Qakbot has been spreading like wildfire. Huntress has seen a 400% increase in Qakbot cases in the past two months (several hundred incidents) in comparison to numbers from all of 2022 spread out over our 1.8 million protected endpoints.

What You Need to Know
QakBot is continuously maintained and developed and has evolved from a banking trojan information stealer, to form botnets, and into a delivery agent for ransomware. It is modular in nature enabling malicious cyber actors to configure it to their needs. (CISA, 2021)
Check out the below video to watch our interview with MSP Media Network—or keep reading to learn more.
1. The threat primarily comes in via email.
Based on Huntress’ telemetry in Q3/Q4 2022, Qakbot’s initial access has been primarily through email HTML attachments that drop a ZIP into the user’s Downloads folder (`C:\users\*\downloads\*.zip`). Users then unzip and interact with the .LNK (Windows shortcut), which mounts an ISO, where Qakbot then begins its malicious execution and persistence.
Prevention is key to keeping this threat in check.
- Minimize your or your clients' attack surface by using an email filtering system
- Educate your users on how to deal with this threat via security awareness training
The real Qakbot execution begins once a user clicks on a .LNK contained within the .ISO. This second .LNK will typically trigger a short obfuscated script (.cmd or .js are common), which then locates and executes a Qakbot .DLL.
The Qakbot DLL is typically executed via regsvr32.exe or rundll32.exe.
Huntress also observed legitimate applications (calc.exe, control.exe) used to load the malware via .dll sideloading.
In these cases, the qakbot DLL and “legitimate” application will both be located within the mounted .iso file.
- Eg `regsvr32 gaffes\twinkle.dll` (utilising regsvr32)
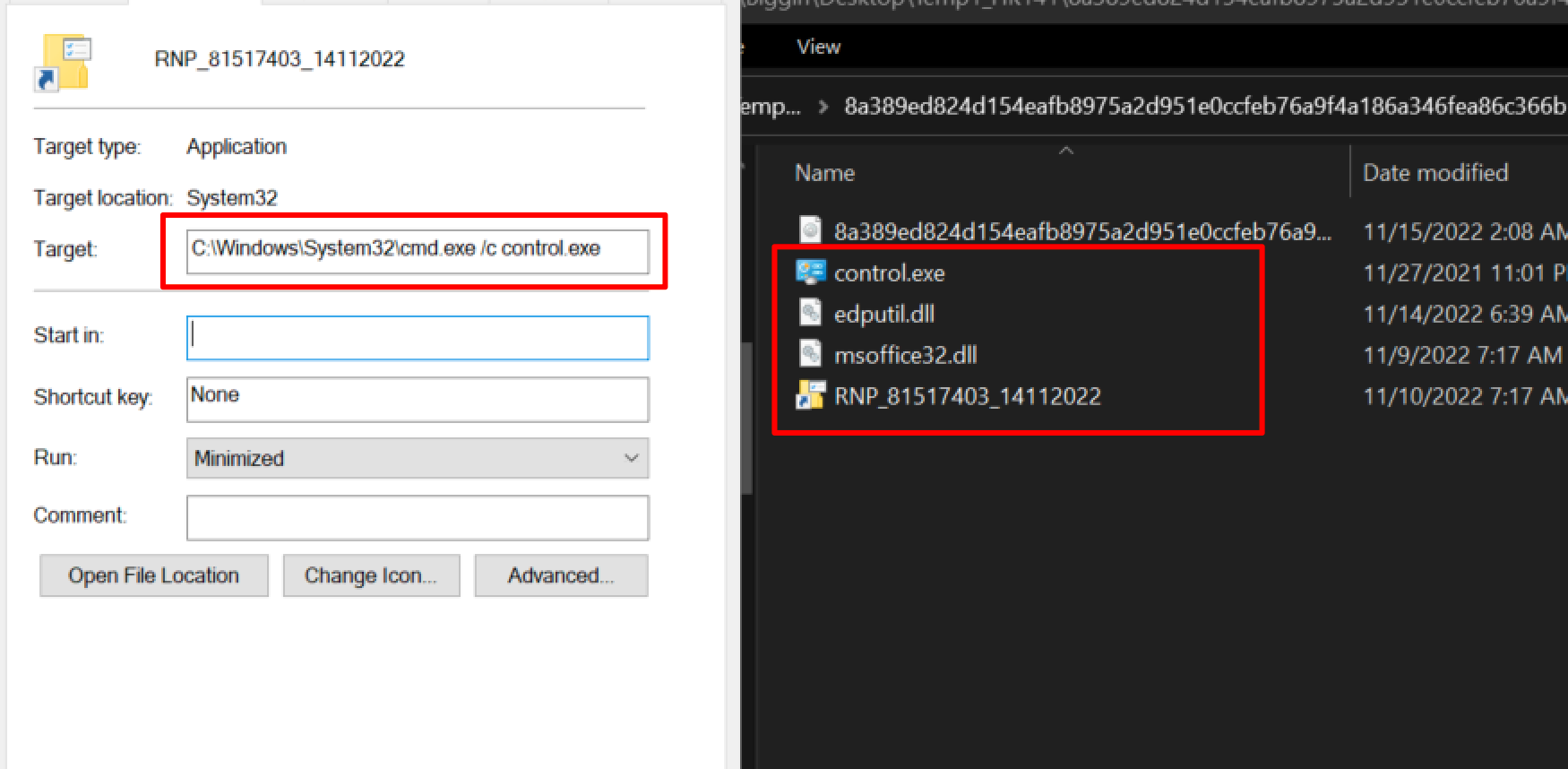
- Cmd.exe /c control.exe (utilising dll sideloading)
2. One way Qakbot launches is by mounting an ISO—but you can limit this capability by editing the registry.
We have seen Qakbot launch by mounting an ISO or VHD. You can limit this capability by editing the registry.
This article (updated 12/6/22) has a great write-up on how to limit mounting an ISO. By the way, if some workstations need to work with ISOs, then maybe this isn’t the mitigation to apply to them and, instead, rely on more aggressive monitoring. The name of the game is risk mitigation and lessening your attack surface.
3. Qakbot is known to evade antivirus (AV) tools.
The developers of Qakbot continue to update their software, making detection via next-gen AV (NGAV) challenging. Here’s why:
- It relies on user interaction for its initial execution and early-stage unraveling
- It actually doesn’t do anything malicious for the middle stage of its activities except mount and unravel folders
- The “middle stage” activities are updated regularly, turning reliable detection into a constant cat-and-mouse game
- When it does do something malicious, it leverages process injection techniques to evade many AV solutions
Managed endpoint detection and response (EDR) solutions that see the processes executing and prevent their spread are critical for early remediation.
Below we can see the “Control.exe” from before. Silently it uses dll sideloading to load edputil.dll. Before ultimately executing msoffice.dll (qakbot) via regsvr32.
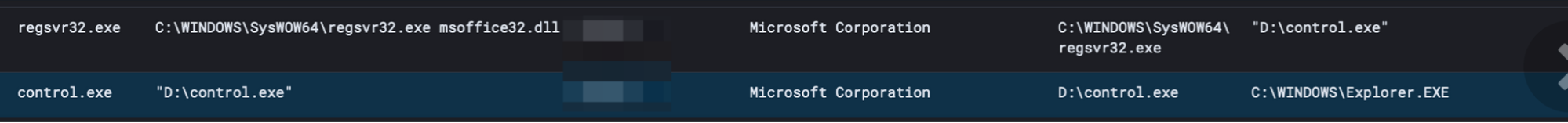
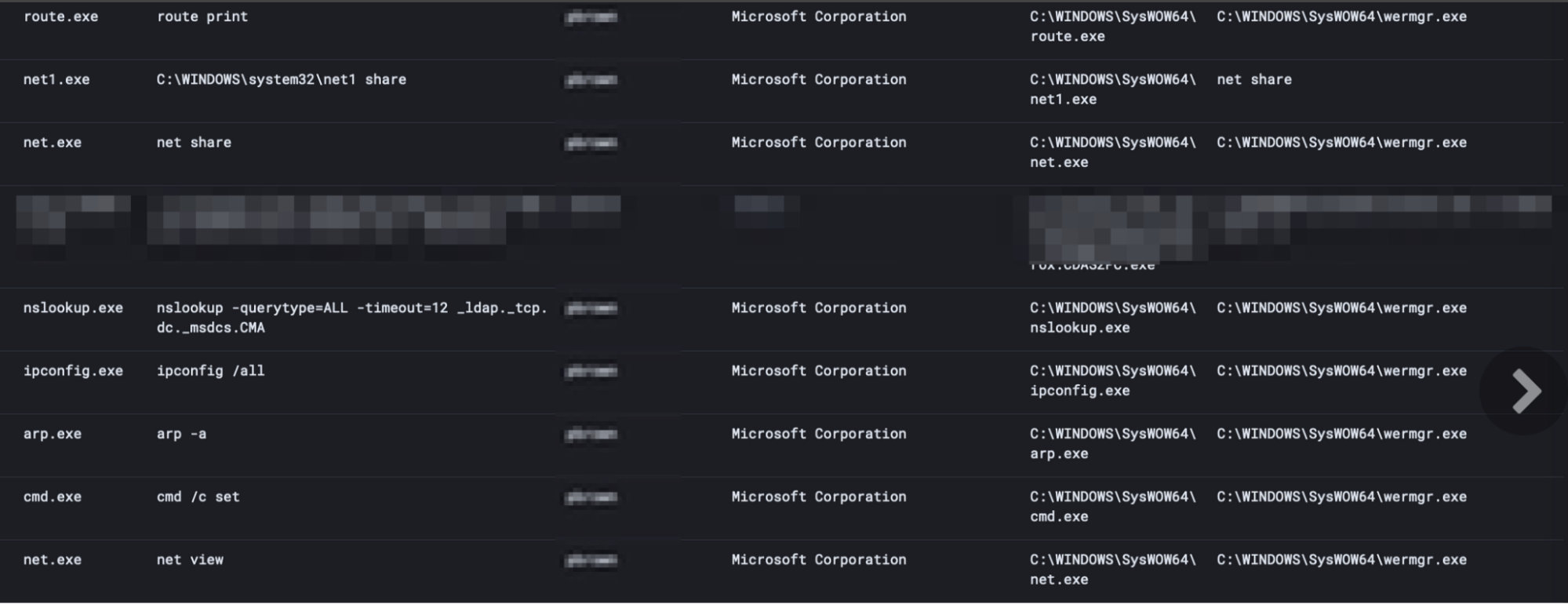
After successfully executing and injecting into wermgr.exe (a common qakbot target), we can also observe common enumeration commands executed via Qakbot.
Qakbot contains an embedded and encrypted list of commands that can be run. The team developed a script to extract these using Dumpulator. A subset of which looks like this:
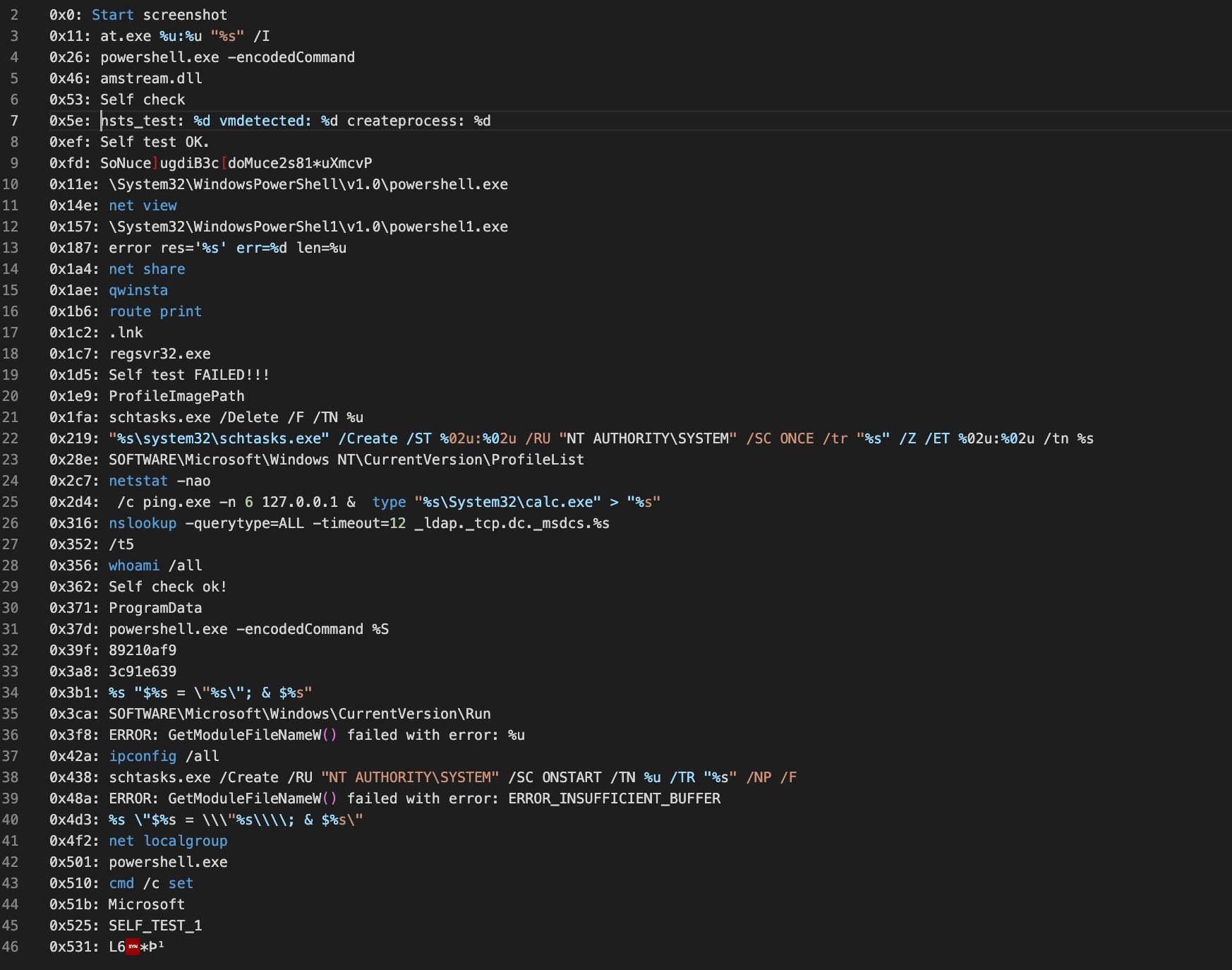
Once executed successfully, Qakbot will move itself to a new folder and create persistence via a RunKey or Scheduled Task (depending on available privileges). Both of these utilize regsvr32 and rundll32 in conjunction with random file and folder names.
Keep an eye out for things like these:
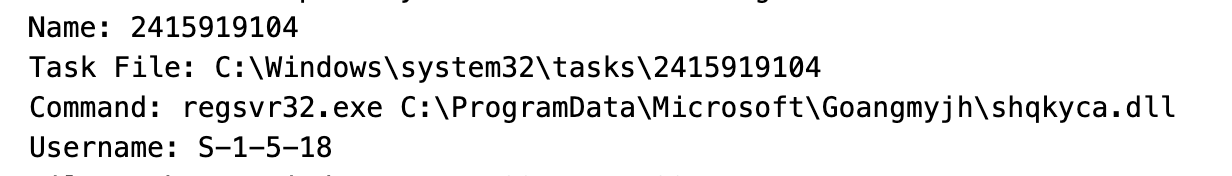

4. Basic cyber hygiene is your friend.
It may seem redundant to mention patching and updating, but they are the most basic form of cyber hygiene available. Never underestimate the power of performing these two simple tasks. Create an expected cadence for this activity, so it is always on the radar and not overlooked.
For example, Microsoft is always releasing security updates that try to mitigate/address known attack vectors. Patching regularly and consistently will keep your endpoints protected.
5. Disable administrative shares on workstations.
Some but not all variants of Qakbot propagate to multiple machines via SMB shares, so disabling SMB shares may be appropriate as a potential preventive measure.
Caution: This hardening may have other side effects, so review your environment and make sure it won’t have negative consequences.
- Some RMM software requires access to administrative shares for installs.
- For more information on disabling admin shares, follow this KB article.
6. If Qakbot gets into an environment, deal with it quickly.
The longer it stays, the harder it is to kick out. In addition, Qakbot has self-defense mechanisms such as the ability to detect a shutdown and, if running in memory, will spawn persistence on shutdown.
Isolating infected hosts from the rest of the network is key to stopping the spread.
Unfortunately, this is the type of threat best dealt with hands-on. We all love to fix issues remotely, but you are going to have better success with boots on the ground at the client/user’s site.
- Some of the most successful cases of handling Qakbot have involved partners who set up a dedicated LAN that does talk to the rest of the network (something as simple as an old router separating the infected machines from the rest of the network)
If you do see an active Qakbot infection in your network, check out this KB article packed with handy remediation steps.
7. With Qakbot, you need to understand and set expectations with your clients about what the "win" is when fighting this malware.
Winning is catching and evicting the threat actor before they can leverage this access to create a botnet, exfiltrate data or spread ransomware.
This includes mass isolation of entire networks to contain the threat. While we have seen organizations go offline for an entire day, it is better to be slow and thorough in order to avoid reinfection and having to repeat the process again.
What You Should Do
Your call to action is to take action to reduce your client’s attack surface and start the conversations now about potential downtime.
It is a whole lot easier to have these conversations when things are working instead of having to talk about it in the middle of an incident.















