Key Takeaways
- Punycode is an encoding system that converts Unicode characters to ASCII for use in domain names.
- Attackers exploit punycode in homograph attacks to create fake domains that look identical to legitimate websites.
- A domain like
xn--pple-43d.comcan render asapple.comin some browsers, tricking users into entering credentials on phishing sites. - Protection strategies include browser configuration, employee training, DNS filtering, and endpoint detection and response (EDR) tools.
- Modern browsers increasingly display punycode rather than Unicode to help users spot malicious domains.
Punycode is an encoding syntax used to convert Unicode characters — such as characters from non-Latin scripts like Chinese, Arabic, or Cyrillic — into the limited ASCII character set supported by the Domain Name System (DNS). In cybersecurity, punycode is significant because attackers exploit it in homograph attacks: registering domains that visually mimic legitimate websites by substituting look-alike Unicode characters to deceive users into visiting malicious sites. Understanding punycode is essential for IT professionals, managed service providers (MSPs), and small-to-midsize businesses (SMBs) that want to defend against increasingly sophisticated phishing campaigns.
What Is Punycode?
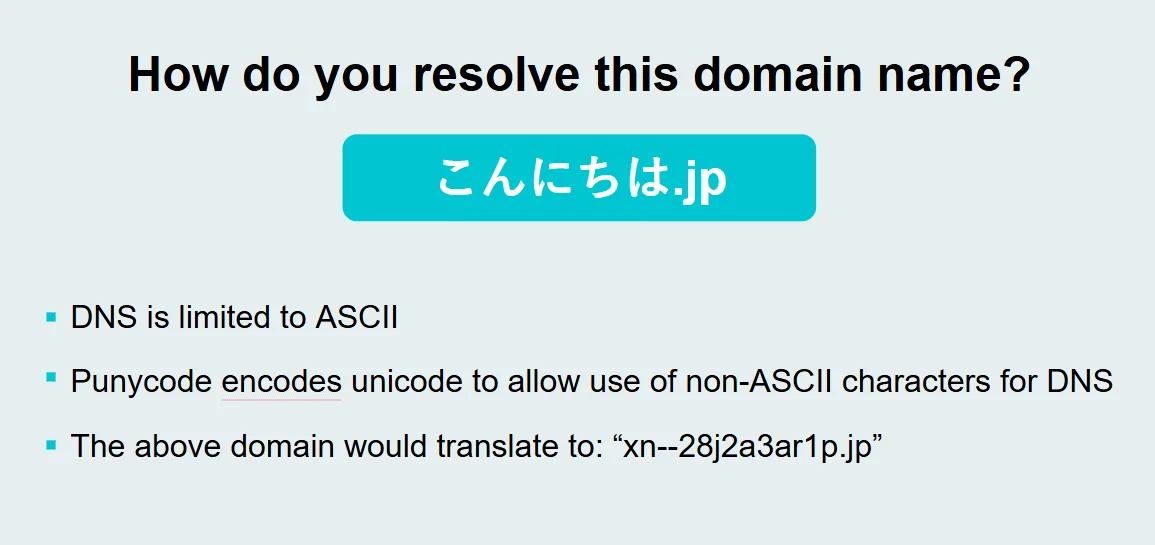
Punycode is an encoding standard defined in RFC 3492 that represents Unicode characters using only the limited ASCII characters permitted in domain names (letters a–z, digits 0–9, and hyphens). It was created to enable internationalized domain names (IDNs) — domain names written in non-Latin scripts — to function within the existing DNS infrastructure, which only supports ASCII.
For example, the German city name "münchen.com" contains the character "ü," which doesn't exist in ASCII. Punycode encodes this domain as xn--mnchen-3ya.com, allowing DNS servers to process it correctly. When a user visits this domain, their browser may decode the punycode and display the human-readable Unicode version in the address bar.
Why Does It Matter?
On one hand, Punycode powers Internationalized Domain Names (IDNs), enhancing internet inclusivity and accessibility worldwide. On the other hand, it gives cybercriminals a way to exploit visual similarities between Unicode and ASCII characters. This has created a pathway to some of the internet’s more cunning attacks.
How Does Punycode Work?
Punycode converts Unicode domain names to ASCII through a systematic encoding process. Here's how it works step by step:
- A Unicode domain is registered. A user or attacker registers a domain containing non-ASCII characters (e.g., "münchen.com" or a domain using Cyrillic characters that resemble Latin letters).
- ASCII and non-ASCII characters are separated. The encoding system identifies which characters in the domain name fall outside the standard ASCII range and need conversion.
- The Bootstring algorithm encodes non-ASCII characters. Non-ASCII characters are converted into an ASCII-compatible string using the Bootstring algorithm, a generalized variable-length integer encoding method specified in RFC 3492.
- The "xn--" ACE prefix is added. The resulting encoded domain receives the ACE prefix "xn--" to signal that it contains punycode. For example, "münchen.com" becomes
xn--mnchen-3ya.com. - DNS resolves the ASCII version. The Domain Name System processes only the ASCII punycode version of the domain to route the request to the correct IP address.
- The browser renders the domain. Depending on the browser's security settings and policies, the address bar may display either the original Unicode version (e.g., "münchen.com") or the raw punycode version (e.g., "xn--mnchen-3ya.com"). This rendering decision is where the security risk lies.
This entire process happens transparently and almost instantly. Users typically never see the punycode version unless their browser is configured to display it — which is exactly what attackers count on.
What Is a Punycode Phishing Attack (Homograph Attack)?
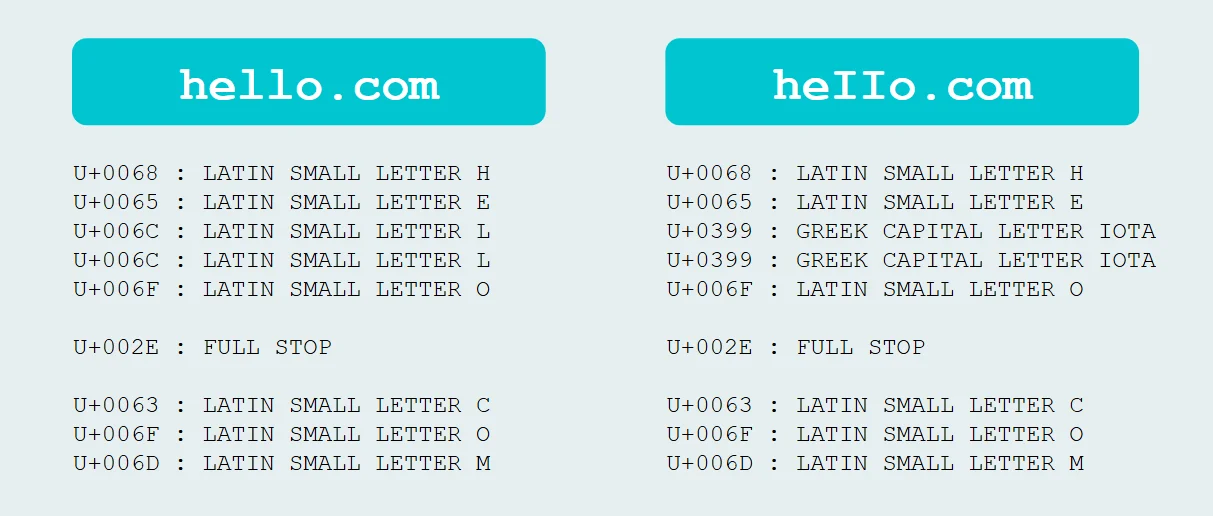
A punycode phishing attack — formally known as an IDN homograph attack — is a type of cyberattack where an attacker registers a domain name using Unicode characters that are visually identical or nearly identical to the ASCII characters in a legitimate domain. Because the Unicode characters have different underlying code points, the domain is technically different, but it looks the same to the human eye.
For example, the Cyrillic letter "а" (U+0430) is visually indistinguishable from the Latin letter "a" (U+0061) in most fonts. An attacker can register a domain that replaces one or more Latin characters with their Cyrillic look-alikes. The resulting domain appears identical to a trusted brand's website in the browser address bar, but it resolves to a completely different server controlled by the attacker.
The attacker then builds a convincing replica of the legitimate website — complete with login forms, branding, and SSL certificates — and uses phishing emails, ads, or search engine manipulation to drive victims to the fake site. When victims enter their credentials, payment information, or other sensitive data, the attacker captures everything.
This attack is particularly dangerous because it defeats one of the most common security tips: "check the URL before you click." In a punycode homograph attack, the URL looks correct even under scrutiny.
Why Punycode Is a Cybersecurity Concern
Here’s the issue: Unicode allows the creation of lookalike characters (homographs). When bad actors hop on this train, they can spoof legitimate domains and trick users into visiting malicious websites. Let’s see how it works.
The Good Side of Punycode
Inclusivity: Businesses in Japan, China, and the Middle East can register local-language domain names.
User experience: Consumers type web addresses using characters familiar to them.
The Dark Side of Punycode
Homograph Attacks: Ever heard of “microsоft.com”? Notice the subtle swap? That’s not an “o” from the Latin script; it’s a character from Cyrillic that looks eerily similar. Hackers register fake domains that visually replicate trusted brands and use them for phishing and malware campaigns.
Evasion of Detection: Punycode-encoded domains often slip through email filters, DNS blocklists, and even experienced cybersecurity eyes.
Real-World Examples
Coinbase Phishing Attack: A targeted phishing email used the fake domain “cоinbase.com” (with a Cyrillic “о”). It successfully lured victims to enter their credentials on a fraudulent page.
Invoice Fraud: Attackers impersonated an executive’s email, using “ì” (Latin character with an acute accent) in place of a regular “i.”
Anatomy of a Punycode Attack
1. Homograph Attacks
Homograph attacks rely on lookalike characters to spoof domains. A few examples include:
Cyrillic “а” (U+0430) vs ASCII “a”
Greek “τ” (U+03C4) vs ASCII “t”
This trick convinces users they’re visiting legitimate websites when, in fact, they’re not. A couple of classic Punycode translation examples include:
xn--pple-43d.com → аррӏе.com (fake “apple.com”)
xn--microsft-5xa.com → micrоsоft.com (fake “microsoft.com”)
2. Hiding in Plain Sight
Encoded strings, like xn--paypal-4ve.com, often appear harmless in email headers or logs, bypassing regex URL filters.
3. Bypassing Legacy Tools
Older Secure Email Gateways (SEGs) and security tools may not fully decode or analyze Punycode, allowing attacks to slip through unnoticed.
4. Spoofing Emojis in Domains
Even emojis get Punycode treatment. For example, 🌐.com translates to xn--i-7iq.com, making a phishing campaign even harder to detect, thanks to its novelty.
Why Punycode Attacks Are Extra Dangerous
Punycode attacks are like ghosts in the IT machine—not easily spotted and nearly impossible to stop if you’re unprepared.
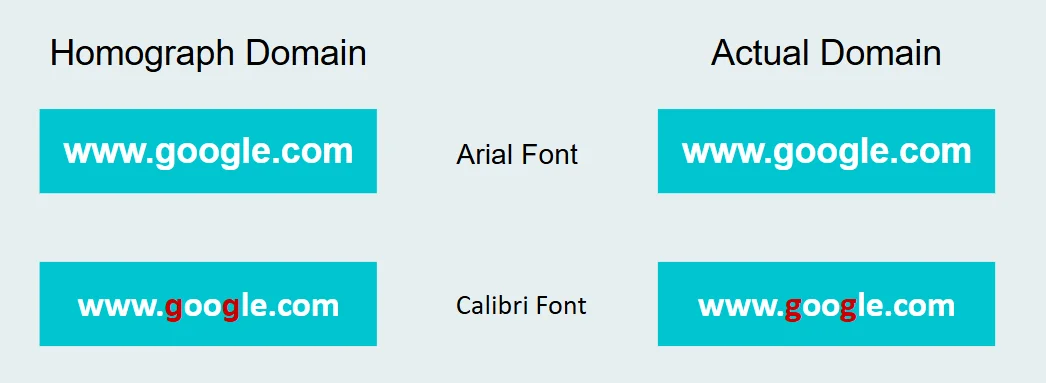
Undetectable to Users: Unicode lookalikes can be visually identical to legitimate URLs, particularly in certain fonts or low-res settings.
Exploiting Mobile Devices: Tiny screens, lack of hover previews, and urgent browsing make mobile users particularly vulnerable.
Browser Discrepancies: While Chrome may display raw Punycode, Safari often renders Unicode, creating inconsistency in detection.
How Do Hackers Use Punycode in Cyberattacks?
Hackers use punycode as a foundational tool in several types of cyberattacks that target human perception rather than technical vulnerabilities. The most common attack methods include:
Credential Harvesting Phishing Campaigns
The most prevalent use of punycode in cyberattacks is phishing. Attackers register a homograph domain, build a pixel-perfect clone of a target website (such as a bank, email provider, or SaaS application), and send phishing emails directing victims to the fake site. Because the domain appears legitimate, victims enter their usernames and passwords without suspicion. The attacker harvests these credentials and uses them to access real accounts, sell them on dark web marketplaces, or launch further attacks.
Business Email Compromise (BEC) Setup
Attackers use punycode domains to impersonate executives, vendors, or partners in business email compromise schemes. By registering a homograph domain that matches a company's real domain, the attacker can send emails that appear to come from a trusted source — requesting wire transfers, sensitive documents, or changes to payment information.
Malware Distribution
Homograph domains serve as convincing delivery mechanisms for malware. An attacker creates a fake software download page on a punycode domain that mimics a trusted vendor. Victims searching for legitimate software may land on the fake site and download trojanized installers that deploy ransomware, remote access trojans (RATs), or information stealers.
Watering Hole Attacks
In targeted campaigns, attackers identify websites frequently visited by employees of a specific organization, register homograph versions of those domains, and redirect or lure targets to the spoofed sites. These watering hole attacks can deliver tailored payloads designed to compromise specific networks.
Supply Chain Attacks
Punycode domains can be used to impersonate software repositories, API endpoints, or update servers. If a developer or automated system is tricked into connecting to a homograph domain instead of the legitimate service, the attacker can inject malicious code into the software supply chain.
How Can You Detect a Punycode Attack?
Detecting punycode attacks requires a combination of technical controls and human awareness. Here are the most effective detection methods:
- Look for the "xn--" prefix. If a URL contains "xn--" at the beginning of the domain name, it is a punycode-encoded internationalized domain name. While not all punycode domains are malicious, unexpected "xn--" prefixes in business contexts are a red flag.
- Configure your browser to display punycode. Most modern browsers can be set to show the raw punycode version of IDN domains instead of rendering the Unicode characters. In Firefox, set
network.IDN_show_punycodetotrueinabout:config. Chrome and Edge now display punycode by default for domains that mix scripts from different languages. - Hover over links before clicking. Before clicking any link in an email, message, or document, hover over it to inspect the actual destination URL. Look for unusual characters, unexpected domains, or the "xn--" prefix.
- Use URL inspection tools. Online punycode decoders and URL scanners can reveal the true Unicode characters behind a punycode domain, making it easier to identify substitutions.
- Deploy DNS filtering and threat intelligence. DNS security solutions can flag or block known homograph domains and newly registered domains that match patterns associated with punycode attacks.
- Monitor SSL certificate transparency logs. Certificate Transparency (CT) logs record all publicly issued SSL certificates. Monitoring these logs for certificates issued to domains that closely resemble your organization's domain can provide early warning of impersonation attempts.
- Implement email security with homograph detection. Advanced email security gateways and phishing detection tools can analyze URLs in inbound emails for punycode encoding and flag messages containing homograph domains.
How Do You Protect Against Punycode Attacks?
Protecting your organization from punycode attacks requires a layered defense strategy that combines technology, training, and process. Here's how to build comprehensive protection:
Browser and Endpoint Configuration
- Configure all organizational browsers to display punycode instead of rendering Unicode for IDN domains.
- Deploy browser extensions or endpoint policies that warn users when they navigate to punycode-encoded domains.
- Keep browsers updated — modern versions of Chrome, Edge, Firefox, and Safari have built-in protections against mixed-script homograph domains.
Employee Security Awareness Training
- Train employees to recognize punycode attacks as part of regular phishing awareness programs.
- Teach staff to bookmark important sites and navigate to them directly rather than clicking links in emails.
- Conduct simulated phishing exercises that include homograph domain examples.
- Emphasize that even "correct-looking" URLs can be malicious.
Email Security
- Deploy email security solutions with advanced URL analysis capable of detecting punycode and homograph domains.
- Implement DMARC, SPF, and DKIM to reduce the likelihood of spoofed emails reaching inboxes.
- Configure email gateways to flag or quarantine messages containing links to newly registered domains or punycode-encoded URLs.
DNS Security and Filtering
- Use DNS filtering services that maintain blocklists of known homograph domains and flag suspicious IDN registrations.
- Monitor for newly registered domains that resemble your organization's domain or key vendor domains.
Domain Registration Defense
- Proactively register punycode variations of your organization's primary domain to prevent attackers from claiming them.
- Register common homograph variations using Cyrillic, Greek, and other scripts that contain look-alike characters.
- Use domain monitoring services to receive alerts when similar domains are registered by third parties.
Endpoint Detection and Response (EDR)
- Deploy EDR solutions that can detect and block connections to known malicious domains, including homograph domains.
- Use threat intelligence feeds that include punycode domain indicators of compromise (IOCs).
- Ensure your EDR platform provides visibility into DNS queries, browser activity, and network connections to identify phishing infrastructure before credentials are compromised.
FAQs about Punycode in Cybersecurity
Punycode is an encoding system that converts Unicode characters (like those in non-Latin scripts such as Chinese, Arabic, or Cyrillic) into ASCII characters so they can be used within the Domain Name System (DNS). For example, “münchen.com” becomes “xn--mnchen-3ya.com.”
Punycode can be exploited in homograph attacks, where cybercriminals use lookalike characters from Unicode to mimic legitimate domains. For instance, “microsоft.com” (using a Cyrillic “о”) can deceive users into thinking they’re visiting a trusted site, leading to phishing or malware distribution.
Look for domains that have a prefix like “xn--.” This indicates they’ve been encoded with Punycode. Tools and browser settings can help display the raw Punycode instead of the Unicode representation.
Businesses can:
- Train employees to recognize phishing attempts and homograph attacks.
- Utilize domain monitoring services to flag fraudulent registrations.
- Enable browser settings that force ASCII display for better visibility.
- Implement advanced DNS filtering to catch suspicious activity.
Yes, there are online decoding tools that can convert Punycode back to its Unicode representation. These tools are valuable for verifying suspicious URLs and preventing phishing attacks.



Related Cybersecurity Terms
- Internationalized Domain Name (IDN): A domain name that contains characters from non-ASCII scripts, such as Arabic, Chinese, Cyrillic, or Devanagari. IDNs rely on punycode for DNS compatibility.
- Homograph attack: A cyberattack that exploits visual similarities between characters from different writing systems to create deceptive domain names, URLs, or usernames.
- ACE (ASCII Compatible Encoding): The encoding format that uses the "xn--" prefix to identify punycode-encoded domain names within the DNS system.
- Bootstring: The general-purpose algorithm defined in RFC 3492 that forms the basis of punycode encoding, converting variable-length integer sequences into compact ASCII strings.
- Typosquatting: A related but distinct attack technique where attackers register misspelled versions of popular domains (e.g., "gogle.com"). Unlike homograph attacks, typosquatting relies on typing errors rather than visual character deception.
- DNS filtering: A security control that blocks access to malicious or suspicious domains at the DNS resolution level, preventing users from connecting to phishing sites, malware distribution servers, and homograph domains.
- Endpoint Detection and Response (EDR): A cybersecurity solution that monitors endpoint devices for suspicious activity, including connections to malicious domains, and provides tools for investigation and remediation.
Staying Ahead of Punycode Exploits
Punycode was built to make the internet inclusive, but that inclusivity comes with risks. For cybersecurity professionals, staying ahead of these exploits means staying informed.
At the end of the day, defending against Punycode phishing isn’t just about having tools; it’s about visibility, vigilance, and action. Train your team, harden your systems, and keep one eye on that seemingly harmless “xn--” prefix.
Special thanks to Dave Kleinatland for the graphics in this guide.


Provide an Impactful SAT Experience
Don’t just check a compliance box. Elevate your workplace’s security culture while giving your employees an enjoyable experience.