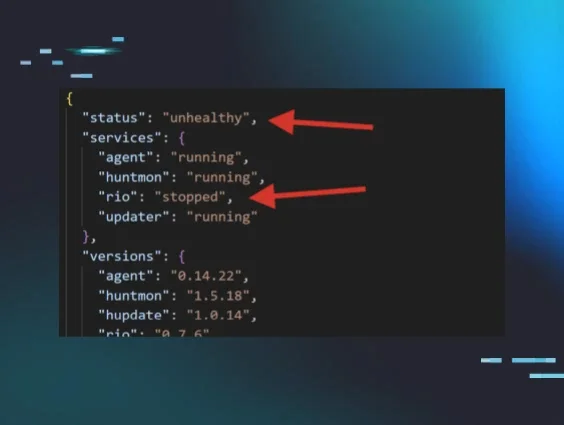
We are excited to introduce the next iteration of The Huntress Managed Security Platform with the addition of Huntress Managed Endpoint Detection and Response (EDR).
This solution adds managed EDR capabilities that provide an additional layer of security by actively monitoring scripts, executables and related activity to identify malicious processes. The data analyzed by Huntress Managed EDR is backed by our 24/7 Security Operations Center (SOC) team, which reviews all suspicious activity to validate threats, remove false positives and determine what remediation steps are needed—making it easy for even non-security teams to swiftly respond to cyber incidents.
Huntress was originally built to find and evict persistent threats, but we’ve always been chipping away to close the gap between enterprise and SMB cybersecurity protection. A lot has changed since we opened our doors in 2015, including the addition of External Recon to identify exposed services, Ransomware Canaries to detect and remove ransomware, and Managed Antivirus to combat malware. And now, with the addition of Huntress Managed EDR, we are one step closer toward delivering an end-to-end platform that helps protect our partners and customers at every stage of the modern attack lifecycle.
What Is Huntress Managed EDR?
Today’s cyberattacks are designed to evade traditional prevention and detection techniques. While attackers try to disguise their activities, Huntress Managed EDR makes it much harder for them to hide by providing continuous monitoring of process executions and associated metadata. This process data, combined with the data from other Huntress managed security services, creates a comprehensive view of cyber threats and an ability to find and stop malicious activity as it’s happening.
Unlike antivirus, which initially determines whether or not a file is suspicious, Huntress Managed EDR executes forensics every time an application is launched. The role of Managed EDR, as part of The Huntress Managed Security Platform, can be mapped out in five steps:
- Collect - The Huntress agent continuously captures process execution data including but not limited to its privilege level, command line arguments and lineage.
- Detect - Huntress applies custom-tuned detection logic to capture process data, making SOC Analysts aware of the suspicious activity that requires investigation.
- Analyze - SOC Analysts dig deep into the continuous stream of data to confirm the activity is indeed malicious, greatly eliminating false positives.
- Report - The Huntress SOC will provide you with a custom incident report sharing our findings and outlining next steps. This can be delivered via email or ticketing system.
- Remediate - You can execute the recommended automated remediation steps or get detailed instructions for additional work that should be completed.
Huntress Managed EDR is designed to show you exactly what’s happening inside your protected endpoints, providing unparalleled visibility and detection of organizational threats. Plus, all data captured by Huntress Managed EDR is stored for seven days to provide historical context. This enables our SOC team to complete greater analysis and map attackers' movement in the event of an incident.
EDR in Action: Protecting Your Endpoints from Today's Cyber Threats
Watch our on-demand webinar to see how managed EDR can help catch attackers red-handed.
What Will I Be Able To Do With Huntress Managed EDR?
We knew that visibility was the key to detecting advanced threats. That’s why Huntress Managed EDR is built to continuously monitor process executions and associated metadata with such granularity that makes it extremely hard for hackers to hide.
After several months in a public beta program, Huntress Managed EDR has already been put to the test and proved its value against some dangerous cyberattacks.
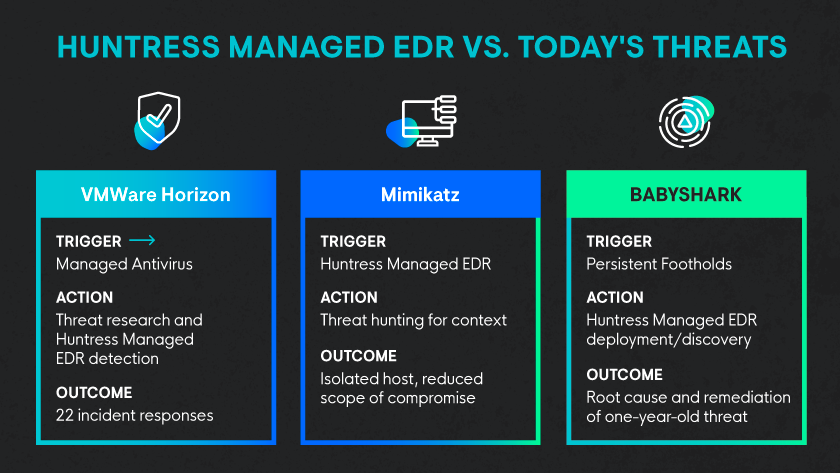
If you’re interested, check out this technical breakdown of how Huntress Managed EDR helped combat follow-on attacks against VMware Horizon servers in real time.
We also knew that cybersecurity has become increasingly more difficult and more expensive to manage. Many businesses have acknowledged the need for advanced security measures and have implemented EDR products. However, EDR products don’t make a business more secure just through implementation. EDR products require significant tuning to reduce false positives and need dedicated personnel to investigate alerts. This requires significant time, money and resources that most businesses lack.
To alleviate these challenges, we made sure to design Huntress Managed EDR to filter out noise and only deliver an incident report when a threat is verified, or action is needed. Not only does this cut down on false positives, it also makes it easy for non-security professionals to respond to threats because our SOC team is at your back providing additional context and instructions to remediate or take appropriate next steps.
Huntress is no longer just the ‘tool that finds what other tools miss.’ We are excited to deliver these new EDR capabilities to the SMB market, and to continue investing in the areas where our partners need the most help.
Want to learn more about Managed EDR and The Huntress Managed Security Platform? Read our reviews on G2 or watch this review video by Tom Lawrence.