There’s not a day that goes by where I don’t hear cringe-worthy stories of sales tactics peddling FEAR, UNCERTAINTY, and DOUBT (FUD) to close deals. Within the cybersecurity industry, it’s such a common practice you can find numerous pleas to “cut the crap”. See: Forbes, CRN, Help Net Security and Security Week.

As a technical founder of a product startup, I’m as anti-FUD as it gets. However, the past three years have taught me how education can be a snake-oil free alternative.
Demonstrate what’s actually happening to businesses in your prospects’ demographic and they will determine how it applies to their business and whether they will accept the risk. — Andrew Kaiser, Sales VP at Huntress Labs
With that said, this blog highlights a handful of examples that IT Departments and MSPs can immediately use to help their executive leadership or SMB clients understand the real-life risks faced by the company. If these incidents resonate, you’re now tee’d up for that sales discussion. From there, it is up to you to accurately convey the business benefits n̶e̶r̶d̶y̶ ̶t̶e̶c̶h̶n̶i̶c̶a̶l̶ ̶d̶e̶t̶a̶i̶l̶s̶ provided by a comprehensive security stack.
The Incident Backstory
A recently unsealed US indictment detailed how the GozNym cybercrime group was behind $100 million in damages. The hackers specifically infected victims’ computers with GozNym malware to gain access to and steal money from their online bank accounts:
Within this indictment was a list of 13 SMB victims. As I read each victim’s story, I couldn’t help but wonder how many of these businesses felt they were adequately protected or simply “too small” to be targeted by hackers. Unfortunately, their bank accounts now tell a different story:


Victim 1 — Asphalt & Paving Business
Full Story: Starts on page 20 of the indictment.

Useful Security Layers: Breach Detection, Multi-factor Authentication, Anti-spam, Anti-phishing Policies, Security Awareness Education, DNS Filtering, Antivirus
Victim 2 — Law Firm
Full Story: Starts on page 21 of the indictment.
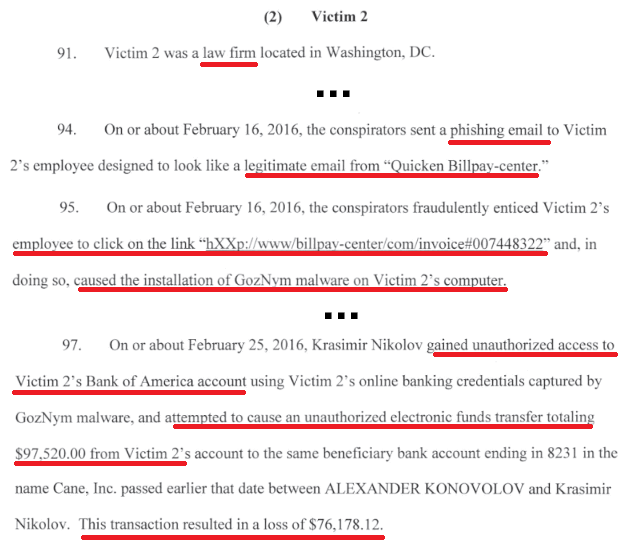
Useful Security Layers: Breach Detection, Multi-factor Authentication, Anti-spam, Anti-phishing Policies, Security Awareness Education, DNS Filtering, Antivirus
Victim 3 — Church
Full Story: Starts on page 23 of the indictment.

Useful Security Layers: Breach Detection, Multi-factor Authentication, Anti-spam, Anti-phishing Policies, Security Awareness Education, DNS Filtering, Antivirus
Victim 4 — Recreational Program
Full Story: Starts on page 24 of the indictment.

Useful Security Layers: Breach Detection, Multi-factor Authentication, Anti-spam, Anti-phishing Policies, Security Awareness Education, DNS Filtering, Antivirus
Victim 5 — Medical Equipment Distributor
Full Story: Starts on page 25 of the indictment.
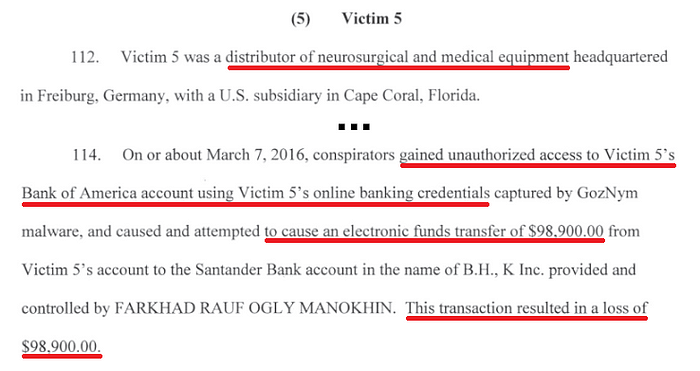
Useful Security Layers: Breach Detection, Multi-factor Authentication, Antivirus
Victim 6 — Furniture Business
Full Story: Starts on page 26 of the indictment.
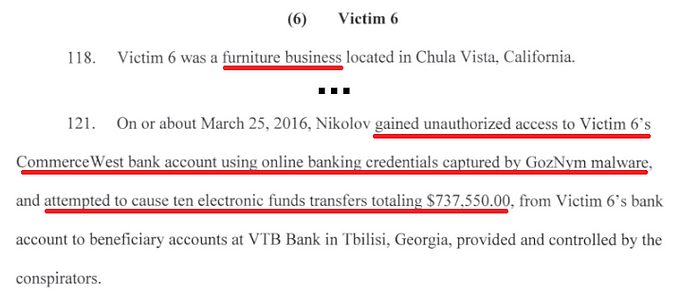
Useful Security Layers: Breach Detection, Multi-factor Authentication, Antivirus
Victims 7–13
Dive into the indictment to find several more of these stories ready to become awesome case studies and whitepapers!
Industries Affected: Electrical Safety Device Reseller, Contracting Business, Cold Pack Shipping Provider, Bolt Manufacturer, Casino, Thoroughbred Horse Breeder/Farm, and a Law Office.
Full Story: Check out pages 27–31 of the indictment.
Learn how to demonstrate these attacks!
There’s nothing better than showing prospects a live hacking demonstration. Join the Huntress team at DattoCon19 on June 17th in San Diego where we teach a no-FUD Hacking Windows course (only basic IT skills needed).


This course arms students with the skills to show how hackers gain initial access, evade antivirus, establish a persistent foothold, and exfiltrate sensitive data. In each lab, students use common exploitation techniques to compromise victim VMs. Sign up while space is still available!








