
Regardless of your daily duties, we’ve all encountered annoying ads, unwanted pop-ups, or generically named rogue applications. These nuisances, commonly called Potentially Unwanted Programs (PUP), are often unknowingly installed when downloading free software.
In this two-part series, we’re bringing you the scoop on the most common flavors of PUP we have seen as we continually validate the security of the systems we protect. This article will enable you to articulate the risks PUP can pose to your customers so you can better triage and polish your response efforts.
1. Adware
Simply put, adware is the name given to software that delivers distracting or unwanted advertisements to your end users. We rarely consider how these pop-ups, inline adverts, and annoying browser toolbars negatively impact our clients’ perception of the IT department. A common example of this is when a user follows an ad to a less-than-reputable website:
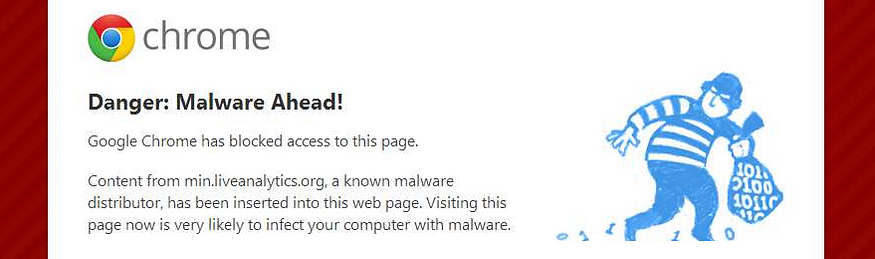
As techies, we all know this screen means that Chrome prevented the user from visiting a known malicious website. Unfortunately, this warning page can still generate help desk calls (likely reassuring Jason from HR that he’s not actually compromised).
Fake update advertisements are also capable of undermining the quality of your IT services. Despite the hard work it took to wrangle your RMM/SCCM into correctly patching your hosts, it only takes a handful of misleading “out of date” pop-ups to wipe out a client’s confidence. 😞

Takeaway: If you know your PUP problem is only adware, you likely don’t need to “roll trucks” or bring in the on-call technician. Waiting until Monday poses minimal risk and the removal process gives you an opportunity to “rescue” one of your customers. Just don’t forget about resolving the issue later.
2. Browser Hijackers
Similar to adware, browser hijackers pose another common threat to a user’s internet experience. As the name suggests, hijackers are Potentially Unwanted Programs that take control of certain browser functionality without a user’s consent in order to benefit the software creator. In most cases, these hijackers come in the form of custom homepages, redirected search queries, and installed toolbars/extensions. Needless to say, they are a source of countless unwanted help desk tickets.

Browser hijackers are often designed to provide businesses and criminals lucrative revenue streams that toe the line between unethical and illegal. Some hijackers make money by reselling collected information for marketing purposes (this often includes user data such as demographics and browsing habits). Others profit from redirecting traffic to affiliate links. An example of this is the Good-search.ml Homepage Hijacker which modifies victims’ shortcuts to forcibly open the browser to a redirecting homepage.
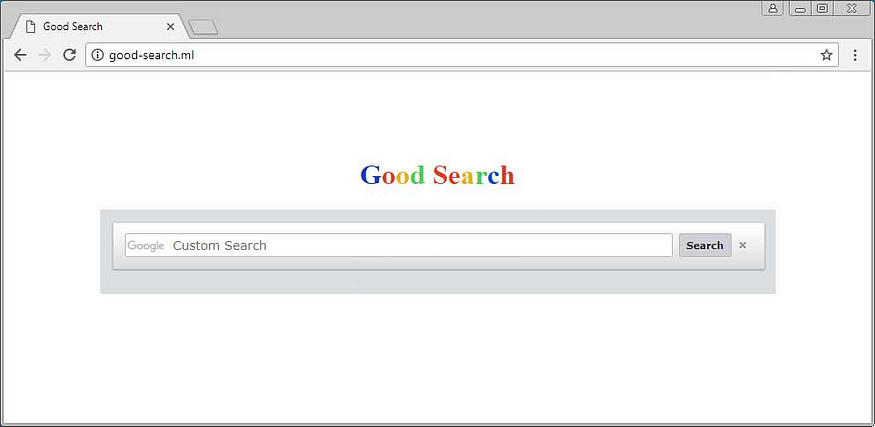
Takeaway: Browser hijackers come in many forms. Some will only pester your end users while others can put their data in danger. It’s important to identify which hijacker is installed and what threat it poses in order to prioritize your remediation efforts.
3. Bundled Software
When faced with a technical problem in 2018, many users turn to free apps for a solution. During these short-term crises, the last thing on their mind is verifying what they’re downloading or reading the “Terms and Conditions”. Unfortunately, these decisions can come with major consequences as free software notoriously bundles together all kinds of annoying and potentially dangerous programs.
As illustrated in How-To Geek’s article above, even the most popular downloads from major websites can lead to Potentially Unwanted Programs. At Huntress Labs, we’ve recently seen an uptick of systems running YahooChrome and the Businessconnectads.com Proxy which are both silently bundled with free software. When YahooChrome is installed, it adjusts the browser’s security settings to allow popup advertisements and redirects search queries (adware and browser hijacking). As for the Businessconnectads.com Proxy, it configures the browser to send all web traffic through a locally installed proxy server capable of monitoring the victim’s traffic and injecting advertisements.
On the more nefarious end of the spectrum, there have been several incidents this year where bundled software was leveraged to distribute applications capable of spying on victims, performing denial of service attacks, and mining cryptocurrency without user’s knowledge.
In Part II of this series, we’ll explore several of these recent campaigns where malicious actors used PUP to deliver malware.
Takeaway: Bundled software may not always trigger an IT armageddon, but its presence signals poor computer hygiene. In an ideal world, application whitelisting would be utilized to prevent an unprivileged user from installing unwanted software within their own profile. With PUP out of the way, it’s one less thing for an auditor or competitive Managed Service Provider to leverage against you.
Parting Thoughts
Unlike malware, Potentially Unwanted Programs generally aren’t designed to to damage computers. However, you can easily imagine how adware, browser hijackers, and bundled software:
- Hassle your end users and interfere with productivity
- Negatively shape your customers’ perception of your service
- Ultimately undermine an IT department’s hard work
To move beyond commodity security services, it’s important to prioritize your response efforts against Potentially Unwanted Programs. Remember, not all PUP means doom-and-gloom to your customers. In our experience, the key to a successful response strategy hinges on early detection and a detailed understanding of the risk each unique threat presents.

Looking to discover unwanted software and other hacker footholds lurking within your networks? Sign up for our free trial and let us show you how our new layer of detection complements your existing security stack!















