TTPs, or Tactics, Techniques, and Procedures, refer to the methods attackers use to plan, execute, and achieve their objectives in a cyberattack. They outline how threat actors operate, giving cybersecurity professionals crucial insights into the lifecycle of an attack.
Understanding TTPs helps organizations recognize early warning signs of malicious activity and build proactive defenses that mitigate potential damage.
Key Takeaways
-
Learn what TTPs (Tactics, Techniques, and Procedures) are and why they matter.
-
Understand how studying TTPs aids in threat detection and defense.
-
Explore real-world examples of how TTPs reveal attacker behaviors.
-
Learn how TTPs fit into cybersecurity frameworks like the MITRE ATT&CK.
-
Get actionable insights to strengthen your security posture.
Digging Deeper Into TTPs
Breaking Down TTPs
TTPs are essentially the playbook for cybercriminals. Here’s how they break down:
Tactics: The overarching goal of an attack. For example, a tactic might be data theft or deploying ransomware.
Techniques: The methods used to achieve that goal. A technique could be phishing emails targeting employees for login credentials.
Procedures: The specific steps or processes carried out during an attack. For instance, a threat actor using a phishing email might craft a message impersonating a trusted vendor.
By analyzing TTPs, cybersecurity teams can predict future actions of attackers, identify vulnerabilities, and prioritize defenses.
Why Do TTPs Matter?
Cybersecurity is all about staying ahead of the bad guys. TTPs provide a roadmap for how attackers operate, making it possible for security professionals to:
Analyze behavior patterns and anticipate moves.
Detect unusual activity in networks or systems.
Focus on proactive defenses like threat hunting.
For example, using a framework like MITRE ATT&CK, teams can map TTPs to better understand criminal strategies.
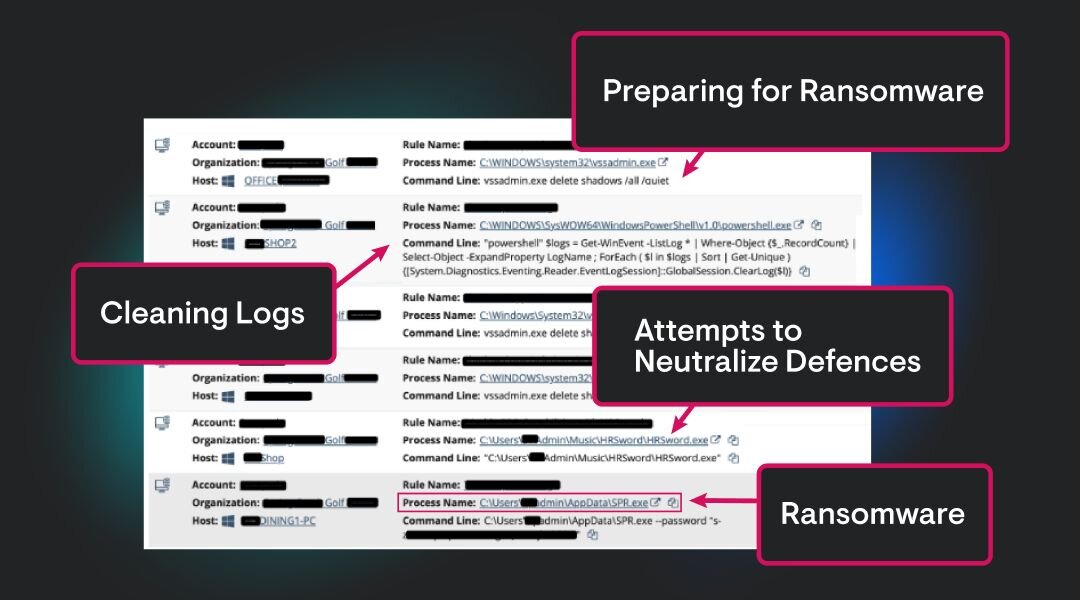
Real-World Example
In a ransomware attack, the tactic is impact: denying availability of data and systems to pressure the victim into paying. A common technique is exploitation of Remote services, such as abusing Remote Desktop Protocol (RDP) to gain initial access. The procedure may involve deploying ransomware that encrypts system files with strong algorithms, deletes backups, and leaves a ransom note. Detecting early signs of this chain - like suspicious RDP activity or rapid file encryption - can help stop the attack before it succeeds.
TTPs in Threat Intelligence
Studying TTPs isn’t just about reacting to attacks; it’s about staying prepared. Solutions like Managed Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) use TTP analysis to flag behaviors often linked to cyber threats.
For example, a login attempted at 3 a.m. from an unusual IP address might be tied to a brute force procedure aligned with a known TTP profile. Knowing this, your team can investigate and halt the attacker before damage occurs.
FAQs About TTPs
TTP stands for Tactics, Techniques, and Procedures, which describe how threat actors plan and execute attacks.
Analysts study TTPs to anticipate threats, detect suspicious activity, and defend against attacks.
TTPs focus on how attacks are carried out, while IOCs are the evidence that an attack has occurred, like malicious IP addresses or files.
Yes, MITRE ATT&CK organizes TTPs into a comprehensive framework for understanding adversary behavior.
Invest in threat intelligence systems, train employees, and adopt frameworks like zero-trust and MITRE ATT&CK to predict and block TTP-based attacks.


Closing Thoughts
TTPs are a window into the strategies and behaviors of today’s threat actors. By gaining an understanding of these patterns, cyber professionals gain the upper hand, detecting unexpected activities and thwarting cyber attacks before they escalate. Whether you’re managing a sprawling network or protecting a small business, understanding TTPs is a non-negotiable step in modern cybersecurity.
This knowledge equips organizations to recognize the bad threat actors lying in wait and outsmart them at every turn.


Protect What Matters