Over the past month, the Emotet family of malware has re-emerged as a formidable piece of crimeware, thanks to its new self-propagation techniques (undoubtedly inspired by the success of WannaCry and Petya). As with many malware campaigns, Emotet takes advantage of simplistic but proven social engineering. This latest variant specifically disguises its payload in a seemingly harmless email from a familiar contact which eventually leads to a malicious Word document. Once it infiltrates a network, its “worm-like” capabilities are used to move throughout the environment virtually unhindered.
At Huntress Labs, we were able to closely examine Emotet while helping one of our partners, SinglePoint Global, remediate an infection at a client site. To gather ground-truth, SinglePoint installed Huntress on their client’s endpoints and quickly learned 16 of 20 computers were compromised with Emotet and Qakbot. Huntress discovered the infection by identifying the “footholds” used by the hackers to ensure their malware would continue running even if users logged off or rebooted their computers.
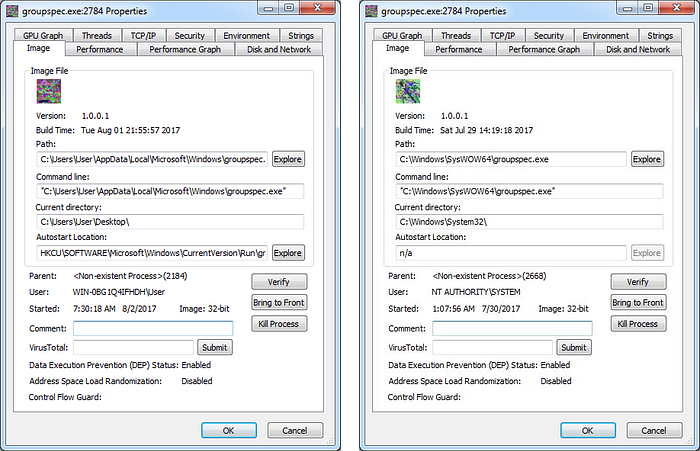
Given the infection levels of the initial 20 computers, SinglePoint deployed Huntress to the remaining 100 laptops, workstations, and servers owned by the client. Ultimately, we found Emotet on 99 of those 120 machines and the client was forced to dispatch an external incident response team to address the situation.
During the first 48 hours of the engagement, the incident response team attempted to use scripts and an AI-backed “Next-Generation” Antivirus to clean up the breach. Using Huntress provided data, SinglePoint was able to maintain control of the situation, guide responders to the compromised hosts, and contain/mitigate the problem.
What makes Emotet difficult to contain?
It starts with Emotet’s ability to regenerate newly encrypted payloads every few hours. How do you prevent something, after all, when it constantly alters itself? Many preventative security tools rely on inspecting specific characteristics and identifying known behaviors before a file is executed. But when those characteristics no longer apply or a threat takes on multiple forms, these methods can be rendered ineffective.
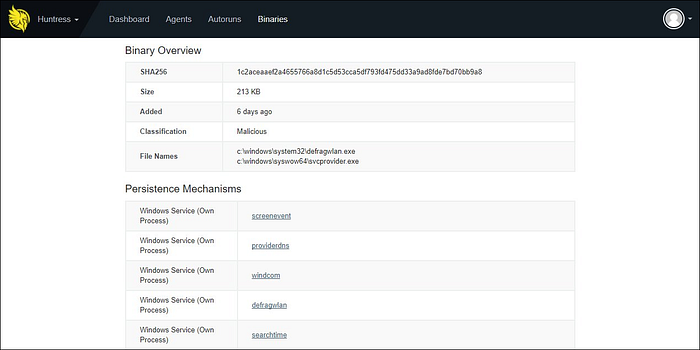
Huntress complements these products by uncovering the footholds hackers use to maintain access. Most of these footholds have been abused by attackers for over 20 years and largely remain unchallenged. For Emotet, this includes the use of malicious services and scheduled tasks used to automatically launch its payload and spread throughout victims’ networks.
Advice for mitigating Emotet and similar threats
SinglePoint Global promotes basic but “tried and true” cautionary steps to minimize damage. For starters, every local and domain administrator account should use unique and uncommon passwords as defined in NIST’s new draft guidelines. Emotet “carries” a password dictionary with 340 generic passwords, for example. Regardless of how unsophisticated those passwords are, the dictionary has still enabled Emotet to run freely within some victim organizations. This sort of thing happens when all of the administrator accounts use the same, “low hanging fruit” passwords. Strong passwords are a simple must.
Secondly, Singlepoint emphasizes how IT Departments must be vigilant in enforcing the principle of least privilege: admins should only have authorization for the systems that are required for their jobs. The more privileges are granted liberally and/or carelessly, the easier you make it for malware like Emotet to spread. It only has to compromise one account to pose as that admin over and over again and infect every machine that admin is authorized to access. And of course, regular users should never be given administrator privileges.
Parting Thoughts on this Breach
At Huntress Labs, our team preaches these “basic” steps while deploying our solution. Time after time, we’ve seen how solid security practices and around the clock monitoring contain and remediate troublesome threats like Emotet. As a result, our partners — like SinglePoint Global — discover and eliminate incidents before they damage their client’s reputation and disrupt their client’s productivity.
If you’re a Managed Service Provider looking to minimize customer downtime while protecting your profit margins, we’d love to partner with you. Sign up for our free 21-day trial and we’ll show you what’s already slipped past your preventative security stack.