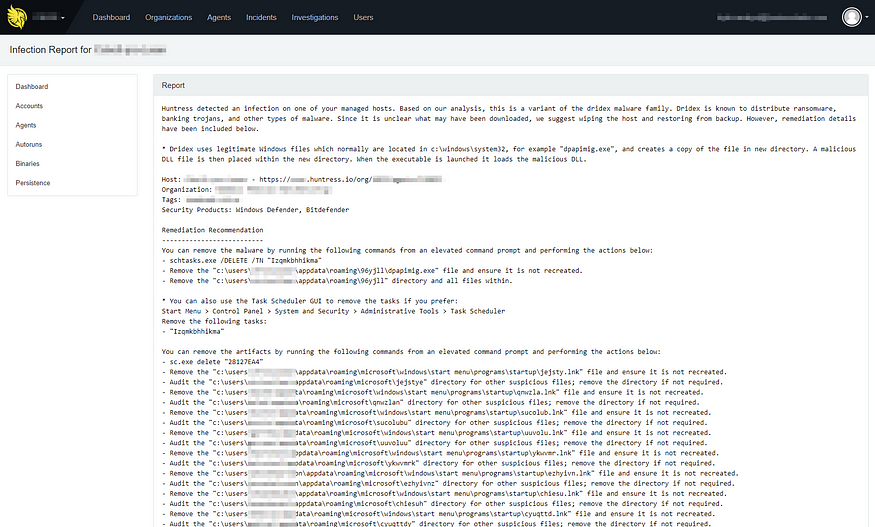
Long Story, Short: Huntress agents running version 0.7.85 and below will not be able to communicate with the Huntress servers after October 6th, 2018. We’ve already updated 98% of our partners’ agents, but need your help to eliminate old installers and the remaining 2% of outdated agents.
Read more to understand why this happened, what we’ve done to minimize impact to our partners, and what you may need to do.
Why is this Happening?
In mid-2017, several browser manufactures proposed and adopted plans to distrust SSL/TLS certificates issued from Symantec’s Certificate Authority due to a history of CA compliance and security issues.
As a result, these browsers will display errors that prevent users from reaching websites using these certificates.
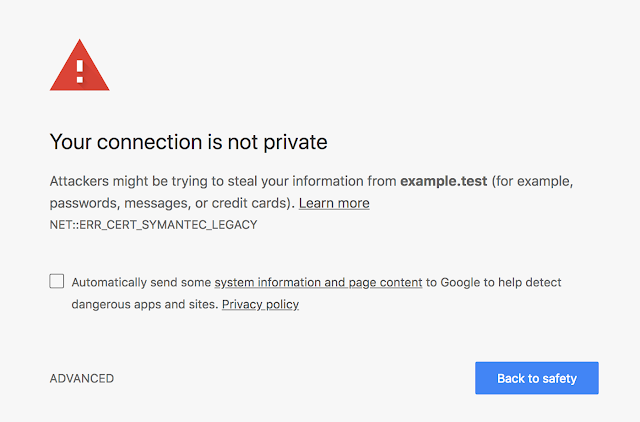
Impact to Huntress Partners
Our corporate and product websites have been protected with encryption since day one. Unfortunately, both of these sites used certificates issued by the Symantec reseller RapidSSL and will be impacted by these changes come October 2018. Thankfully, updating these certificates is a breeze and https://huntresslabs.com has already been migrated to a certificate issued by Amazon.
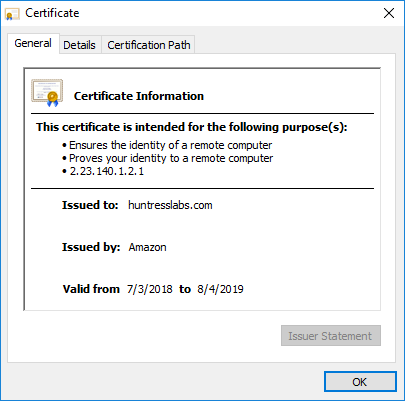
So What’s The Big Deal?
As offensive security experts, we take our partners’ privacy/security serious and implemented several anti-tampering features within our endpoint agent. One of these features is certificate pinning which helps prevent Man in the Middle attacks. Certificate pinning ensures your Huntress agents only accept tasking from and send data to legitimate Huntress servers.
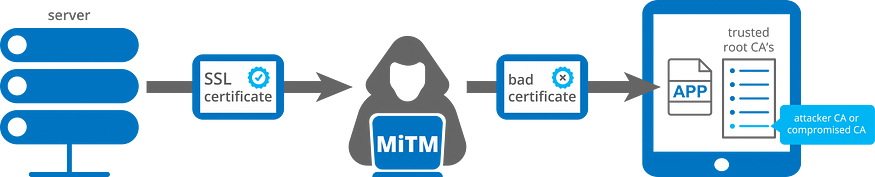
In order to support our new (non-Symantec issued) certificates, we had to release a new version of our agent that can accept this new certificate. To ease this migration, we started auto-updating Huntress Agents in June 2018 and 98% of our agents will not be impacted come October 6th.
What Needs to be Done?
To avoid any service interruptions, please configure your deployment software/RMM to use a Huntress installer newer than version 0.7.85. After October 6th, our servers won’t be able to communicate with old agents, let alone upgrade them.
Curious how to determine your installer version? Learn how here.
Forgot how to download our installer? There’s also a guide for that.
Want to see if you have outdated agents? We’ve added a feature to your Huntress dashboard to make this quick and easy.
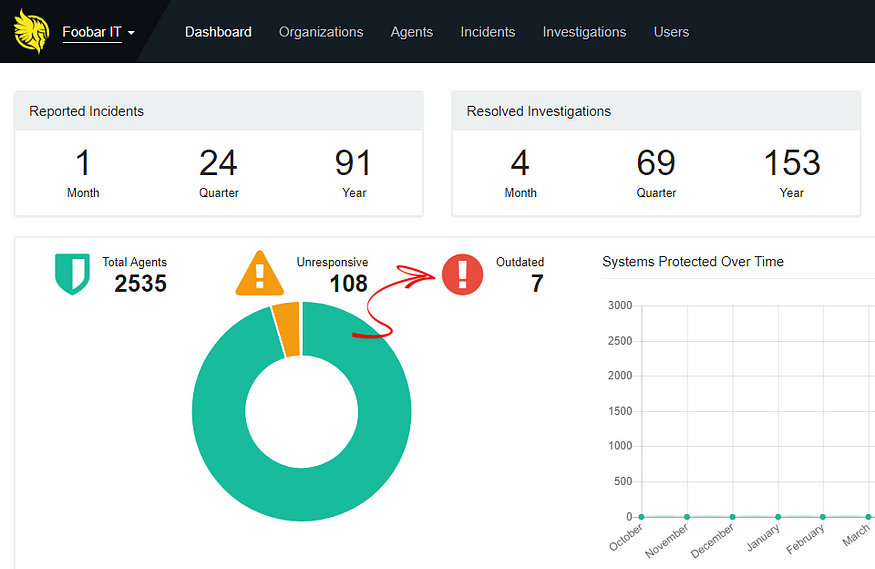
Wondering why your agent wasn’t auto-updated? There could be a couple reasons:
- It’s a laptop/workstation hiding in a storage closet without internet. Power on those puppies before it’s too late!
- The host’s hard drive was wiped/replaced but the agent wasn’t uninstalled. Jump into our dashboard and cleanup those unresponsive agents.
- It’s always possible antivirus quarantined the HuntressUpdater.exe. If you think you fall into this bucket, hit us up at support[at]huntresslabs.com so we can help you out!
Parting Thoughts
As always, thanks a ton for trusting the Huntress Team to protect you and your clients’ systems. If there’s any way we can improve this process, please share your critical or positive feedback!
Curious How You Can Help Huntress?
Hundreds of IT Departments and Managed Service Providers use Huntress to discover advanced attacks. Most learn about our offering via word-of-mouth. Do you know someone who could benefit from our offering? Tell them they’re missing out and point them to a free trial.