You’ve probably seen it by now, but there was a major ConnectWise ScreenConnect vulnerability (CVE-2024-1708 and CVE-2024-1709) – which we’re calling “SlashAndGrab” – that’s been shared across the cybersecurity community. Here’s what you need to know to keep yourself patched up.
The <a href="https://screenconnect.connectwise.com/download" target="_blank" rel="nofollow">patched versions</a> (23.9.8 or newer) are available from ConnectWise. Anything older should be patched immediately as it is considered vulnerable. Do NOT wait to deploy this update. ConnectWise has removed license restrictions, allowing partners no longer under maintenance to upgrade to the latest version.
What Should You Watch Out For?
Work under the assumption that you’ve already been compromised. Even if you have already patched or you run other security solutions, no matter what version of ScreenConnect you are running (cloud-hosted, workstation, server), never assume you are 100% safe.
Keep an eye out for these potential Indicators of Compromise (IOCs):
- Admins or Users are unable to login to your ScreenConnect Server.
- This may indicate that the user.xml file has been wiped or modified.
- Check your ScreenConnect Audit Log for any suspicious or unexpected activity.
- In C:\Program Files (x86)\ScreenConnect\App_Data\ (or your install location, if different) check for zeroed-out timestamps (0001-01-01T00:00:00) as they may indicate that a new user was just created. See the following examples:
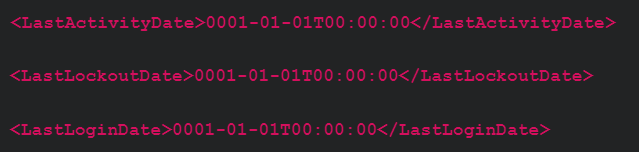
- In C:\Program Files (x86)\ScreenConnect\App_Extensions\ (or your install location, if different) you can look for “evil extensions” where threat actors stage a .ashx file that might allow for remote code execution.
- Each extension, legitimate or not, will be in a subdirectory that matches the format for a GUID.
- You can review the contents of the .ashx files inside the GUID subdirectories to look for rogue or malicious functionality.
- Note: the presence of subdirectories does not alone indicate that you have been compromised.
- Look for SetupWizard.aspx/ with Windows Event ID 4663 in Windows Event Viewer
- The key is the forward slash. Watch for any activity around this aspx file.
What Hosts are Impacted?
This vulnerability is focused around servers running the ScreenConnect Server instances on-premises. But…
- ScreenConnect server instances can run on a workstation, so some non-servers are also impacted. This also extends to instances where a server was compromised, thus exposing the workstations to the compromise as well.
- Single devices can also run multiple versions of ScreenConnect, so do not assume a host is “protected” simply because it should only be running the non-server version.
- Cloud versions of the tool were automatically patched by ConnectWise and therefore not considered directly impacted, but could impact other hosts.
If any of these processes exist on one of your machines, it is considered impacted by this vulnerability. If these server components are not needed on a specific machine, we would recommend removing them.
- ScreenConnect Web Server
- ScreenConnect Session Manager
- ScreenConnect Security Manager
- ScreenConnect Relay
What Do You Do if You’ve Already Experienced Signs of Compromise?
- Isolate any compromised Servers. The Huntress tool can be used for host and organization isolation.
- Stop or disable the following services to kill any ScreenConnect Sessions.
- ScreenConnect Web Server
- ScreenConnect Session Manager
- ScreenConnect Security Manager
- ScreenConnect Relay
- Reset any credentials the threat actor may have gained access to. If passwords were shared with multiple accounts, consider updating those as well.
- Patch the server to the latest ScreenConnect version and follow any updates on the official ConnectWise advisory.
- Deploy Huntress to the environment for 24/7 monitoring of known malicious activity.
- Start your incident response process. If you don’t have one, check out these resources for getting started.
What Is Huntress Doing for Partners?
- With the help of many of our internal team members, and partners as well, we successfully reproduced the vulnerability, began alerting our partners, and developed documentation with insight for the cybersecurity community.
- We have sent over 1,600 incident reports to partners with directions and steps to patch hosts up to version 23.9.8
- We’ve published documentation on how to find vulnerable autoruns via our portal.
- We released a “mitigation” vaccine to hosts running the vulnerable versions—this vaccine is not meant to be a long-term solution, and we strongly recommend that you still patch as soon as you can.
Helpful Resources for More Details:
- Understanding the ConnectWise ScreenConnect CVE-2024-1709 & CVE-2024-1708
- Detection Guidance for ConnectWise CVE-2024-1709
- Immediately Patch ScreenConnect 23.9.8
- SlashAndGrab: ScreenConnect Post-Exploitation in the Wild
We encourage customers and partners to reach out if they need assistance. If you are not currently using Huntress and need help monitoring for activity related to this vulnerability, you can use Huntress' free trial.















