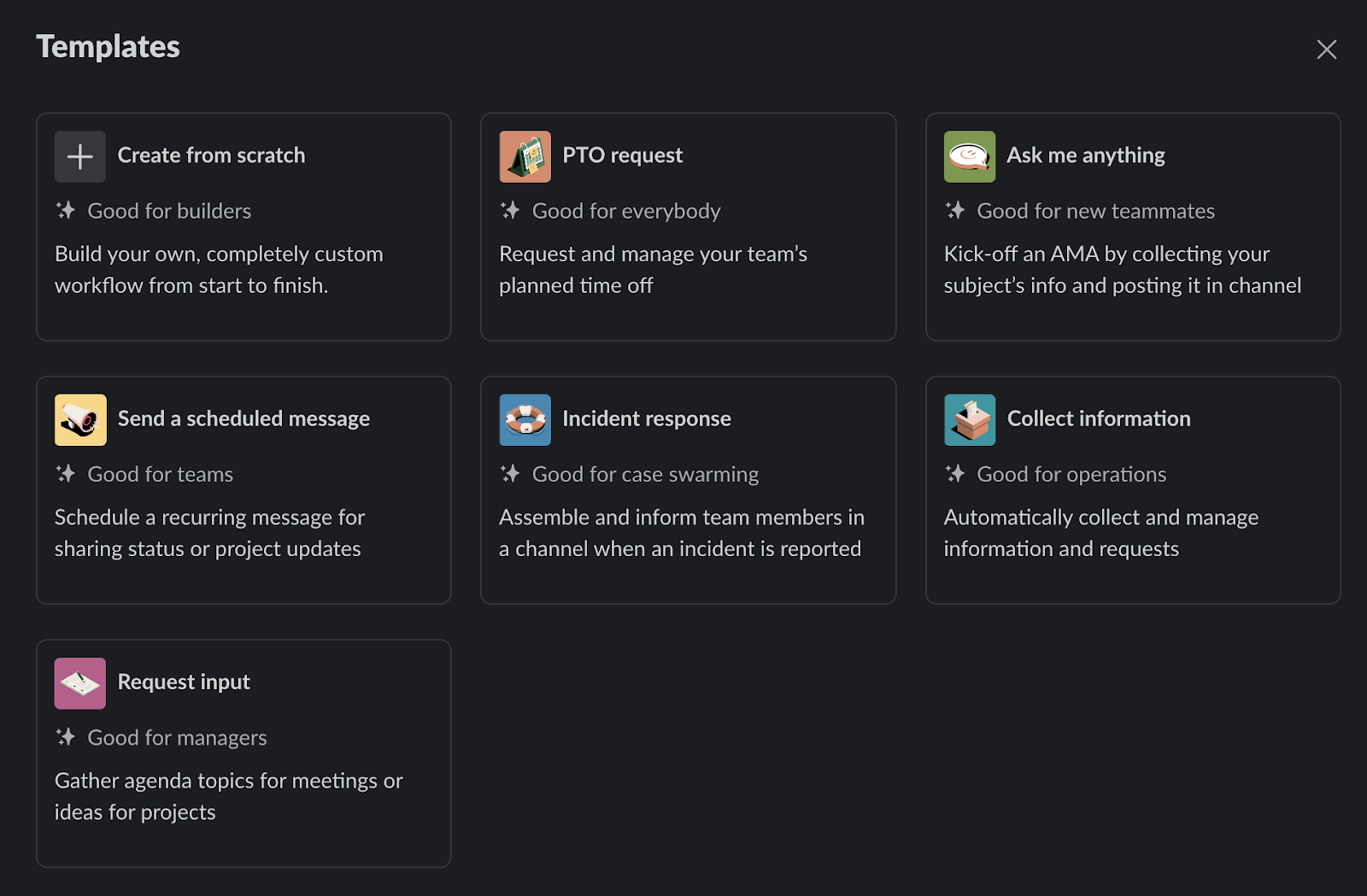
These templates are some of the no-code, out-of-the-box workflows available in Slack’s Workflow Builder.
Analyst Tools & Services
Analyst tools and services, in the form of Slack apps or web apps, can greatly reduce investigation time and improve the operational efficiency of a SOC. The capabilities that can be built out, such as static analysis tools, alert monitoring, and summary reporting, are a few ways we can accomplish this.
To enable analyst tools and services:
- Understand SOC workflows and processes (why and how things work the way they do).
- Identify gaps in existing processes.
- Brainstorm and create a development plan.
- Develop the tool or service based on this plan.
- Demo and share documentation.
- Monitor usage, collect feedback, and finetune as needed.
At the end of the day, we can’t fully automate away our jobs (nor should we, because human expertise is essential in cybersecurity). However, we can use automation to our advantage—to increase efficiency and productivity and to better enable SOC analysts and teams.
Check out my full mWISE presentation for some examples of how we achieve these types of automations at Huntress!
















