Finding malware on a computer stinks. It’s even worse when the payload is encrypted. In this blog, we’ll reverse engineer an encrypted Redosdru DLL to better understand the threat we discovered within our partner’s network.
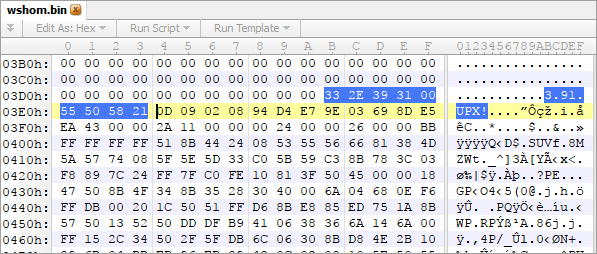
Lurking within the C:\Windows\System32 directory was a binary called “wshom.exe”. By manually inspecting the file’s header within a hex editor, we noticed it had been packed with UPX.
SHA256:e62d433e662bff743e8d0fc554c2308db6c72fa500e64091d76e127445f337e1
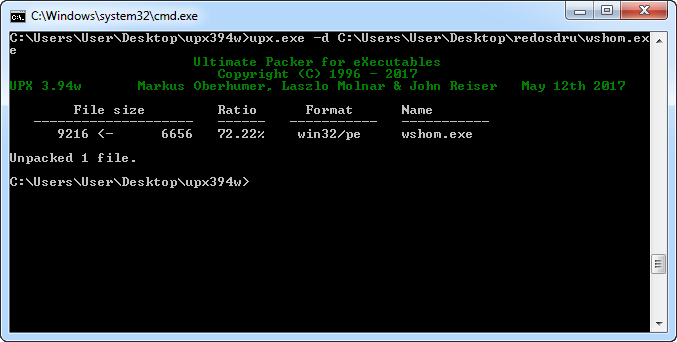
Using the free UPX software, we decompressed/deobfuscated wshom.exe with the “-d” argument.
SHA3256:3edfe93173f368fe5a29e0905fb17996584d4380b48e05b84fe56cc9aac090d1
With the raw PE, we quickly inspected the disassembly to determine what was going on under the hood. Almost immediately, we discovered several paths to a function which received a Base64 buffer and later downloaded a file.
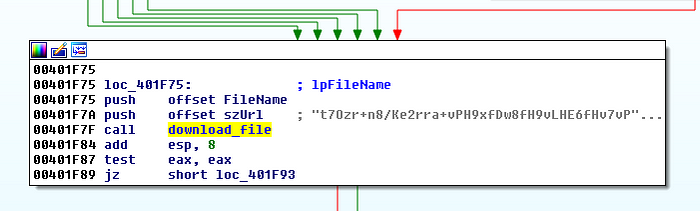
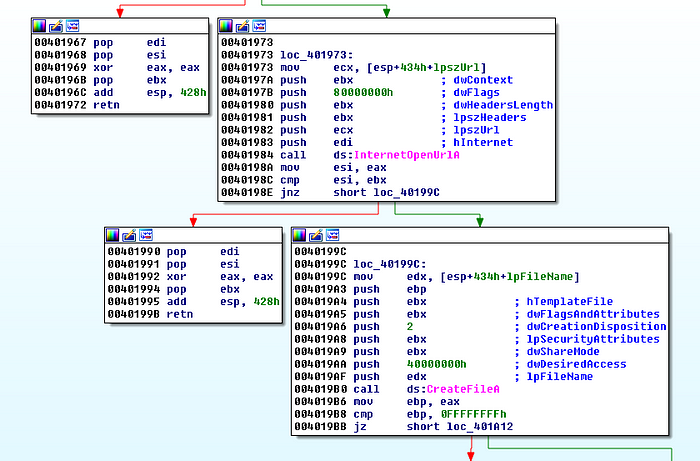
Rather than spend time stepping through with a debugger, we simply ran the executable and inspected wshom.exe’s strings in memory with Sysinternal’s Process Explorer.
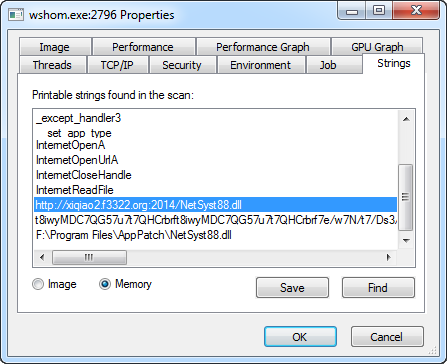
From here, it was obvious to see this was a dropper which fetched “NetSyst88.dll” from hxxp://xiqiao2.f3322.org over port 2014 and placed it within Program Files\AppPatch. We also verifiedd this with ProcMon and Wireshark:
Encrypting Payloads to Avoid Detection
With a hex editor, we noticed that NetSyst88.dll was missing the MZ and PE headers. This typically points to some sort of encryption/obfuscation routine which helps the malware author evade security products that inspect files on disk. After some online research, we concluded this DLL was related to the Redosdru malware family.
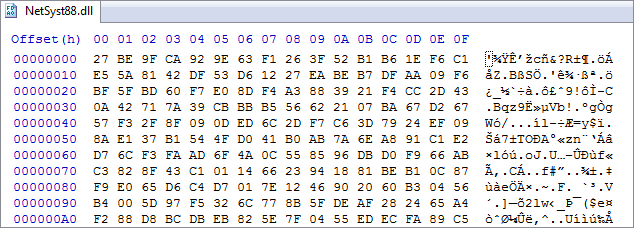
SHA256:3394755E45B6CBA8FD63160512A847533DE89CD88BD8EEC3251623E85F67E987
It was unclear how this encrypted DLL was being used and no other resources online documented this routine. So, we decided to take another look at what happened after NetSyst88.dll was downloaded. We learned that wshom.exex will check for files within Program Files\AppPatch and once that succeeds, it will call function sub_401DA0. Within this function, we saw how it loaded the string “Kother599” onto the stack and called a decryption routine.

Since the decrypted DLL was never dropped to disk, we had to set a breakpoint immediately after decryption to extract raw DLL from memory.
Decrypted DLL Capabilities
Now that we had a decrypted DLL, we were excited to see the purpose of the payload. After decompressing the UPX wrapper, it’s imports and exports gave us everything we needed:
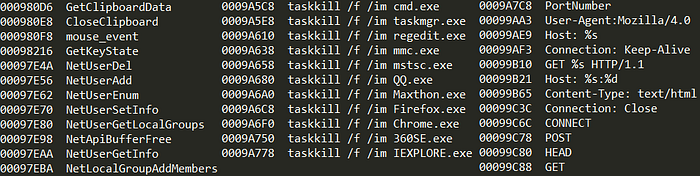
As we expected, the payload featured several features common in most implants including:
- Recording Keystrokes
- Managing Users and Groups
- Killing Programs
- Harvesting Clipboard Data
With this information, we were able to expertly advise our affected partner on the capabilities of their attacker, the risks to their client, and additional locations to inspect for malicious activity.
Ready to find hackers in your network? Sign up for our 21-day Free Trial
At Huntress Labs, we believe the best defense is a good offense. We’ve spent our careers circumventing preventive security products to stay a step ahead of malicious actors. This mentality enables our products and analysts to tackle threats head-on. As a result, we force hackers to earn every inch of their access within the networks we protect and monitor.















