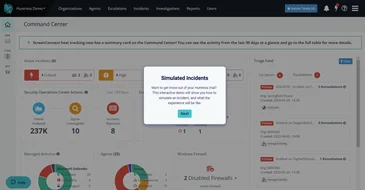
This tour will walk you through the Managed ITDR, Unwanted Access, and Rogue Apps dashboards, as well as an incident report.



Email spam filtering is just the first step. Huntress Managed ITDR spots what attackers do after initial access — like lateral movement, malicious app installs, and stealthy persistence.
We've sent a confirmation link to your email . Click the link to instantly access the Huntress platform.
The confirmation link will be active for 2 hours.
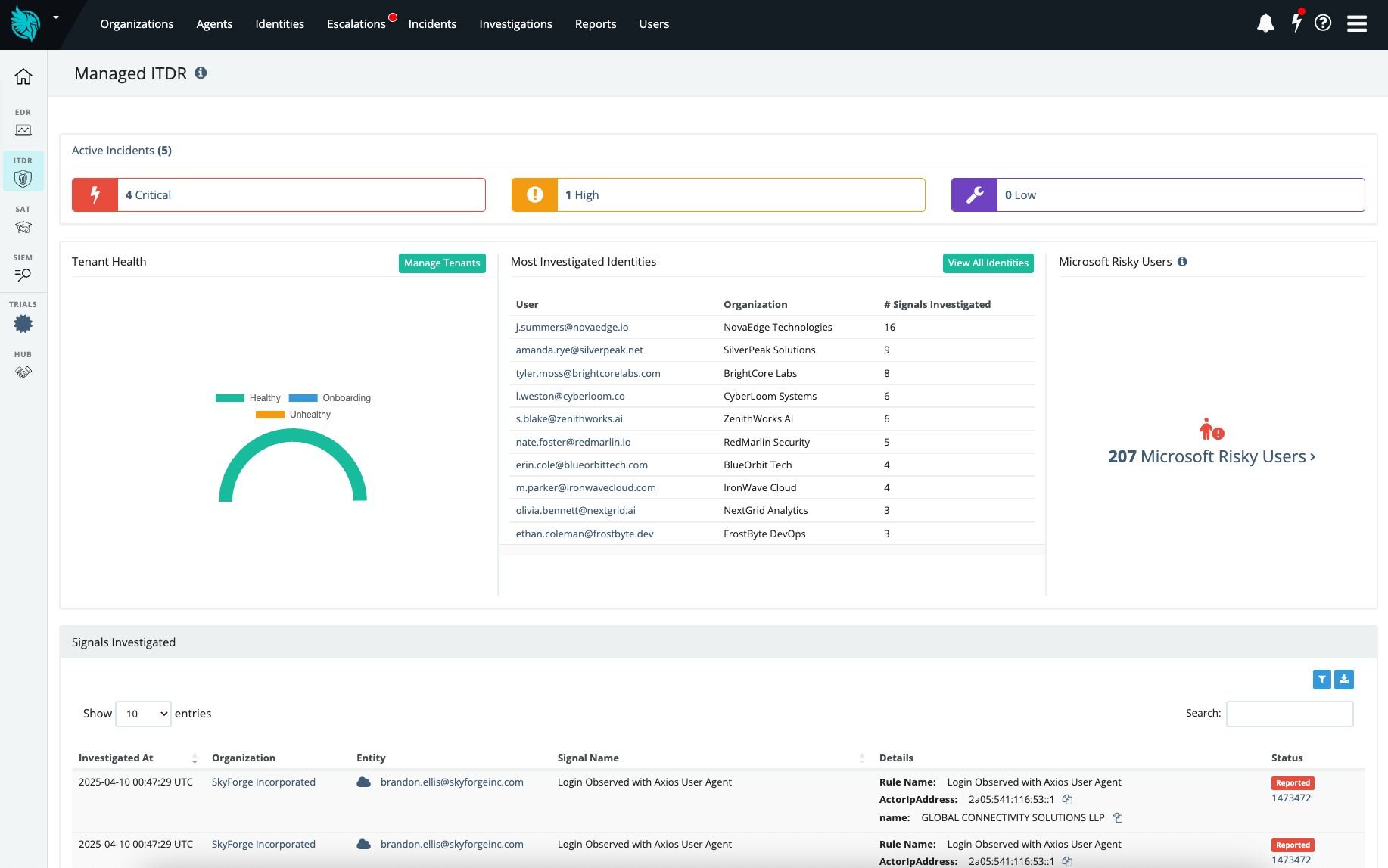
Your email spam filters are solid. Your SAT program is strong. But attackers still get through. What happens next is where most email security tools fall behind.
That’s where ITDR steps in.

Detects identity misuse after phishing or when your email is compromised

Secures Microsoft 365 identities with 24/7 continuous monitoring

Flags rogue apps and suspicious authentications attackers use post-breach

Provides real-time alerts + human-led investigations

Features a 3-minute mean time to respond (MTTR)

Huntress Managed ITDR is built and managed by identity security experts who provide advanced threat detection that targets critical risks, such as account takeovers and business email compromise (BEC).



Attackers grab session tokens—the digital keys that keep users logged in—and import them into their own browsers. No password needed, just instant access. Managed ITDR stops hackers from exploiting your systems and bypassing your 2FA/MFA.

When attackers snag usernames and passwords, this is the easiest way into your business. Managed ITDR keeps cybercriminals out by watching your identity assets and locking down identities.
Managed ITDR exposes unusual login locations and VPNs so only authorized users can access your data.

Don’t let malicious OAuth apps lurk in your Microsoft 365 environment—get a full view into every OAuth app installed across tenants and proactively find Traitorware and Stealthware before they can cause harm.

Business email compromise (BEC) isn’t just about tricking users; it’s about taking over your inbox. Managed ITDR spots unusual activity, protects your inbox, and keeps your emails secure and private.

Huntress Managed ITDR gives you fast containment, powerful remediation, and seamless recovery so threats don’t stand a chance.
Explore our Guided Demos to learn more about key functionality and capabilities of Huntress Managed ITDR


This tour will walk you through the Managed ITDR, Unwanted Access, and Rogue Apps dashboards, as well as an incident report.

This capability empowers Huntress to identify unsafe applications installed in a protected tenant. Tour Managed ITDR's latest step in wrecking hacker identity tradecraft.

Welcome to our new Managed ITDR capability: Unwanted Access. This capability focuses on detecting and responding to session hijacking and credential theft.




Email security is just the first line of defense. Huntress Managed ITDR is your safety net for everything that comes after.
