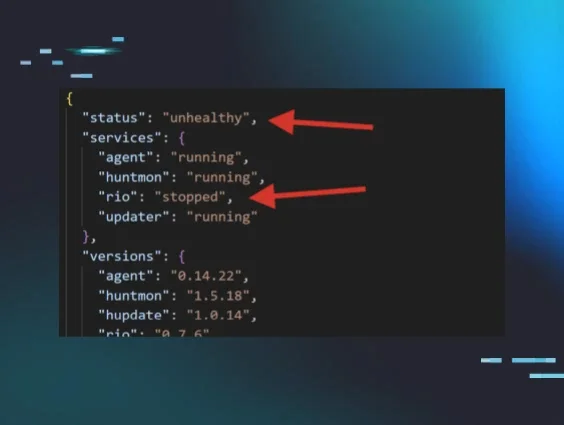
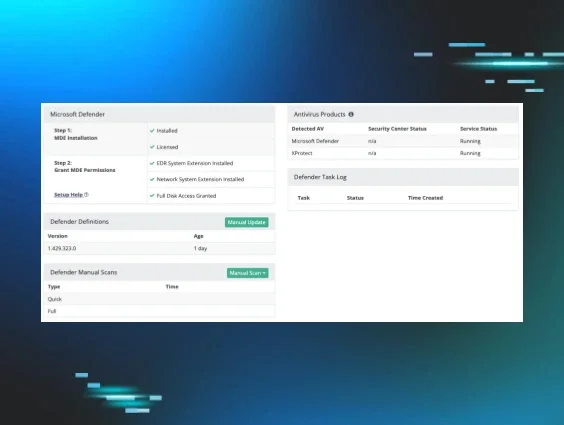
As hackers have become smarter and more sophisticated in their attack strategies, we’ve been watching, learning and evolving to help you face these new threats head on.
We’re excited to enter this last quarter of the year full steam ahead with 30+ new team members and our most robust features and ThreatOps support to date! But there’s a lot more to the story than just headlines. Here’s a rundown of the new capabilities, technology and talent we’ve unleashed as part of our recent platform enhancement.
Defenders, Assemble
To keep pace with today’s savvy threat actors, we went out and found the best minds in the cybersecurity industry—then we hired them. Some of our new faces include folks on our Product, Engineering and ThreatOps teams.
They’re people with vastly different backgrounds, including digital forensics experts, leaders with military cybersecurity experience (from the Department of Defense, US Coast Guard Cyber Command and Air National Guard), as well as industry leaders from Cisco and VMware. These diverse minds will enable us to continue to do what we do best, but better than ever: hunt hackers down.
We’re always on the hunt for passionate cyber professionals. If you want to roll up our sleeves and solve complex problems, join our growing team!
All together, we’ve got more than 100 years of combined cybersecurity expertise. With a world-class team at the helm, we’re writing a new story that’s going to redefine cybersecurity—and we’re starting with some impressive new technologies.
What’s New?
Managed Antivirus
You’re already using antivirus software, but are you maximizing its full potential? Using Microsoft Defender Antivirus, which is built-in to each Windows OS (and consistently ranked as one of the top antivirus protections), we now offer a rigorously beta-tested Managed Antivirus.
This service provides centralized insight into and management of all Microsoft Defender activities—including health, status, signature updates, exclusion settings and execution of remediation actions for all points at the account, organization and host level. Our ThreatOps team also provides expert assistance for incident analysis and any subsequent remediation steps to help you bolster your defenses.
Host Isolation (Beta)
As we all know, cyberattacks can and do happen—even when you have a layered cybersecurity strategy in place. To help increase your protection against untimely attacks, we’ve created Host Isolation, a new feature that’s currently in public beta.
This powerful capability allows you to isolate a host after receiving a threat incident report from ThreatOps. Host Isolation provides the ability to quickly block incoming and outgoing network activity on infected hosts—significantly reducing the chances of a network-wide cyberattack. During isolation, which can be triggered manually or automatically, the host will be isolated from the organization’s network—only allowing connectivity between Huntress and the isolated host. And once isolated, ThreatOps will provide you with assisted remediation steps to resolve the incident and get the host(s) back online.
24/7 Threat Hunting
Cyberattacks often occur at the most inconvenient times—and that’s no accident. Hackers and bad agents know that you’re most vulnerable in the middle of the night or during a holiday weekend. They don’t sleep—and now, neither do we.
Starting in October, we’ll be providing 24/7 threat hunting with coverage spanning from the US and Canada to the United Kingdom and Australia.
• • •
The cybersecurity landscape is evolving, and so should we. While enterprises can afford to throw everything but the kitchen sink at hackers, this simply isn’t realistic for the other 99% of businesses. Instead, we champion a more proactive and layered approach to cybersecurity—one that provides comprehensive detection and response at a cost-conscious pricepoint… and this is only the beginning. 😉
If you’d like to learn more about Managed Antivirus, Host Isolation, or ThreatOps, watch our on-demand webinar or read more details here. If you’d like to take a look under the hood, you can also start your free trial today!