Our CEO, Kyle, recently received the ad below, found on an online forum frequented by cybercriminals.
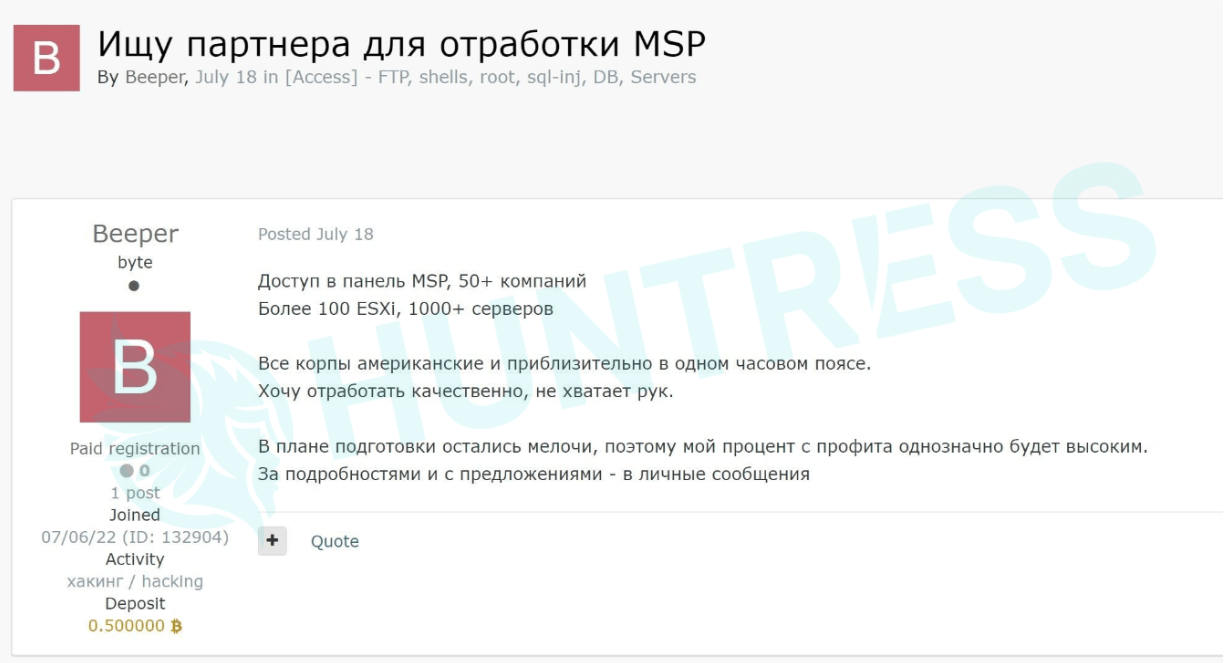
The body of the ad, translated into English, reads:
Looking for a Partner for MSP processing.
I have access to the MSP panel of 50+ companies. Over 100 ESXi, 1000+ servers.
All companies are American and approximately in the same time zone. I want to work qualitatively, but I do not have enough people.
In terms of preparation, only little things are left, so my profit share will be high.
Please send me a message for more details and suggestions.
Around the same time, Kyle was getting access to information about the ad, @Intel_by_KELA posted this Tweet:
Spotted: Initial Access Brokers using "ransomware insurance" as an important metric for their buyers, in addition to revenue, sector, access type and level of privileges.
Spotted: Initial Access Brokers using "ransomware insurance" as an important metric for their buyers, in addition to revenue, sector, access type and level of privileges. pic.twitter.com/ahu3SQqbvG
— KELA (@Intel_by_KELA) July 26, 2022
In the Tweet above, the image on the right is the contents of the image on the left, translated into English, and reads:
Sale RDP admin access for UK companies.
$5m+ revenue
Company has ransomware insurance.
Pm if interested
Both of these images illustrate a concerning and not-often-discussed trend of specialization in cyberattacks, specifically as it applies to initial access brokers (IABs).
Both ads illustrate that someone (a hacker) has gained access to an organization, unbeknownst to that organization, for the express purpose of offering that access for sale to other parties.
While the Tweet illustrates the various metrics offered up to buyers (access method and privileges, geographic location, revenue, insurance coverage, etc.), the image from the forum is perhaps more alarming, as it illustrates access to a managed service provider (MSP), who then has access to 50 or more customers.
It wasn’t so long ago that the entire lifecycle of a cyberattack was seemingly handled by one individual or group. In the spring of 2016, the group responsible for deploying the Samas ransomware was observed using the same exploit to gain access to multiple organizations—and following similar timing across those organizations regarding establishing a foothold, reconnaissance, identification of critical assets and deployment of ransomware. Something similar was observed regarding the Ryuk ransomware threat actor from September 2018 through the spring of 2019.
However, what the above images illustrate is specialization at the various stages of an attack—in particular, initial access.
IABs are threat actors whose goal is to gain access to organizations, and then monetize that access by offering it for sale. This allows for that specialization and isolation of skill sets (the hacker only needs to gain and maintain access), but also has the additional benefit of the payment being addressed offline, out of view of law enforcement.
Ransomware attacks are necessarily “public” in nature, in that some means must be provided to the impacted organization to make payment. By providing a cryptocurrency wallet, some information regarding the hacker’s infrastructure is exposed to law enforcement, who has developed significant skills in following such leads. However, by isolating the skill sets and phases of the attack cycle, IABs can receive payment for access to compromised organizations out of view of law enforcement.
MSPs remain an attractive supply chain target for attackers, particularly IABs.
On May 11, 2022, the Cybersecurity & Infrastructure Security Agency (CISA) issued a warning for MSPs and their customers, stressing that MSPs in multiple countries (including the United Kingdom, Australia, Canada and New Zealand) were likely being targeted because of their own access to their customer base.
What You Can Do
Here are some steps that MSPs can take to protect themselves and their customers:
- Basic cyber hygiene, such as patching systems, implementing MFA, network segmentation, implementation of “least privilege,” etc.
- Maintain an accurate asset inventory, not just of physical systems but also of running services, user accounts, etc.
- Reduce your attack surface—as part of your asset inventory, reduce your exposure by limiting what’s accessible
- Monitor your inventory and network for suspicious activity, with an eye toward detection and response
- Maintain and verify offline backups















