This week we had the opportunity to help an MSP partner contain and remediate an Emotet/TrickBot infection that impacted a client with 50+ computers and servers.
Considering how quickly TrickBot reinfects systems and drops ransomware, this was the perfect opportunity to kick the tires on our Assisted Remediation beta feature—which was designed to combat this exact scenario.
Keep reading for a play-by-play of how this incident unfolded.
Introducing the Situation
Network Titan’s day started out with a bang when Huntress detected TrickBot on 23 of 55 systems within one of their clients’ networks. This created a separate incident report for each host containing remediation details. Don’t get us wrong, our remediation steps are easy to follow. However in this case, time was of the essence and no one wants to manually clean 2019’s nastiest malware from 20+ workstations and servers. 😉
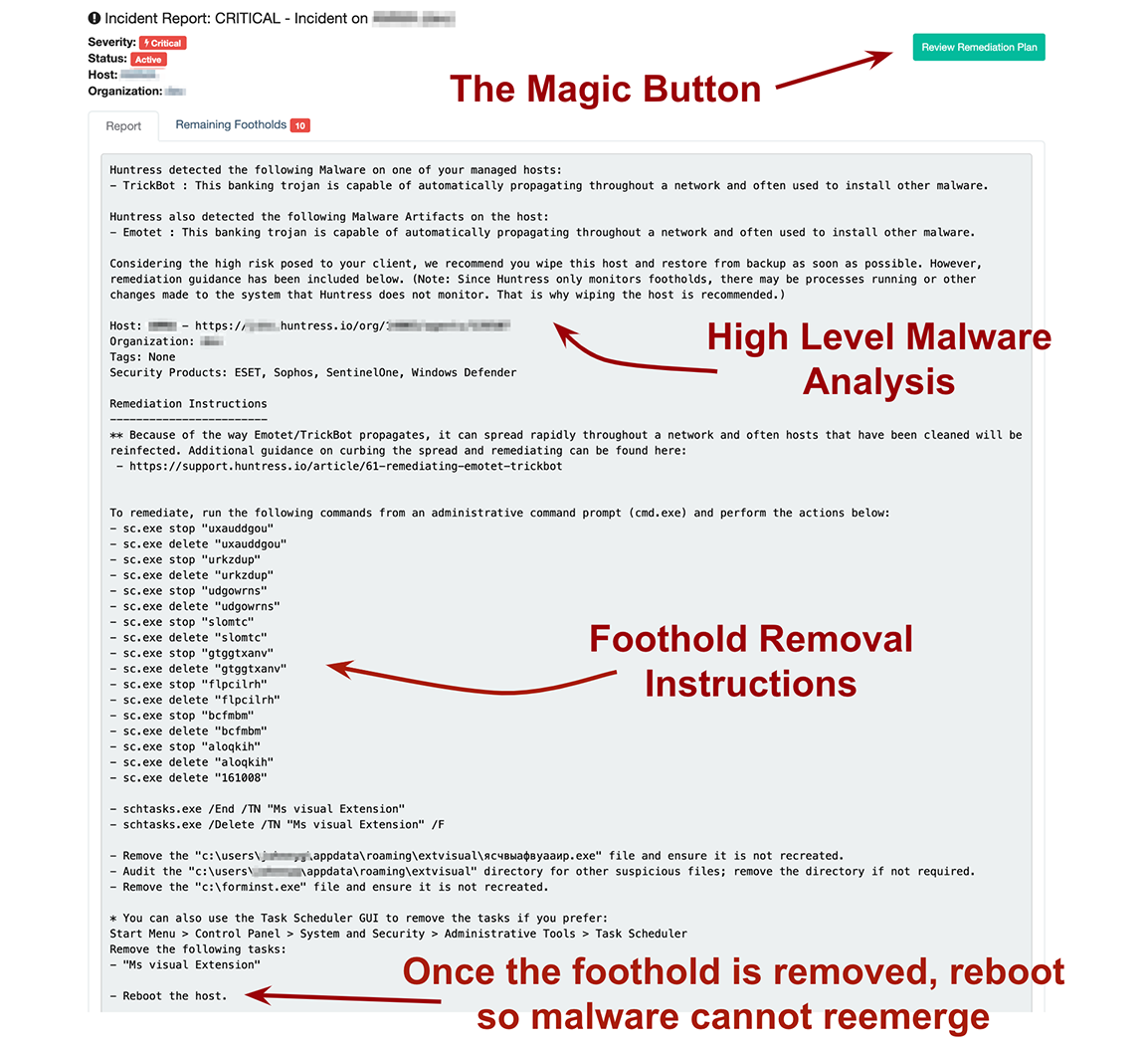
Knowing that Assisted Remediation was coming (we like to call it the “Magic Button”), it’s no surprise that their IT Services Manager, Chris Nolan, reached out to the Huntress SOC team for help.
Coordinating Preemptive Efforts
During the discussion, ThreatOps analysts agreed that our assisted remediation feature would help to quickly delete the malicious scheduled tasks, services, and files. However, we would still need the Network Titan team to disable Windows’ Administrative Shares (part of our existing mitigation guidance) and implement Software Restriction Policies to help prevent the malware from reinfecting newly cleaned systems.
While performing these actions, the Huntress Team upgraded all hosts with the beta agent and prepared remediation plans similar to the one below:
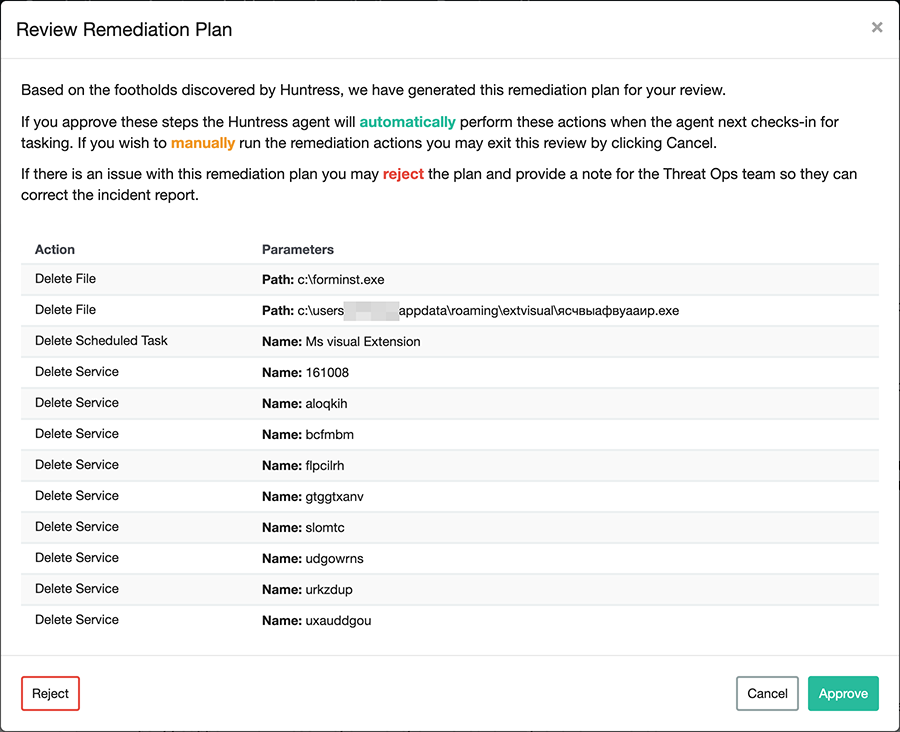
Executing the Remediation
Now with the upgraded agents in place, it was time to execute—our moment of truth! As soon as the remediation plans were tasked/approved, our team began rapidly mashing [F5], watching incident after incident flip from Active to Resolved.
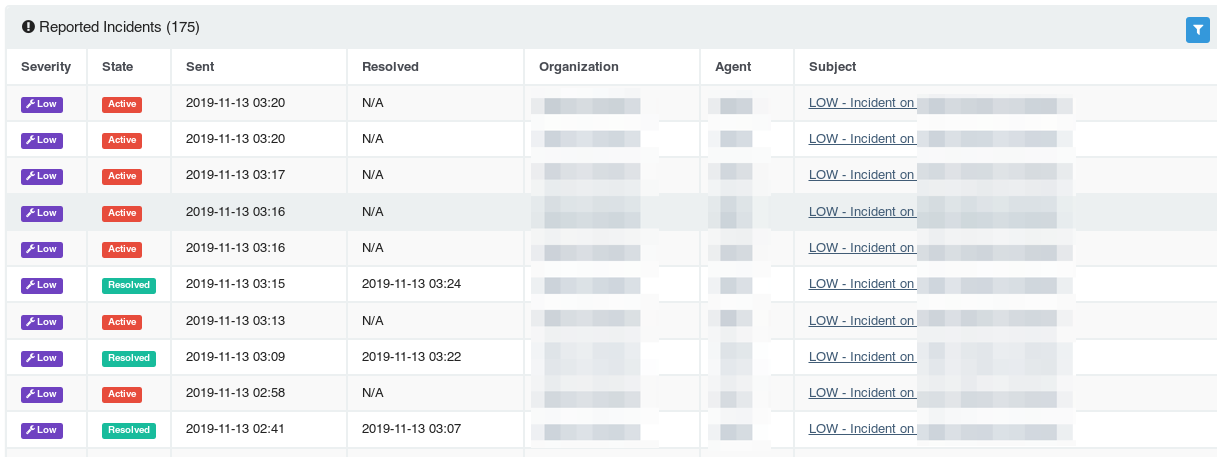
In under 20 minutes, Huntress and Network Titan were able to clean up 21 of the 23 infected hosts (two hosts were offline).
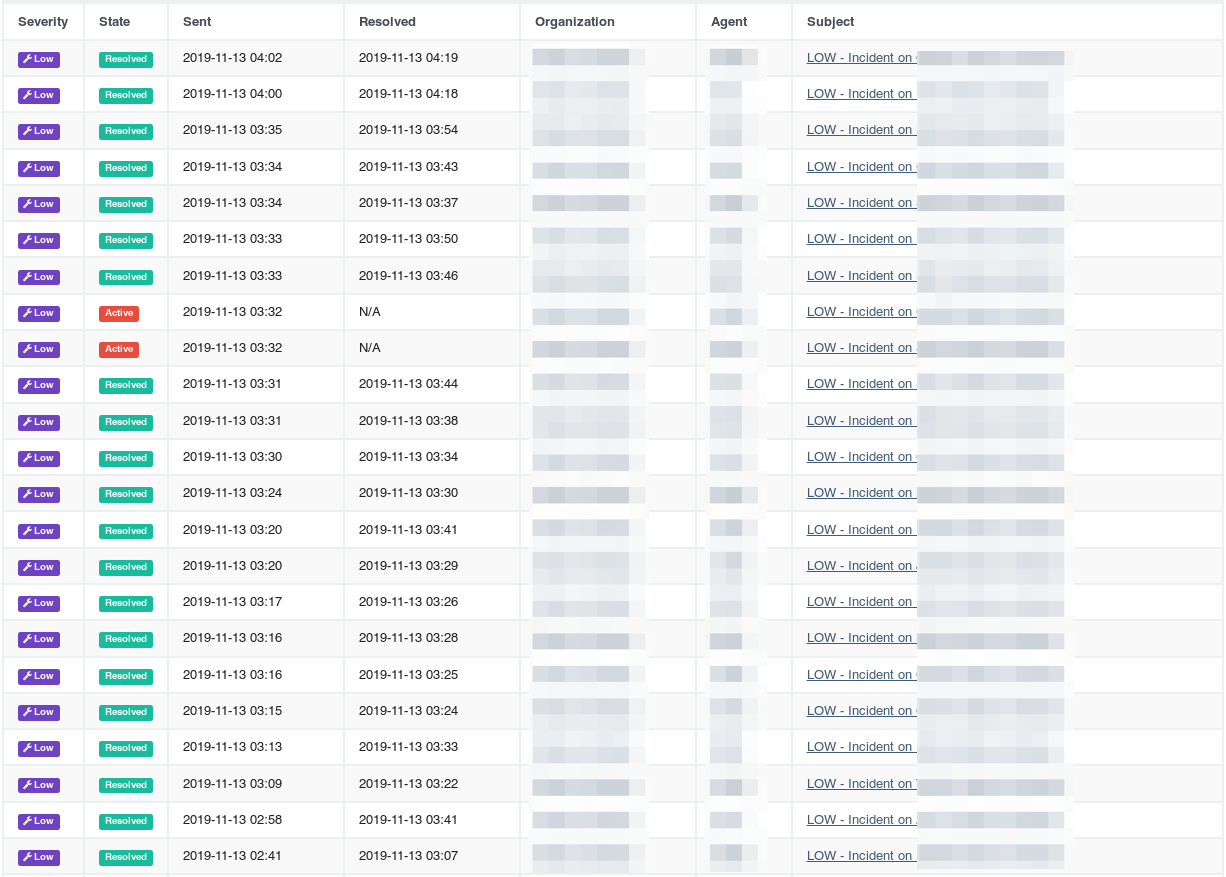
Once those two hosts were powered on, they also received the agent upgrade and Assisted Remediation tasks—resolving those machines as well. Needless to say, both teams were excited about the result.
Parting Thoughts
With Assisted Remediation, Huntress addressed our partner’s most pressing need: to quickly reduce the client’s level of risk posed by this incident without impacting productivity.
Although this cleanup effort still required work on our partner’s behalf (like rebooting machines to eliminate non-persistent payloads and re-enabling Administrative Shares), we’re pretty darn happy about this success!